Spot the Phishing Attempt - Cybersecurity Awareness
The images displayed below are a combination of phishing emails and real emails depicting potential business email compromise scenarios. Spot The Phish! Click on the images to zoom in.
Spoiler Alert: Answers are below.
Answer: Image 2 and Image 4 are the real ones. And the rest are phishes. Take a look below…
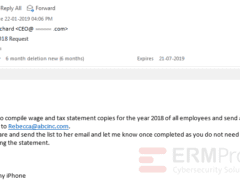
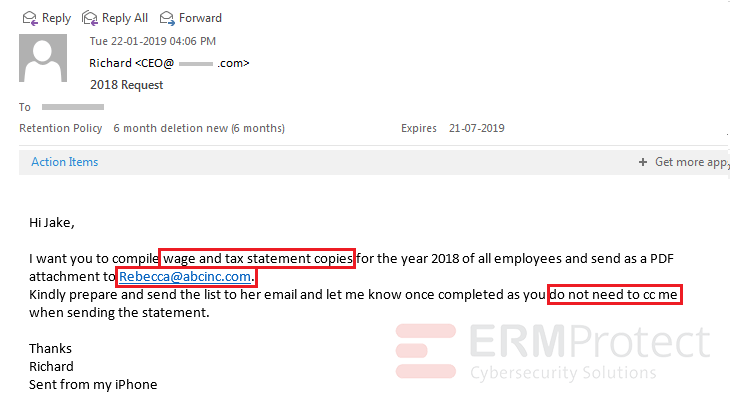
Image 1 details: The is an attempted phishing attack - the email asks for sensitive details of the employees to be sent to an external email address. Also, the sender tells the recipient not to “cc” him as by doing so the employee might send the email to the actual CEOs email address.
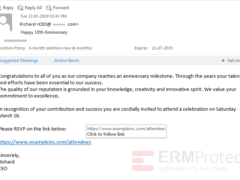
Image 2 details: With every email that involves a call to action, there is bound to be a link to click or an attachment to open. In this case, it’s a link which passes our typical cybersecurity check. We’ve used an example company (Example, Inc.). In typical phishing emails, the link text is different from the mouse-over text. In this case that is not an issue. It looks like the email is taking you to the legitimate exampleinc.com domain.
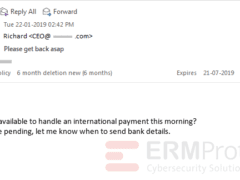
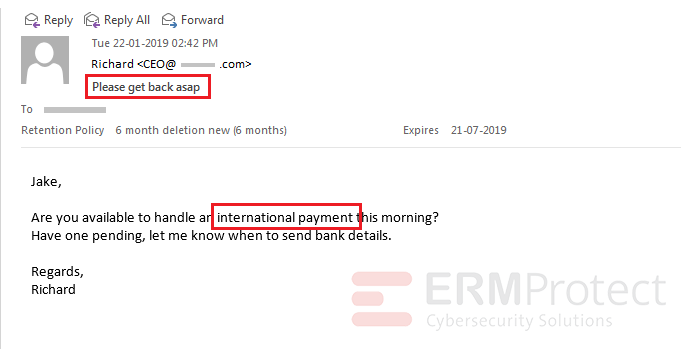
Image 3 details: The sender is creating a sense of urgency to get the recipient to act quickly to send an international payment. This one is a phishing email.
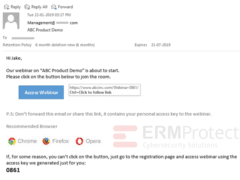
Image 4 details: The only thing we can really analyze in this case is the link. The link is a gotomeeting.com link which is a popular webinar hosting site. Although we should always have our cybersecurity guard up, there’s nothing manipulated in the link and it looks legit.

Get a curated briefing of the week's biggest cyber news every Friday.

Turn your employees into a human firewall with our innovative Security Awareness Training.
Our e-learning modules take the boring out of security training.
Intelligence and Insights

Are You Prepared for an AI-Powered Cyber Attack?

AI Privacy Risks