Spot the Phishing Attempt - Cybersecurity Awareness
The images displayed below are a combination of phishing and real websites. Spot the phish! Click on the images to zoom in.
Spoiler Alert: Answers are below.
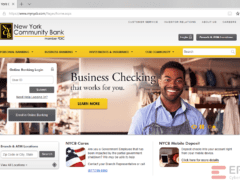
Image 3 is the only real one.
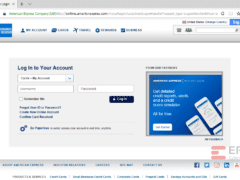
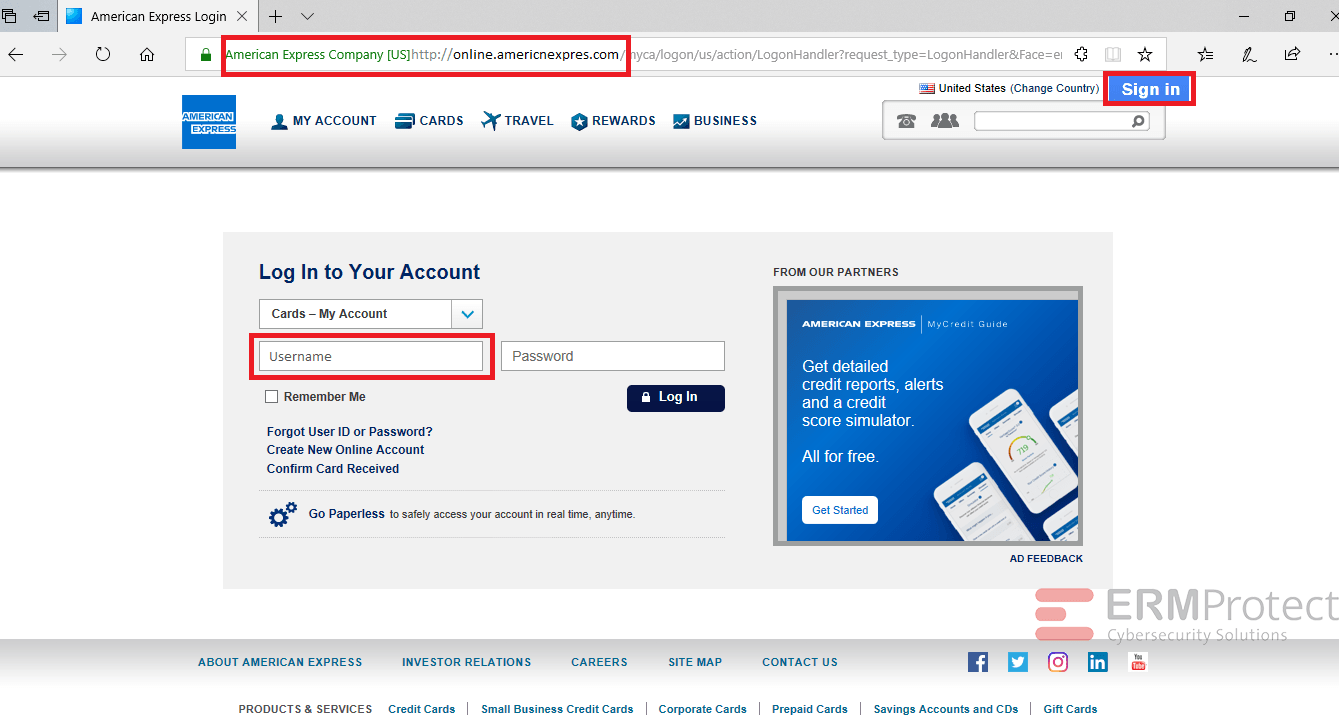
Image 1 details: The biggest sign of a possible phishing attack is that the URL is a phishy one. Further, American Express typically asks for a USER ID for login but it is changed to USERNAME and the ‘log in’ icon is changed to say, ‘Sign in.’
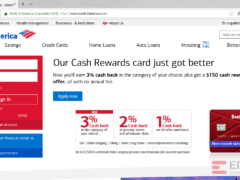
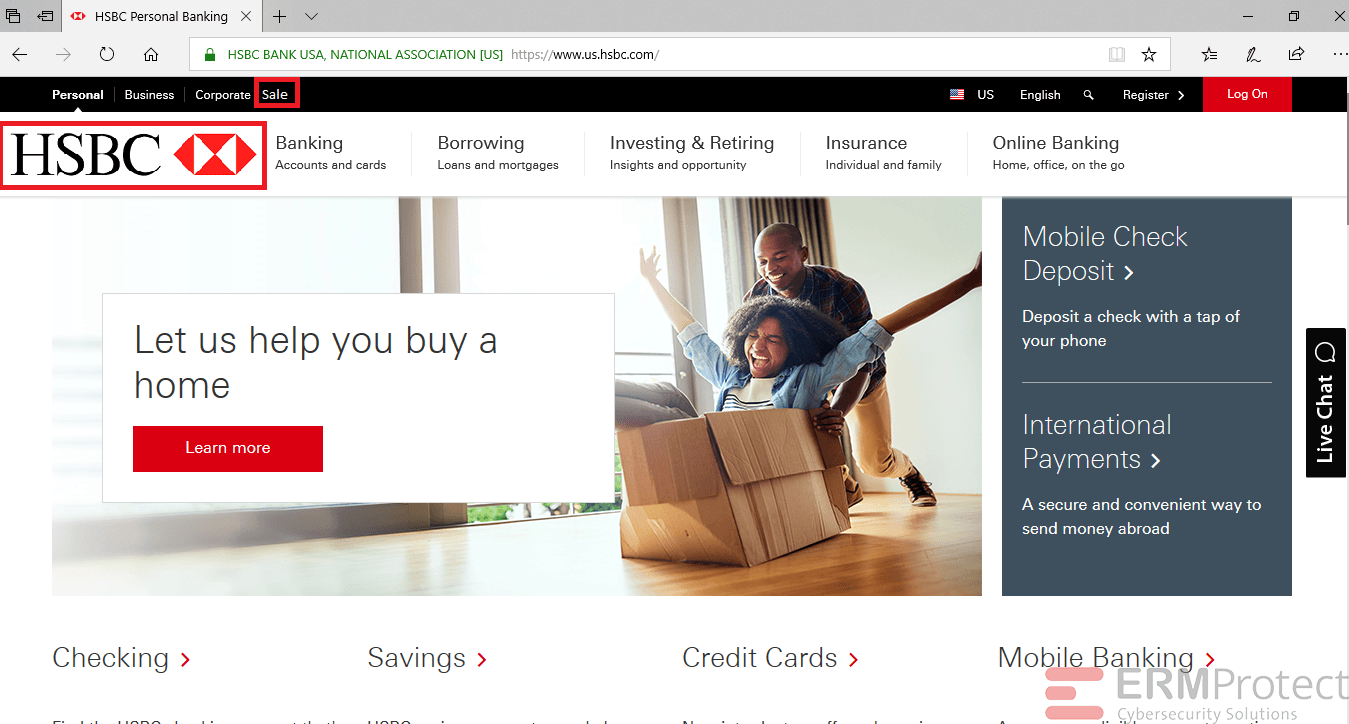
Image 2 details: The site has 3 misspelled words. In the page title, America is spelled as “Amrica.” Business and Option are clearly spelled wrong, as well. Definite cybersecurity red flags.
Image 3 details: There is nothing fishy in the URL. But, remember, even on websites that seem legitimate, always be cautious and have your cybersecurity awareness guard up, on the lookout for any behavior that digresses from the normal.
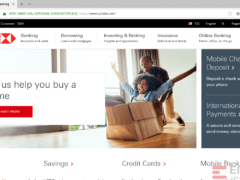
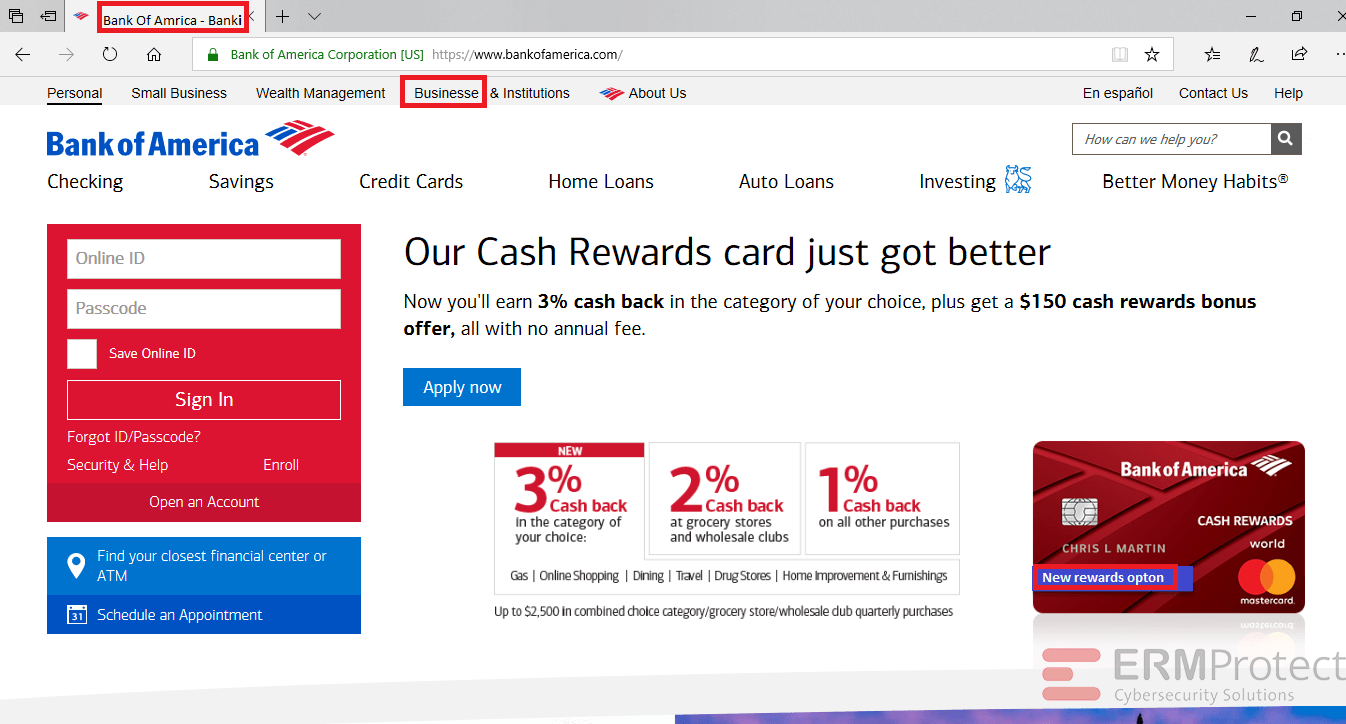
Image 4 details: Logo of the company is actually an old logo and there’s a ‘Sale’ tab on a banking site. It’s possible the hacker did a sloppy job, creating the site and attempted phishing attack in a hurry.

Get a curated briefing of the week's biggest cyber news every Friday.

Turn your employees into a human firewall with our innovative Security Awareness Training.
Our e-learning modules take the boring out of security training.
Intelligence and Insights

Are You Prepared for an AI-Powered Cyber Attack?

AI Privacy Risks