A Guide to the New PCI DSS Client-Side Security Requirements
By Rey LeClerc Sveinsson, PhD
By March 31, organizations that process, transmit, or store payment card data must be compliant with a significant update to new data security standards, known as PCI DSS v4.0. This revision aims to address the rapidly evolving landscape of cybersecurity threats, with a particular emphasis on bolstering client-side security - a critical but often overlooked aspect of online payment systems.
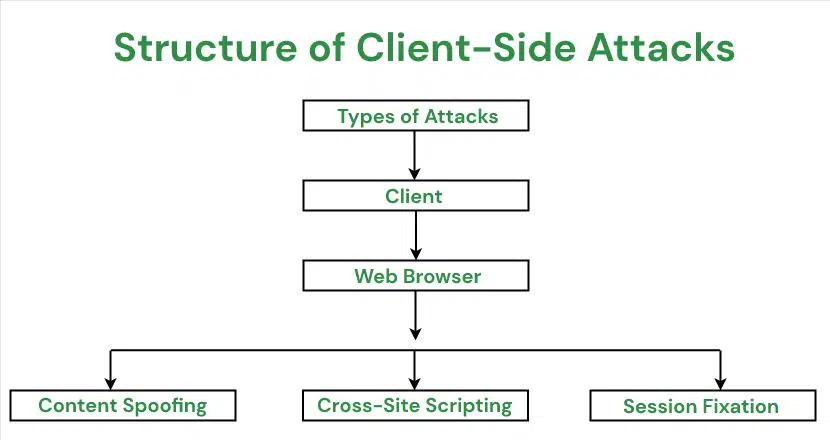
Client-side security refers to safeguarding the part of a website that interacts directly with users' web browsers, including the scripts and functionalities that drive smooth user experiences, such as payment processing, chat tools, and analytics.
The change was driven by a worrying trend - cyberattacks targeting the client-side of web applications have been rising steadily. Hackers have discovered that the client-side - because it involves external scripts from third-party vendors - is a weak link in many organizations' defenses.
These vulnerabilities can allow attackers to:
- Intercept sensitive data: By exploiting client-side scripts, attackers can capture personal information, payment card details, and login credentials during transactions.
- Alter the user experience: Through tactics like form jacking or clickjacking, hackers can manipulate the appearance and functionality of web pages to mislead users and steal information.
- Spread malware: Compromised scripts can deliver malicious software to users’ devices.
Getting a handle on client-side security will prove to be an instrumental part of any organization’s PCI compliance solutions heading into 2025 and beyond.
Breaches Highlight Need for Better Security
High-profile cases such as those affecting British Airways, Macy’s, and Ticketmaster have underscored the severe consequences of neglecting client-side security:
- British Airways: In 2018, approximately 380,000 customers had their personal and financial information compromised. Attackers injected 22 lines of malicious JavaScript code into the airline's website, skimming payment details during transactions.
- Macy's: In 2019, the retailer suffered a data breach where malicious code was injected into their online payment page, capturing customers' payment information during the checkout process. This attack was also attributed to Magecart.
- Ticketmaster: In 2018, the company experienced a breach where attackers compromised a third-party chatbot service used on its website, leading to the theft of payment and personal data from thousands of customers. Magecart was identified as the group behind this attack.
These incidents involved breaches where third-party scripts embedded on payment pages were manipulated to skim payment card details from thousands of customers.
The fallout included hefty regulatory fines, reputational damage, and financial losses for the companies involved.
Another driving factor for the update was the explosion in online commerce. Over the past few years, particularly during the COVID-19 pandemic, consumer shopping habits have shifted dramatically toward online platforms.
With more transactions occurring in digital spaces, the stakes for securing these environments have never been higher.
A single vulnerability in a client-side script could compromise thousands, if not millions, of transactions.
How PCI DSS v4.0 Addresses These Risks
PCI DSS v4.0 takes a proactive and comprehensive approach to addressing modern cybersecurity threats, particularly those targeting client-side security. Within this framework, Sections 6.4.3 and 11.6.1 stand out as pivotal in managing and safeguarding the scripts – small programs that that run on payment pages. These scripts, often developed by third-party vendors or embedded from external sources, play a crucial role in processing online transactions but also represent a significant vulnerability.
Section 6.4.3 focuses on ensuring rigorous oversight of these scripts. Organizations are required to maintain a complete inventory of all scripts operating on their payment pages. This inventory is not merely a list but must include written justifications for why each script is necessary.
Furthermore, the section emphasizes the importance of authorization - only scripts deemed necessary and secure are permitted to operate. To enhance security, scripts must also be verified for integrity, ensuring they have not been tampered with or altered in ways that could jeopardize data security.
Complementing these measures, Section 11.6.1 introduces mechanisms to detect unauthorized changes to payment page scripts. These mechanisms are designed to monitor for tampering or suspicious modifications, providing alerts that enable organizations to respond promptly to potential threats.
Early detection and rapid response are crucial in minimizing the impact of such changes, which could otherwise lead to data breaches or fraudulent activities.
Together, these updates represent a significant step forward in addressing the unique challenges posed by client-side security vulnerabilities. By establishing clear guidelines for script management, integrity verification, and threat detection, PCI DSS v4.0 equips organizations to proactively defend against cyberattacks.
This comprehensive approach not only enhances the security of online payment transactions but also builds greater trust with consumers, ensuring safer and more reliable digital experiences for all parties involved.
By addressing client-side security comprehensively, the update equips organizations to face modern cybersecurity threats head-on, ensuring safer online transactions for businesses and their customers alike.
Client-Side Security in Layman’s Terms
Think of client-side security as a virtual bouncer for your website. It ensures that every piece of code running in your visitors’ browsers is behaving as it should. It’s vital because websites often use external code – such as chatbots or analytics tools - which can inadvertently introduce vulnerabilities. If unchecked, these vulnerabilities can lead to data theft, malware attacks, and more.
Imagine this: a third-party script on your payment page is altered by cybercriminals. Without proper security measures, you might not detect this for weeks, exposing sensitive customer data. The result? Hefty fines, legal issues, and loss of customer trust.
Managing client-side security presents significant challenges for organizations, primarily because of the complexity and unpredictability of the external scripts embedded in websites.
These scripts, often provided by third-party vendors, play a vital role in enhancing user experience, such as enabling payment processing, chat features, and analytics. However, their external origin means their behavior is largely outside the organization’s direct control.
Vendors frequently update their scripts to introduce new features or fix bugs, and these updates can occur without the organization’s knowledge or proper vetting.
This lack of oversight creates an environment ripe for vulnerabilities, as even small changes to a script could introduce weaknesses that cybercriminals could exploit.
Lack of Monitoring Opens Door to Hackers
Another challenge is the frequency with which these scripts are updated. Modern websites often rely on multiple third-party and fourth-party scripts, each with its own update cycle. Tracking these changes manually can be an overwhelming task, especially for organizations that use dozens - or even hundreds - of scripts.
Without effective monitoring tools in place, organizations may fail to notice when scripts are modified or replaced, leaving them vulnerable to malicious code injections or other client-side attacks.
Unauthorized changes to scripts are particularly insidious because they often go undetected for extended periods. Cybercriminals can exploit this by injecting malicious code into legitimate scripts, allowing them to steal sensitive data, hijack user sessions, or deface content.
Since these scripts execute directly in the user's browser, traditional security measures such as firewalls or server-side monitoring may not catch the unauthorized changes. This means that by the time the breach is discovered, significant damage - such as data theft or financial loss – may already have occurred.
These challenges underscore the importance of having robust client-side security measures in place.
Organizations need tools and processes to maintain visibility into all scripts running on their websites, monitor changes in real-time, and ensure that only authorized scripts with verified integrity are allowed to operate.
Without such measures, managing client-side security effectively can feel like chasing a moving target, with potentially catastrophic consequences for both businesses and their customers.
Solutions to Tackle PCI DSS 6.4.3 and 11.6.1
Organizations seeking to manage client-side security and comply with PCI DSS v4.0 have several tools at their disposal, each offering unique advantages and challenges. One such tool is Subresource Integrity (SRI), which ensures that scripts loaded onto a website remain unaltered by comparing them to pre-approved versions through a process called hashing.
If a script’s hash value doesn’t match the approved version, it won’t execute, protecting the site from tampered or malicious scripts.
However, SRI can be cumbersome to manage in practice, as scripts are frequently updated by vendors. Each update requires generating and approving a new hash, which can be time-consuming and prone to human error. This complexity often makes SRI challenging to implement at scale.
Another option is the Content Security Policy (CSP), which provides a set of rules that govern what scripts can and cannot do within a website. By defining domains or sources from which scripts can be loaded, CSP creates boundaries for acceptable behavior.
For instance, it can block scripts from unknown or untrusted sources, reducing the risk of unauthorized code running on a site. However, CSP has limitations - while it can restrict where scripts come from, it doesn’t inherently verify their integrity.
Once access is granted, CSP cannot prevent a trusted script from being modified or behaving maliciously. Moreover, CSP policies can be difficult to configure and maintain, particularly for complex websites with numerous third-party dependencies.
The most advanced and comprehensive solution is proprietary script management systems, such as those offered by Source Defense. These platforms provide real-time monitoring and control of all scripts running on a website.
Unlike SRI or CSP, proprietary systems isolate third-party scripts in virtual environments, ensuring they cannot directly interact with sensitive user data or other website components. This isolation allows organizations to grant granular permissions, specifying what each script is allowed to do.
Additionally, these tools offer real-time insights into script activity, alerting security teams to unauthorized changes and potential threats as they occur. Proprietary systems streamline the management of client-side security by combining visibility, control, and automation, making them a powerful solution for businesses dealing with complex digital ecosystems.
While each tool has its strengths, the choice depends on an organization’s needs, resources, and risk tolerance. For some, the simplicity of SRI may suffice, while others may require the robust capabilities of a proprietary script management system.
Regardless of the chosen approach, investing in client-side security tools is essential to safeguarding online transactions and maintaining customer trust.
Why Prompt Action Is Essential
Delays in responding to security alerts can have costly consequences. Studies show it takes over 200 days on average to detect and contain breaches, during which criminals can steal sensitive data.
By implementing PCI DSS 6.4.3 and 11.6.1 early, organizations not only safeguard their businesses but also save millions in potential fines and losses.
PCI Compliance Solutions To Meet New Requirements
Meeting the compliance requirements of PCI DSS 6.4.3 and 11.6.1 can feel like a complex and overwhelming task for many organizations, especially given the technical depth and operational changes required.
However, the potential consequences of non-compliance far outweigh the effort and investment needed to meet these standards. Non-compliance can expose your business to significant risks, including massive fines, legal liabilities, reputational damage, and loss of customer trust.
A single data breach resulting from inadequate client-side security could compromise sensitive payment information, leading to financial and operational disruptions that might take years to recover from.
The good news is that by taking proactive steps and investing in robust PCI compliance solutions, organizations can not only meet compliance but also strengthen their overall cybersecurity posture.
Implementing security measures ensures that client-side vulnerabilities are addressed, some of them include:
- Comprehensive script management
- Real-time monitoring
- Tamper detection systems
Beyond compliance, these measures provide a competitive edge by building customer confidence in the safety and reliability of your online payment systems.
The clock is ticking, with the March 31, 2025, deadline for PCI DSS v4.0 compliance approaching faster than many realize. Delaying action could leave your business scrambling to implement changes at the last minute, increasing the risk of errors and oversight.
Acting today allows your organization to develop and execute a well-planned compliance strategy, ensuring a seamless transition to the updated standards.
ERMProtect for Your PCI Compliance Solutions
ERMProtect is a trusted leader in cybersecurity, offering comprehensive PCI compliance solutions to help organizations navigate the complexities of PCI DSS compliance, particularly the challenges introduced by v4.0. Our expertise ensures businesses meet requirements such as script inventorying, integrity verification, and real-time monitoring.
ERMProtect provides advanced tools for managing and auditing scripts, detecting unauthorized changes, and responding to threats in real-time. We also offer tailored security solutions, training programs, and ongoing support that empowers organizations to maintain compliance while enhancing their overall security posture.
By seamlessly integrating with existing systems and fostering a culture of security awareness, ERMProtect not only safeguards sensitive payment data but also strengthens customer trust and organizational resilience.
Our approach turns compliance into a strategic advantage, enabling businesses to focus on growth while staying ahead of emerging cyber threats.
Click here to learn more about our PCI compliance solutions.
About the Author
Dr. Rey Leclerc Sveinsson is an expert in Privacy and Data Protection, Information Security, and Technology Governance, Risk & Compliance (IT GRC). He has developed information assurance programs for major organizations globally during his career as well as serving as a Consultant for ERMProtect. He has a PhD in Information Systems and multiple master’s degrees in the areas of privacy, information technology, and cybersecurity laws.
Intelligence and Insights

Cybersecurity Blind Spot: Why Physical Security Is Now the Easiest Way In

Red, Blue, & Purple Teaming: Unified Strategy Organizations Can’t Ignore