The ABCs of Phishing
This guide is to walk you through everything you need to know about phishing, starting with what it is, the different types, common techniques being used and tips for prevention. If you are looking for specific information about a specific topic feel free to skip to the section you are looking for using the shortcuts below.
What is phishing?
Phishing is a type of social engineering that refers to attempts to extract personal information such as user names, passwords, credit card details and other information by impersonating a reputable entity or a known individual and making a request to the target. If the attacker is successful, they will then use the information to access accounts to transfer money, buy things, or other damaging activities including identity theft.
Phishing attacks attempt to stimulate emotions and call for an immediate action to lure the victim into giving away credentials or other information before taking a moment to analyze the message and question its legitimacy. Attackers use a variety of different techniques and are masters of disguising their attacks. In some cases, attackers will research their targets and use any personal information they find to increase the perception of legitimacy in the eyes of the victim; improving the attacks likelihood of success.
To stay safe from these cyber criminals, it is vital to know the different methods they use to be able to identify an attack.
The 3 Types of Email Phishing
1. Spear Phishing
What is spear phishing?
By far the most successful type of phishing, spear phishing targets specific individuals or companies by using fraudulent emails that are designed to appear as if they are from someone the recipient knows and/or trusts. The mission of the email is to have the recipient do something (click on a link, download a document, send login credentials, etc.) that the attacker cannot do to achieve their goal.
For example, the attacker may need a recipient to click on and visit a website that will infect their system. The attacker can create the malicious website and construct a legitimate looking email and even reference a “mutual friend” or a recent purchase the target has made but, they cannot infect the system without the recipient’s action.
There are two tactics for spear phishing emails that are dictated by the information the attacker is after.
- Mass Attack
If the attackers are looking for a foothold in an organization, they may gather as many email addresses they can find and send an email to each of them. - Targeted Data
If the objective is to obtain specific data, such as the names and addresses of customers, the attackers may only send emails to targeted individuals. In doing so, the likelihood of being detected/reported is kept to a minimum while the probability of finding the desired data from an infected system is high.
What does spear phishing look like?
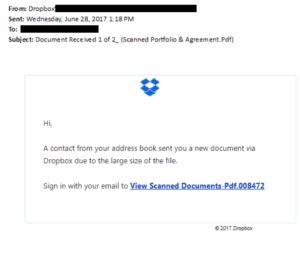
Below is an email that was sent to me, the addresses have been removed to keep the anonymity of both organizations.
The email address of the sender replicated this format, [email protected]. John is the name of a director at RealCompany. However, after visiting the website the email address listed for the director is [email protected].
The attacker is hoping that the targets that know John will not think twice about the address and assume the message was from John at RealCompany. Since the email appears to be automated there is no need for the attacker to attempt replicating John’s communication and writing styles; keeping the recipients suspicion low.
The “View Scanned Documents” button brings the recipient to an email sign-in page.
First of all, if we were sent a document over DropBox, why are we being brought to a Microsoft Office sign-in page? On top of that, why is the URL not login.microsoftonline.com and instead a very crowded and complicated domain.
The attacker is trying to extract the recipients log-in credentials. This could be to see confidential emails, use the account for other, even more targeted phishing attacks or for other malicious reasons.
See other examples in our Spot the Phish series.
Why does spear phishing work?
As the example above shows spear phishing emails work because they are believable. The attackers search the internet to gather as much information as they can on their potential targets. The bits of personal information give the email a lot of credibility. According to a Fire Eye report, spear phishing emails have an open rate of 70 percent while mass spam emails have an open rate of 3 percent. Additionally, 50 percent of those who open the spear phishing email will also open the malicious links.
The 2016 Q4 APWG Phishing Attack Trends Report shows that the amount of phishing attacks in 2016 was 65 percent higher than 2015. With spear phishing attacks increasing in volume combined with their high success rates, the data suggests that people are the weakest link in security. Since there is no silver bullet in Cybersecurity, businesses must use multiple, layered solutions to minimize their risk. As the old saying goes, a chain is only as strong as its weakest link. A proactive approach to fortify security and combat spear phishing is to conduct individualized cybersecurity awareness training for all employees to aid in identifying possible threats.
2. Mass Phishing
What is mass phishing?
This method is the most common type of phishing and as its name suggests, messages are sent to as many people as the attacker can find to extract their personal and/or financial information. These messages may ask for the recipient to download a file with malware, visit a malicious website or respond directly with personal information.
BYOD (“bring your own device”) is a popular concept being used by organizations, due to this, mass phishing is not only a threat on the consumer level but also a threat to businesses.
While some of the other methods rely on attackers researching their victims to succeed, the engine that drives mass phishing is volume. With no specific target in mind, the entity that the attacker impersonates (banks, credit card companies, government agencies, etc.) will not apply to everyone who receives the message. Resulting in only a small fraction of the messages being opened and even a smaller amount being executed.
What does mass phishing look like?
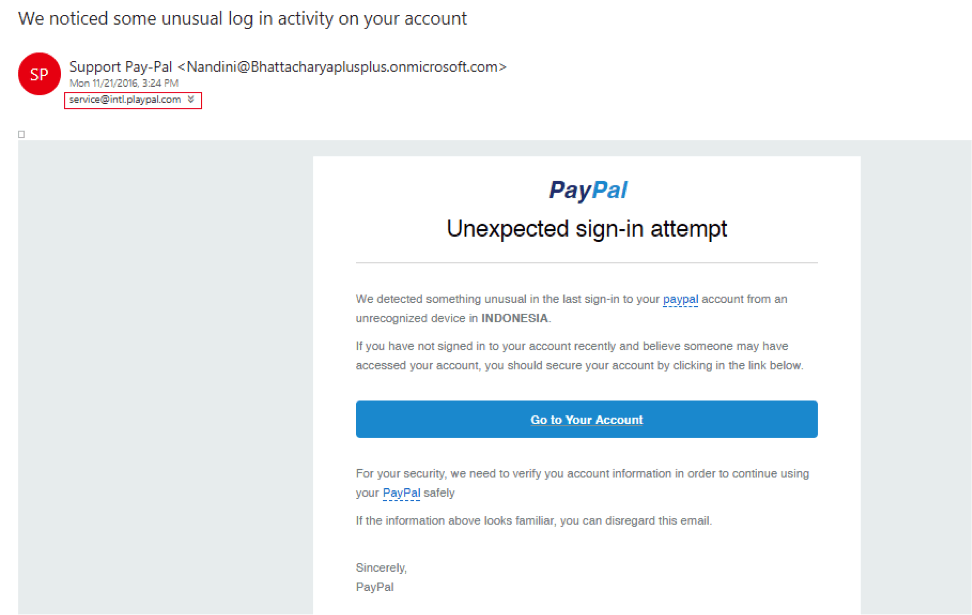
The attacker must decide which entity they will be impersonating. Below is an email that was sent to me in late 2016 where the attack decided to impersonate PayPal.
Ironically, the replica email claimed that my account experienced an unexpected sign-in attempt. The attacker poorly attempted to spoof the email address to look like the email is from PayPal or should I say PlayPal.
Before clicking on the link in question, mouse-over the link (do not click) and the tool tip will show you where the link is really taking you.
The “Go to Your Account” button contains a bitly URL address, which is a shortened version. For example, this link would bring you to our homepage: http://bit.ly/2uem2qf
To find out where a shortened link will take you visit www.unfurlr.com and plug in the link in question. This free tool will provide you with the real destination and a plethora of other information that may influence your decision to click on the link.
The destination for the link in the email was “webapps-sumarry.billgateways.com” (even though it is no longer working, do not visit) and the page looked like the PayPal sign in page.
Now, this was not the best phishing attempt (especially since I do not have a PayPal account with this email) but, it is not crazy to believe that this may trick an unsuspecting victim.
Why does mass phishing work?
Let’s say the attacker above had a list of 50,000 active email addresses.
If only 10 percent of the messages are opened and only 5 percent of the recipients who opened the message fulfil the request the attacker would have successfully gained access to 250 accounts. PayPal accounts can be linked with bank accounts, credit cards and contain other personal information.
Imagine you receive the email but you have never had a PayPal account; odds are you would delete the email and move along. Conversely, if you do have a PayPal account, you may be concerned and decide to investigate. You click on the link and the nearly identical log-in page opens, you fill in your credentials and then are redirected to your account page. There is no issue, which is strange but you are relieved so you move along.
What users miss is that the website recorded your credentials and in the background used them to sign you into the real site. Now the attacker has control and can do as they please.
The attacker isn’t trying to fool everyone instead, they are playing the numbers game; with enough emails sent there is bound to be a situation where the minor details of the email are overlooked and the desired data is successfully extracted.
3. Whaling
What's whaling?
“Whale hunting” is used as a metaphor for landing large accounts that can transform the business. Instead of acquiring business from a large organization, cyber criminals target valuable individuals such as CFOs, celebrities, politicians, or others with high valued credentials. The phishing attempts are extremely targeted and attempt to scare and convince the recipient into acting, like to prevent legal fees or to save their job.
Although whaling is uncommon it can be the costliest, if cybercriminals can successfully trick the large profile target they can gain access to confidential company information or take advantage of their esoteric resources. Facebook and Google fell victim to a phishing attack in which they wired over $100 million; it can happen to anyone.
What does whaling look like?
While other phishing scams may be designed to be from PayPal that attempt to frighten the recipient with claims that their account has been compromised. Whaling emails disguise themselves as the FBI requiring information, a C-level executive making a request or as an authority figure that the target is likely to serve.
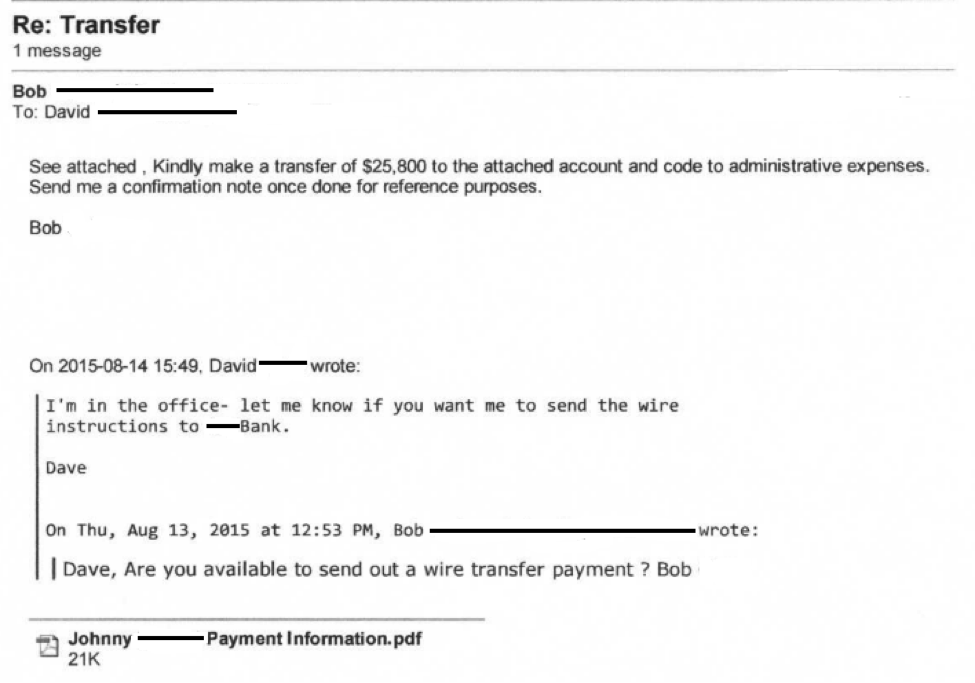
Below is a series of emails that was sent between the CFO and what appeared to be the CEO of the company. To keep their identities and company private, all identifiable information has been removed.
The email address of the sender replaced an “i” in the domain with the letter “l” in an attempt of going unnoticed.
The CEO told us that, “Dave, our CFO, has received several of these. They started after we began listing our staff members on our website. Interestingly, they only seem to arrive when I am out of the office. That might be a coincidence since I am out a lot but it is still interesting.”
Again, the little bits of information that attackers gather and use adds a lot of credibility to the email. In this case, Dave responsibly called Bob asking about the request before wiring the money.
Why does whaling work?
It works because they are believable. Although the targets for whaling are high-profile individuals it does not mean that they are experts in Cybersecurity.
Proactive tips to prevent falling victim to phishing emails
Implement several layers of defense.
The unfortunate reality with Cybersecurity is that there is not a single, catchall solution. Therefore, to mitigate these attacks, it is required to have multiple layers of defense. The goal is to make a successful attack extremely difficult by forcing the attacker to jump through as many hoops as possible.
Implementing firewalls, anti-spam software and filters, encrypting sensitive information, employee awareness training, and so on decreases the attacks margin of error, thus, creating more opportunities to identify and eradicate threats.
Below are several technology solutions to aid in preventing phishing attacks, however know that relying on technology alone is not a solution. The best defense are the employees themselves, making training the biggest change-bringer.
- Use effective firewalls.
Firewalls are the first line of defense against phishing emails. They are designed to protect private networks by preventing unauthorized Internet access, meaning that, all messages leaving or entering the private network must pass through the firewall. - Utilize anti-spam software.
This type of software has a variety of functions that are designed to protect the users from various threats. Although spam filters are not perfect and will not catch everything, they will identify and remove a good amount of phishing emails that would otherwise end up in an inbox, thus reducing risk, making anti-spam software an effective layer of defense that is essential to protecting organizations from phishing attacks. - Implement encryption.
Any email that contains sensitive information should be encrypted. Doing so reduces the potential damages that phishing attacks can have. - Keep systems and software up-to-date.
Whenever available, update your firewalls, spam filters, anti-virus, and malware detection and ensure that your systems have the latest security protections and patches. They often include bug fixes and new features that will help mitigate new types of threats. Otherwise, you run the risk of attackers taking advantage of known exploits and deficiencies of the outdated version. - Create a security culture.
Technical solutions are only half of the puzzle, the other half being human behavior. The board and executives should create a meaningful security culture by constantly reinforcing cybersecurity awareness and best practices to all members of the organization. - Educate employees.
Implement a cybersecurity awareness training program to give employees the information necessary to identify potential threats they may encounter. The program should include clear company procedures for employees to take once a threat has been identified. - Stay updated on the latest phishing attacks.
Cyber criminals are constantly devising and creating new phishing methods. Keep an eye out in the news for different phishing scams and relay the information to employees. Avoid being the latest victim by being aware of the emerging threats. - Measure the success of your security awareness program.
Doing so will aid in identifying individuals who need additional training and will keep security top-of-mind throughout the organization.
Other Common Phishing Methods
In addition to phishing emails, attackers try to trick us by using communication channels on our phones. When compared to email phishing, the following two methods are not as common but, they can be just as damaging.
Being aware of the scams to be able to identify and react to an attack when you, or your organization becomes the target.
Vishing
What is vishing?
Voice phishing – or vishing – is conducted over the telephone and like the other types, attempts to trick people into giving up personal information or their money. Like mass phishing, vishing is a numbers game. Attackers cast a wide net by calling every phone number they can find to maximize their returns.
Attackers will typically spoof their caller ID to alter the incoming call to appear as if it was coming from a legitimate or known phone number. With Voice over Internet Protocol (VoIP) services, spoofing a phone number is easier than ever. Some providers even allow users to configure the displayed number on the provider’s configuration webpage.
What does vishing look/sound like?
Vishing is different; it requires the listener to make decisions in real time instead of having the time to analyze and verify the legitimacy of the message.
Messages designed to stimulate emotions – such as fear or excitement – combined with processing verbal information leaves the listener scrambling to organize their thoughts. Thus, creating the ideal opportunity to be taken advantage of.
It is common for the attacks to begin with a prerecorded message that will:
- Introduce themselves as being from an authoritative organization
- Alert the listener about an issue with their account or payment
- Ask the listener to press a specified number to resolve the issue
From there, either a prerecorded message or a real person will ask for the listener’s Social Security number, bank account information, or any other form personal information to “authenticate themselves.” After the attacker has extracted all the information they were looking for, they will either drop the call or transfer the call to the actual support line.
This was just an example and there are many variations and methods.
Tips to avoid falling victim to a vishing attack
- Be suspicious of unknown callers.
People should be just as skeptical of a phones call asking for personal information as they are of an email asking for personal information. - Don’t trust caller ID.
Even if you recognize the number, remember that they can be easily modified to display the number of a legitimate organization. - What if the phone call is real?
After receiving an unsolicited phone call, it is important to proceed with caution. Before giving away any personal information be sure to ask the caller questions that someone in their position should know.
If your bank is calling, ask them for your account number. The person calling should have that information readily available. Regardless if the individual provides the correct information, you should tell them that you will call them back in a moment. From there you will be certain that you are talking to an employee of the company in question and can ask about the previous call.
Block all automated called to reduce your vulnerability from vishing scams.
This can be done by visiting the National Do Not Call List Registry. Plus, who wouldn’t mind a few less automated calls?
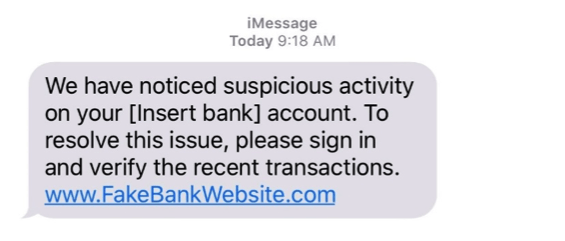
SMiShing
What is smishing?
Smishing is short for SMS phishing. Attackers send text messages with the intent of deceiving the recipient into giving out their personal information or to download a harmful virus onto their mobile phone.
With BYOD (“bring your own device”) increasing in popularity, smishing has become a threat to businesses in addition to being a consumer threat.
What does it look like?
Like the other types of phishing, smishing plays on emotions to trick the recipient.
Smishing messages may use fear by claiming to be from the IRS, your bank, or another service giving notification of an urgent issue.
Other messages use excitement and hope by claiming to be someone you gave your number to at a bar or that you won a prize. Attackers are creative and are always trying to come up with new angles.
The goal is to have you click on a link or reply with your personal information.
Why does smishing work?
Most people are aware that there are risks in clicking on links and downloading files from an email while on their computer. However, people often overlook these risks when they are on their smartphone, especially when in the form of a text message.
Tips to avoid falling victim to a SMiShing attack
- SMiShing scams usually begin with a pressing call to action.
If you receive a text message alerting you of an urgent security alert or an act-now or miss out proposition, ignore and delete the message. - Do NOT send personal, private or financial information via text messages.
- No financial institution will send you a text message asking for your account information.
If you have any concerns about your account, contact the institution via their website or their listed phone number. - Never click a link or reply to message from an unknown sender that you are unsure about. Simply don’t respond and delete the message.
- Look at the number the message is coming from.
Keep an eye out for phone numbers that do not look like traditional 10-digit mobile phone numbers. Attackers often use email-to-text services instead of their real phone number to conceal their identity.

Turn your employees into a human firewall with our innovative Security Awareness Training.
Our e-learning modules take the boring out of security training.

Get a curated briefing of the week's biggest cyber news every Friday.
Intelligence and Insights

Are You Prepared for an AI-Powered Cyber Attack?

AI Privacy Risks