How to Prepare a Self-Assessment Questionnaire (PCI SAQ)
A PCI Self-Assessment Questionnaire (PCI SAQ) is a merchant’s statement of compliance with Payment Card Industry standards, a requirement to process credit and debit cards. The questionnaire includes a list of security standards that businesses must meet to securely process Payment Card brands, including Visa, Mastercard, Discover and American Express.
By accurately filling out the PCI self-assessment questionnaire, merchants demonstrate that they are implementing the security measures needed to protect sensitive cardholder data from exposure.
However, many organizations struggle to figure out how to fill out the SAQ. First, they may not fully understand the complex Payment Card Industry standards. Second, they may have adequate in-house IT knowledge to understand if their security controls truly measure up.
Mistakes can lead to data breaches
Based on our experience, a leading cause of data breaches in small and medium-size firms is their failure to put in place required security controls specified in the SAQ – even though they have attested in the SAQ that these are fully implemented. The temptation to treat the self-assessment as a “check off the box” exercise comes back to haunt businesses when a breach occurs. It’s then glaringly obvious that the merchant misrepresented their security posture.
So, how does an organization avoid this mistake?
Some organizations elect to hire a firm like ERMProtect to assist them in filling out the SAQ. Many cybersecurity firms, like ERMProtect, employ Qualified Security Assessors. who understand IT security and the PCI standards and the technical measures needed to comply with them. Accredited and tested annually by the Payment Card Industry Security Council, they have both the technical and data compliance expertise to validate security for companies processing, transmitting, or storing payment card data.
However, it’s not always necessary or financially viable to go outside the organization, especially if you have a strong in-house IT resource. But remember - it is not enough for this person to be IT savvy. They must be IT security savvy.
Steps to filling out an error-free SAQ
-
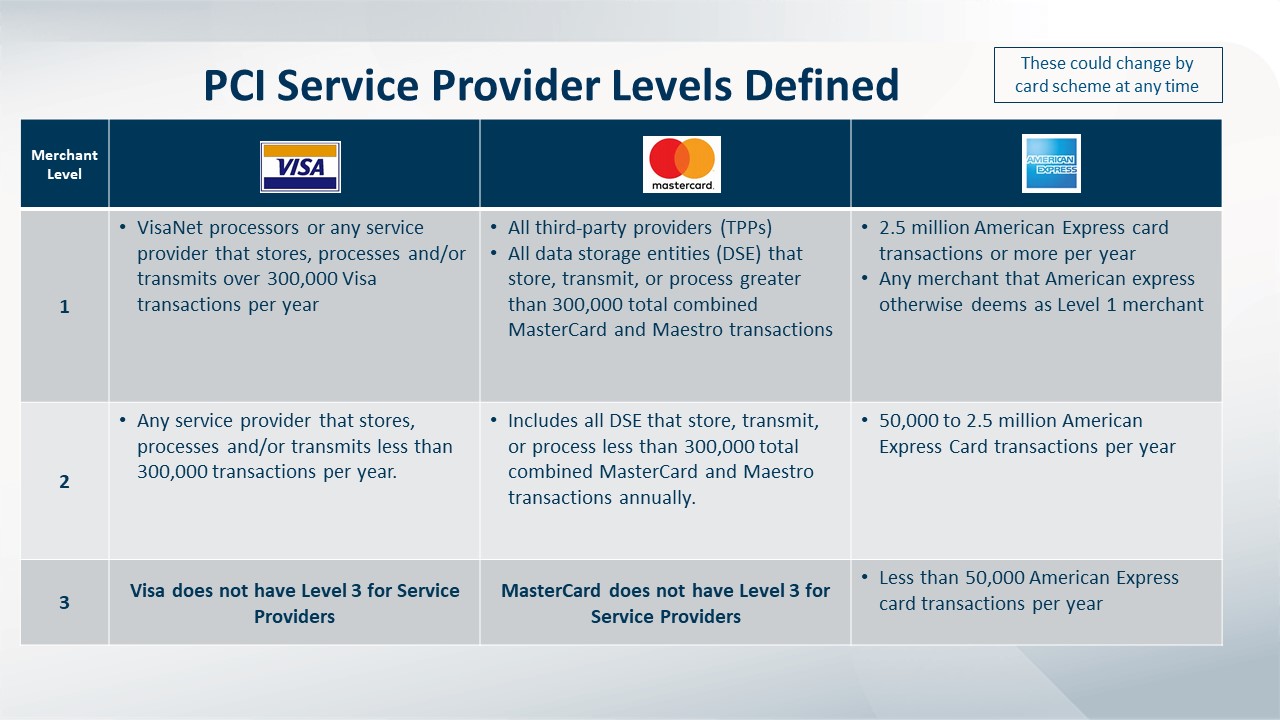
Determine Your Merchant or Service Provider Levels (based on volume of transactions).
Depending on your annual volume of transactions, your organization will be categorized as Level 1, 2, 3 or 4, with Level One representing an organization with the highest volume of transactions and, therefore, highest level of compliance demands. See Table 1 and 1.2 for guidance on how to determine your compliance Level.
Click to enlarge.
-
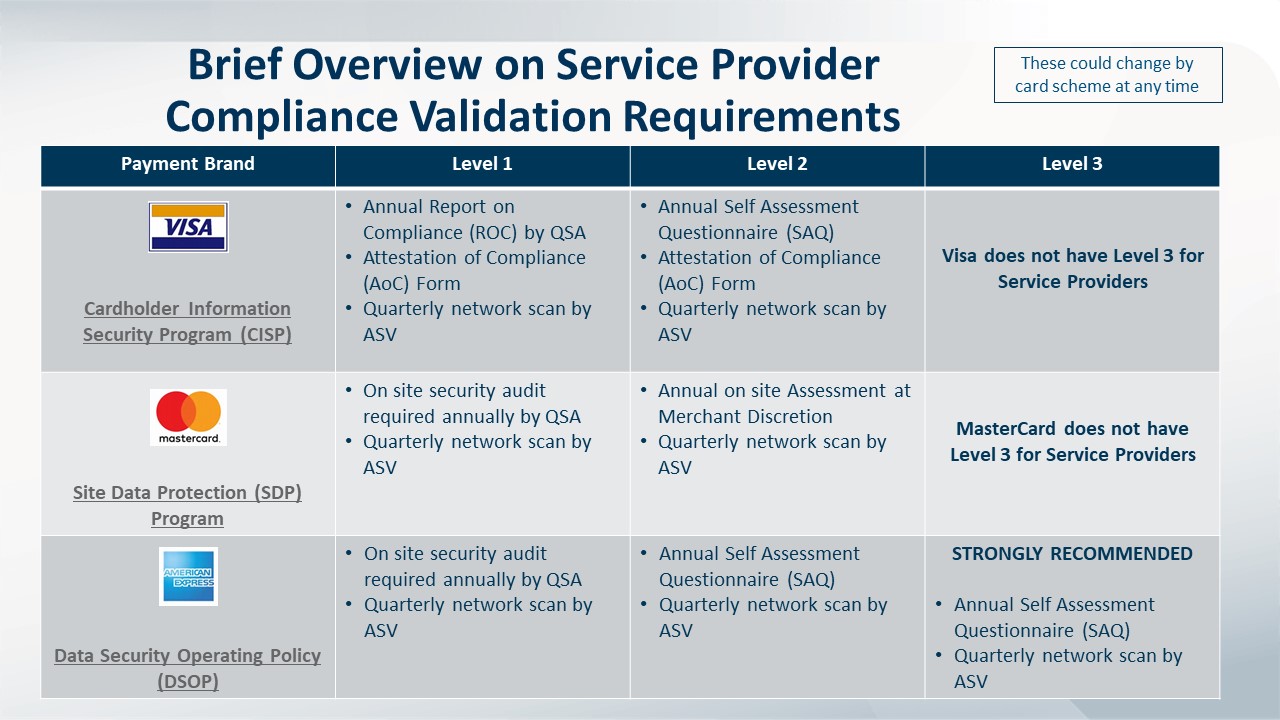
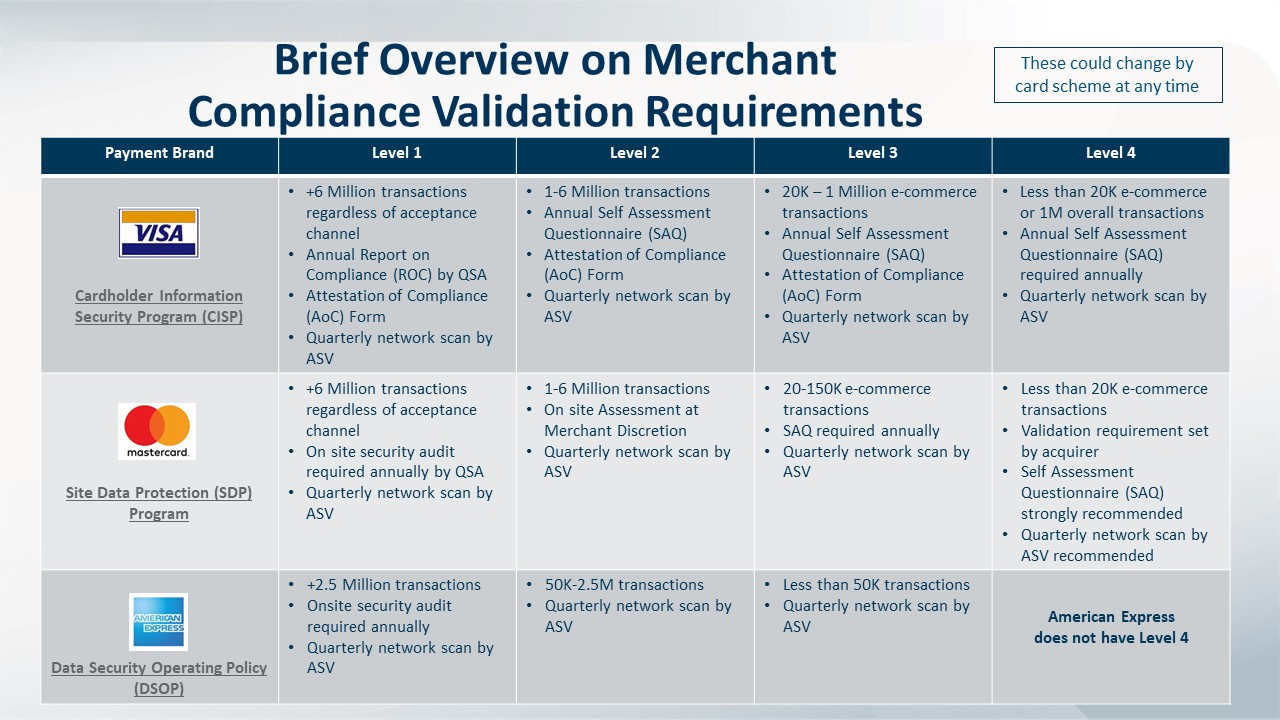
Determine the Compliance Requirements for Your Level.
The fewer transactions you process annually, the lower the requirements and vice versa. See the validation requirements for merchants and service providers below. Generally speaking, merchants that process fewer than 6 million transactions a year, will be required to:
-
- Conduct quarterly scans of their external networks to ensure security
- Fill out the SAQ
- Complete an Attestation of Compliance certifying that the organization’s required controls are in place
Click to enlarge.
High volume merchants (Level 1) and some service providers must hire a Qualified Security Assessor to conduct a PCI DSS Audit to identify whether the organization has more than 400 security controls required by the PCI Data Security Standard
-
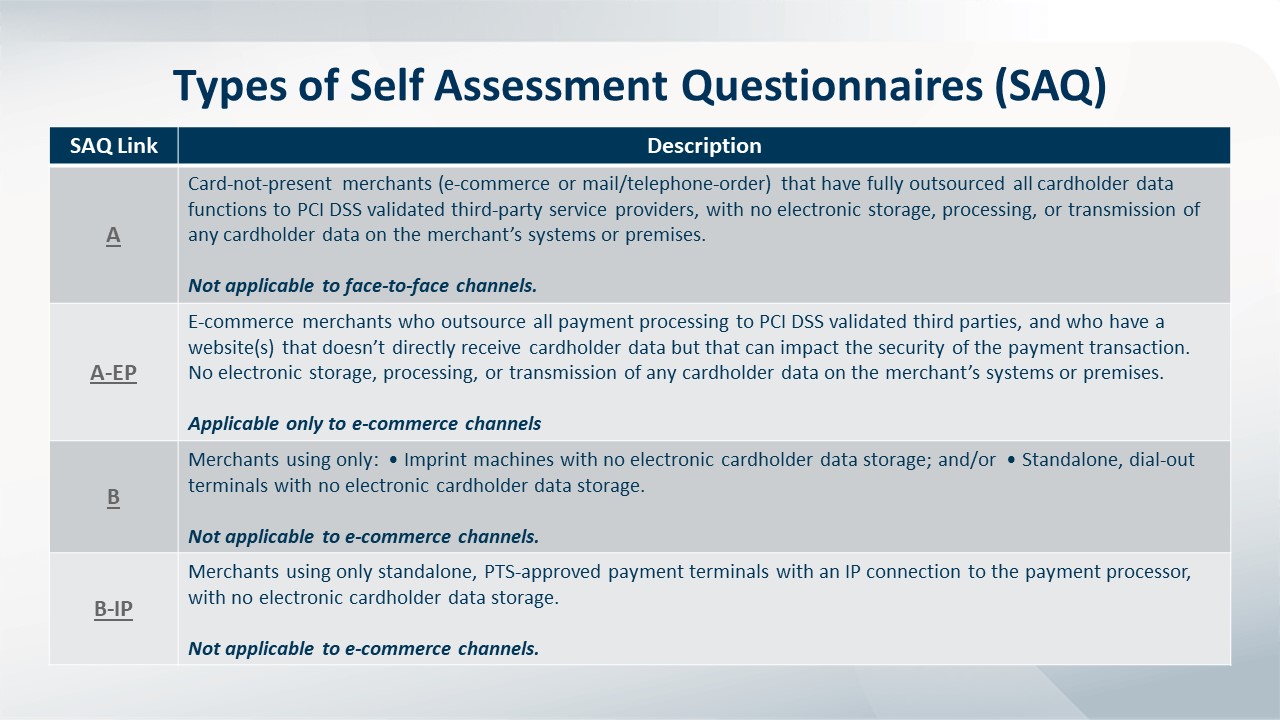
Determine which Self-Assessment Questionnaire to use (based on how your organization processes credit cards).
Do you take credit cards by phone? Over the Internet? On a point-of-sale device? How you process credit cards significantly affects which SAQ form you must fill out. If you're wondering, "which SAQ is right for me?" there are nine different SAQs a merchant can choose from. Generally speaking:
Click to enlarge.
-
- SAQ A is for e-commerce/mail/telephone-order (card-not-present) merchants that have fully outsourced all cardholder data functions. No electronic storage, processing, or transmission of any cardholder data on the merchant’s systems or premises takes place.
- SAQ A-EP is for e-commerce-only merchants that use a third-party service provider to handle their card information and who have a website that doesn’t handle card data but could impact the security of the payment transaction. No electronic storage, processing, or transmission of any cardholder data on the merchant’s systems or premises takes place.
- SAQ B is for merchants that use imprint machines and/or standalone, dial-out terminals, and have no electronic cardholder data transmission, processing, or storage. Not for e-commerce environments.
- SAQ B-IP is for merchants using only standalone, PTS-approved payment terminals with an IP connection to the payment processor, and that have no electronic cardholder data storage. Not for e-commerce environments.
- SAQ C-VT is for merchants that use a virtual terminal on one computer dedicated solely to card processing. No electronic cardholder data storage. Not for e-commerce environments.
- SAQ C is for any merchant with a payment application connected to the Internet, but with no electronic cardholder data storage.
- SAQ P2PE is for merchants using approved point-to-point encryption (P2PE) devices, with no electronic card data storage.
- SAQ D for Merchants is for merchants that do not outsource their credit card processing or use a P2PE solution and may store credit card data electronically.
- SAQ D for Service Providers is for service providers deemed eligible to complete an SAQ.
See Table 3 to understand the different types of payment card processing methods and which apply.
-
Download the official SAQ Questionnaire and Attestation of Compliance (AoC).
The AOC is a form used by merchants and service providers to attest to the results of a PCI DSS self-assessment. It is submitted to an acquirer or payment brand along with the appropriate SAQ, plus any other requested documentation. These forms can be found at https://www.pcisecuritystandards.org/document_library. Ensure you use the most up to date SAQ.
Now, it’s time to actually put your security to the test. The SAQ will ask questions to show that you're taking appropriate security measures needed to keep cardholder data secure at your business. Each SAQ includes a list of security standards that businesses must review and follow. PCI SAQs vary in length. SAQ A is the shortest with just 22 questions, and the longest is SAQ D with 329 questions. You must answer accurately.
The SAQ is a roadmap to better security. Filling out a PCI SAQ is the best way to make sure you aren’t missing any business security requirements.
The SAQ is usually completed by members of the IT or information security team. The completed SAQ is delivered along with a signed Attestation of Compliance (AoC) by an officer of the company responsible for compliance (usually the Chief Financial Officer or equivalent).
Given the importance of choosing the right questionnaire and also ensuing that it is completed accurately, it often makes sense to work with a qualified PCI QSA firm that can help simplify the self-assessment process. Engaging a QSA like ERM Protect can provide invaluable assistance in determining which SAQ is most applicable and reducing the scope of your cardholder data environment.
-
Conduct Vulnerability Scans and Penetration Testing, if necessary.
Vulnerability scans look for known vulnerabilities in your systems and report potential exposures. Penetration tests are intended to exploit weaknesses in the architecture of your IT network and determine the degree to which a malicious attacker can gain unauthorized access to your assets.The organization may be required to undergo annual penetration tests and quarterly vulnerability scans for compliance depending on the type of SAQ.
-
- PCI SAQ A – No vulnerability scans or penetration tests necessary.
- PCI SAQ B – No vulnerability scans or penetration tests necessary.
- PCI SAQ C – Vulnerability scans are required, but no penetration tests.
- PCI SAQ C-VT – No vulnerability scans or penetration tests necessary
- PCI SAQ D – Vulnerability scans are required, along with penetration tests.
- PCI SAQ P2PE-HW – No vulnerability scans or penetration tests necessary.
Vulnerability scanning refers to quarterly external vulnerability scans of networks that must be performed by a PCI approved vendor – known as an Approved Scanning Vendor. A PCI penetration test is a “pen test” that has specific requirements under PCI DSS to verify the protection of Cardholder Data. A PCI Pentest is designed to validate the security of credit cards. PCI DSS does not require that a QSA or ASV perform the penetration test — it may be performed by either a qualified internal resource or a qualified third party. However, if internal resources are being used to perform penetration tests, those resources must be experienced penetration testers.
If you need to conduct vulnerability scans or penetration testing, ERMProtect is here to help.
-
Complete the Attestation of Compliance.
More commonly known as the Attestation of Compliance (AoC), this document is included as part of the Self-Assessment Questionnaire (SAQ) you downloaded, and it’s to be completed once all the requirements for your applicable SAQ have been met. This document is often requested by payment processors, gateways, acquiring banks, customers, prospects, and other interested parties wanting evidence of actual PCI DSS compliance and certification.
The Payment Card Industry Data Security Standards (PCI DSS) is a moving target, something that organizations should be focusing on throughout the year. PCI compliance is a commitment that should never cease.
ERMProtect can Help
As one of the original PCI QSA firms, we are experts at payment card compliance, IT security, and data protection. We leverage our 24+ years of experience to secure your payment data, protect your business and manage costs and risk. Click here to talk to a PCI expert on our team or call (800) 259-9660.
Intelligence and Insights

Red, Blue, & Purple Teaming: Unified Strategy Organizations Can’t Ignore

Quantum Computing Puts Today’s Encryption at Risk