Spot the Phish: Career Opportunity Emails
Can you tell which of the emails below are real and which are phishing attempts?
Spoiler Alert: Answers are below.
Answer: All of the emails are phishes! Let’s take a look:
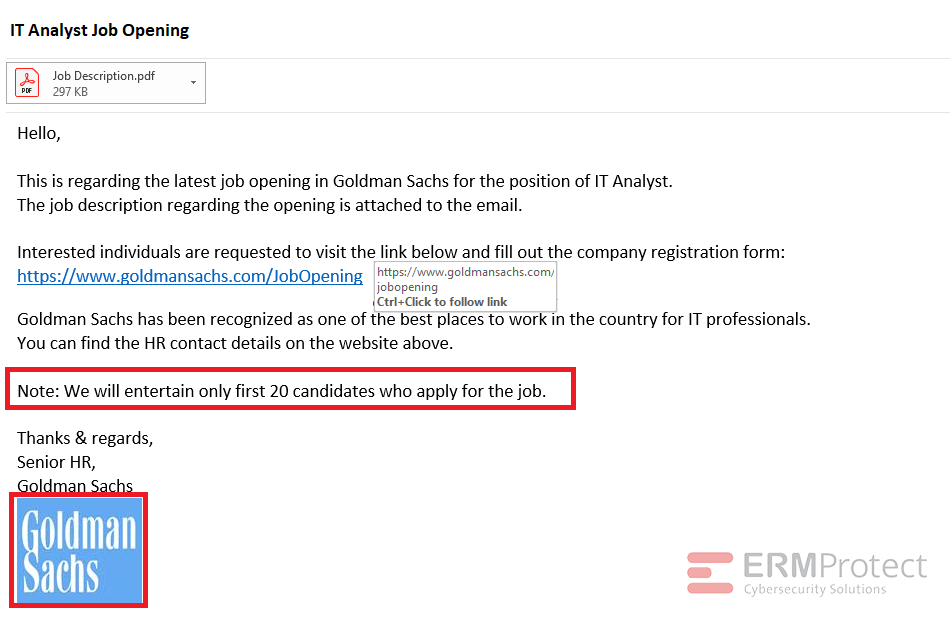
Image 1 details: First, the logo of the company looks disfigured. That’s not at all normal for any reputable organization. Second, the “Note” at the bottom of the email creates a sense of urgency and, honestly, it’s quite ridiculous that a professional organization would treat its hiring process like a lucky draw! Now, the link in the email appears legit. But the attacker is hoping you’ll open the attachment instead. So, s/he is trying to create a bit of trust with the legitimate link. Given this, the chances are quite high that the attachment is infected and will fire off a malicious executable in the background. Attachments that appear innocuous and legit (like the PDF with a legit .pdf extension in this case) can be joined with malicious executables to launch a really sinister attack where you won’t even know that there’s something malicious running in the background while you browse what appears to be an absolutely normal-looking PDF file.
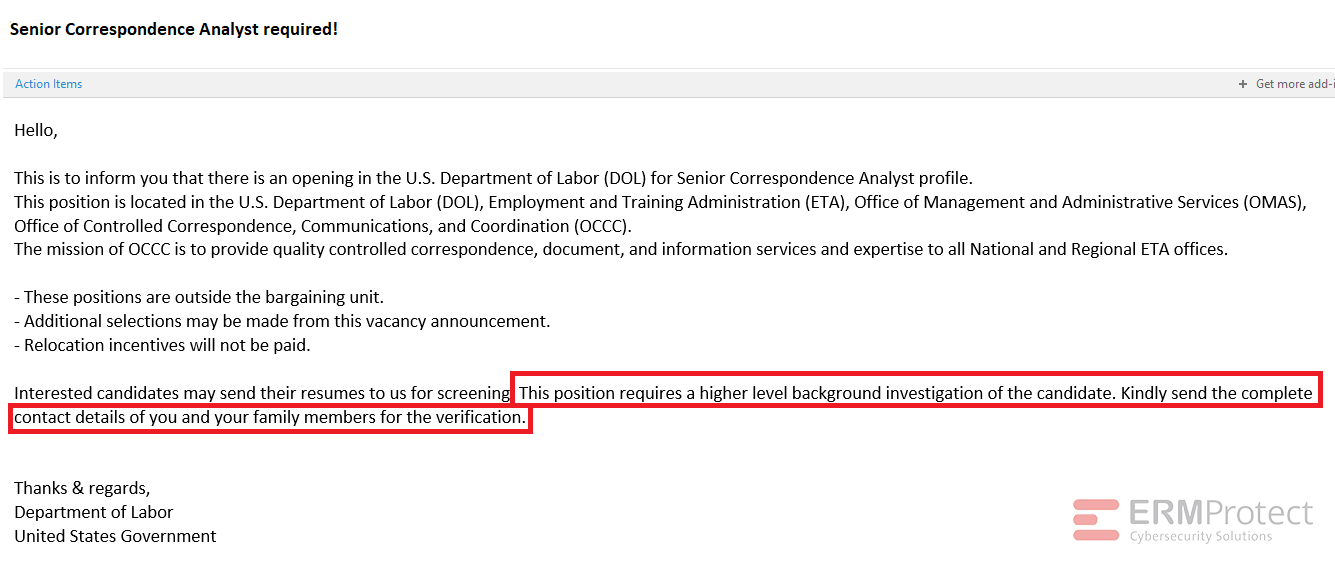
Image 2 details: There are a few grammatical issues in this email. But let’s assume that those can be missed, which is often the case, otherwise phishing attack success rates wouldn’t be as high as they are. The big red flag here is the part that asks you to send the “complete contact details of you and your family members.” That’s the one thing you should focus on and immediately press the “delete” button. Government organizations do not function this way. They’re not going to ask you to send all of that information over email; definitely not in their very first email to you. That just doesn’t happen!
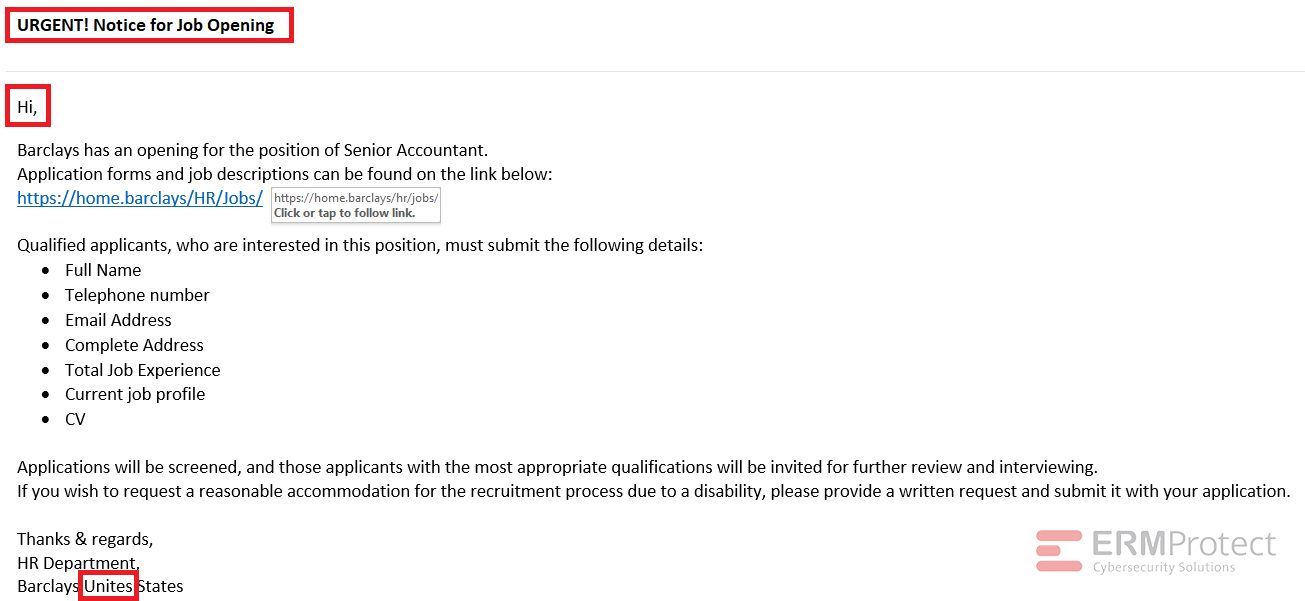
Image 3 details: The subject line of the email creates a sense of urgency that isn’t typical for a professional email. Furthermore, that “Hi” in the salutation doesn’t inspire confidence. There is also the typo in the email where “United” is spelled as “Unites”.
Note that the link in the email appears to be a legit Barclays link, but the fact is that the attacker is hoping to get a reply to this email rather than having you click the link. Even if the sender’s email address looks like a legitimate Barclays address, you need to know that phishing emails can be designed to have a different “Reply To” address. So, an attacker could send you a spoofed email that comes from a legitimate Barclays email address but makes you reply to a completely different email address. And the attacker is hoping that you’ll overlook that minor detail.
Image 4 details: The biggest giveaway in this email is the phony domain in the link. Harvard University’s real domain is “harvard.edu” while this one says “harvared.edu”. In fact, the attacker hasn’t even tried hard enough to hide the URL behind something more legit.

Get a curated briefing of the week's biggest cyber news every Friday.

Turn your employees into a human firewall with our innovative Security Awareness Training.
Our e-learning modules take the boring out of security training.
Intelligence and Insights

Are You Prepared for an AI-Powered Cyber Attack?

AI Privacy Risks