Spot the Phishing Attempt - Cybersecurity Awareness
The images displayed below are either phishing emails or real. Spot the phishy one(s)! Click on the images to zoom in.
Spoiler Alert: Answers are below.
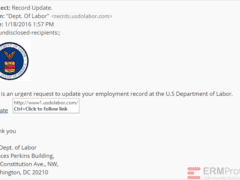
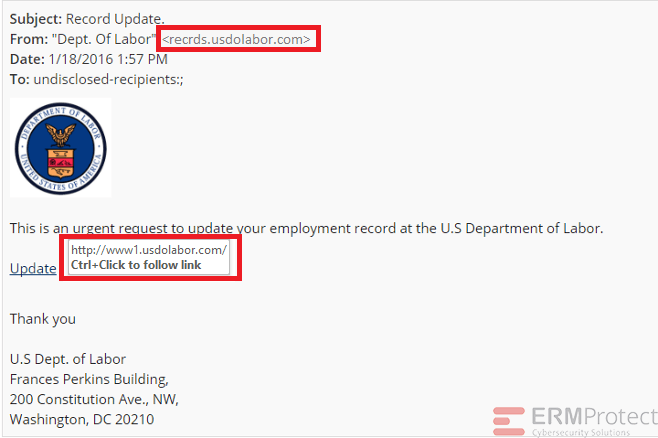
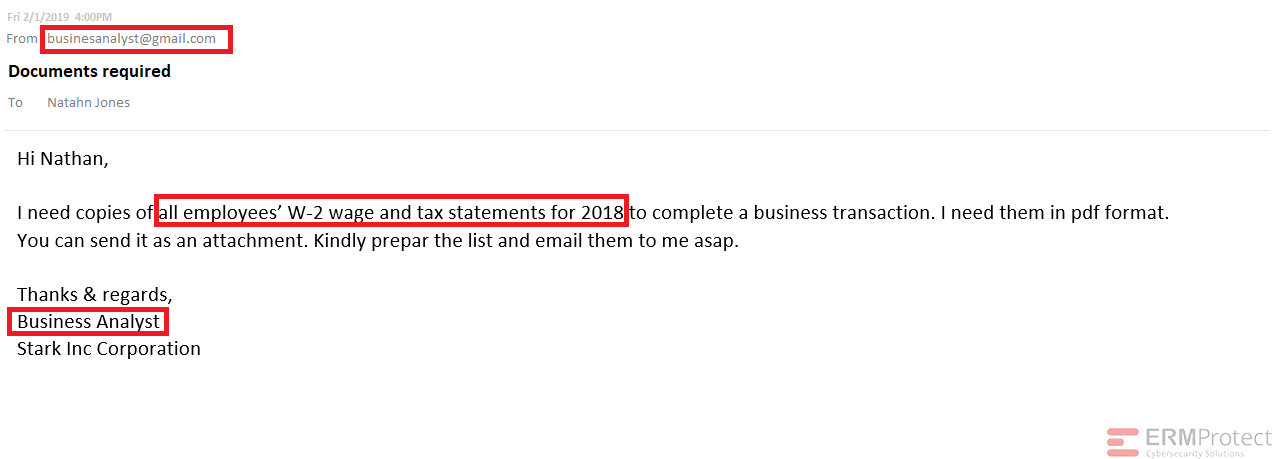
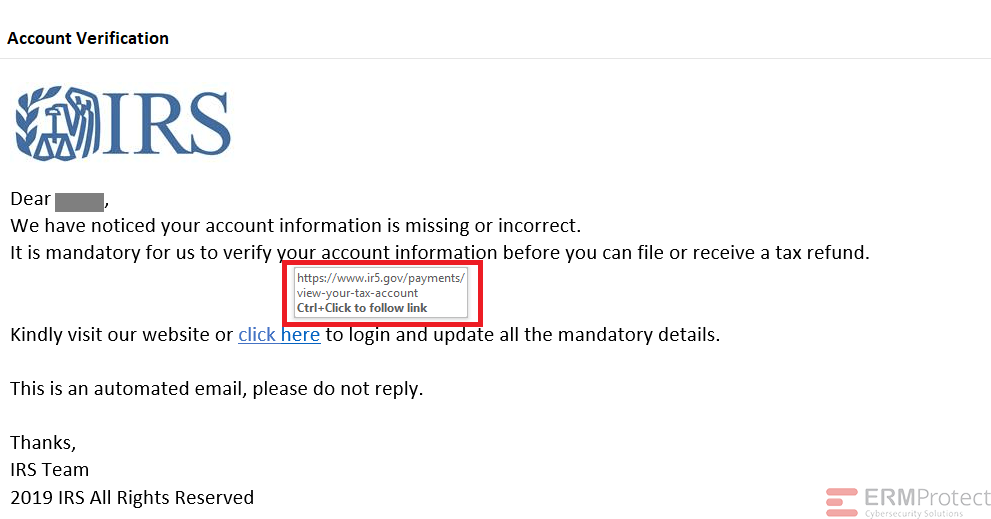
Answer: For a change, all the four emails are phishes! Let’s see how…
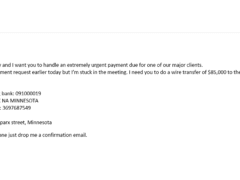
Image 1 details: The biggest sign is that there is money involved! There is a sense of urgency in the email for a money transfer and the email is purportedly from the CEO. Such phishing emails are classic Business Email Compromise (BEC) emails.
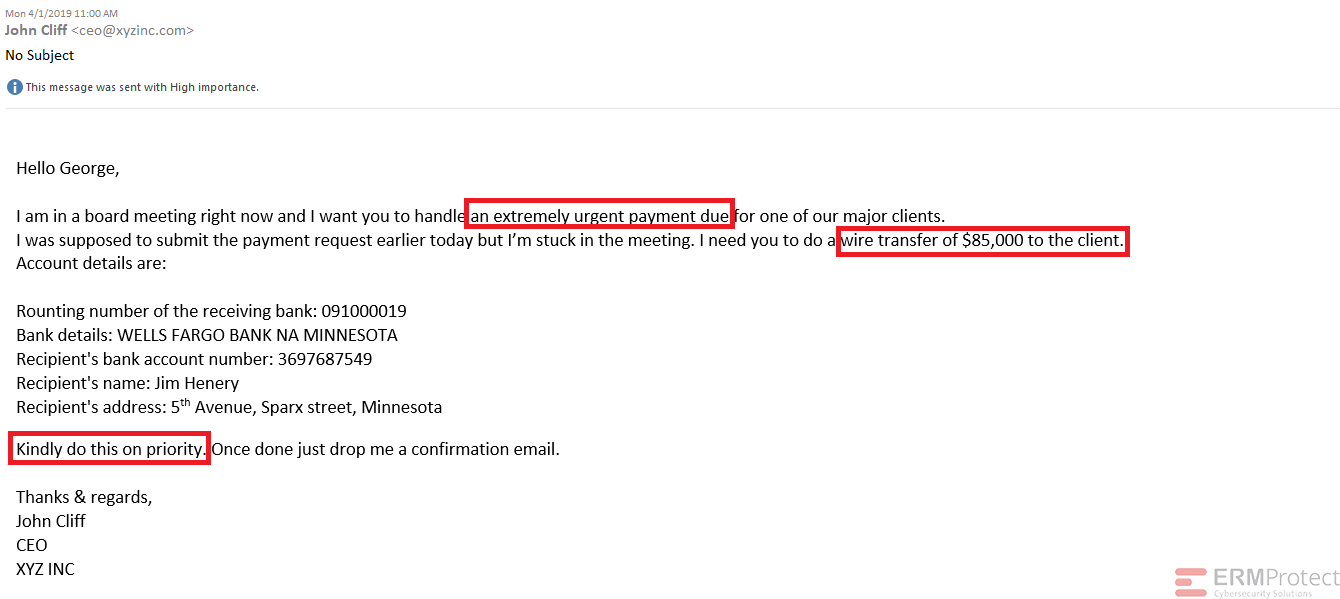
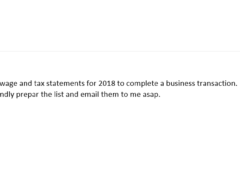
Image 3 details: First, there’s no sender name. Second, the email is sent from a personal (Gmail) account and the sender’s email address has a typo. Third, the sender asks for confidential information to be sent over email. Finally, the signature of the email doesn’t have the name of the sender either. Well, that’s plenty of red flags for you, quite clearly an attempted phishing attack!
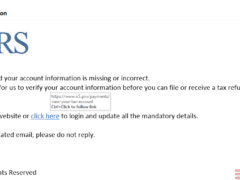
Image 4 details: First of all, the IRS never sends you emails. They always communicate via postal mail. Even if you weren’t aware of that, there’s another thing phishy in the email. Take a look at the hyperlink. You’ll see that the domain is www.ir5.gov. Now that’s phishy! There are other signs, as well, but this should be enough for you to know that this is a phishing email.

Get a curated briefing of the week's biggest cyber news every Friday.

Turn your employees into a human firewall with our innovative Security Awareness Training.
Our e-learning modules take the boring out of security training.
Intelligence and Insights

Cybersecurity Blind Spot: Why Physical Security Is Now the Easiest Way In

Red, Blue, & Purple Teaming: Unified Strategy Organizations Can’t Ignore