Spot the Phishing Attempt - Cybersecurity Awareness
The images displayed below are a combination of phishing emails and real emails sent from various e-commerce websites. Spot the phish! Click on the images to zoom in.
Spoiler Alert: Answers are below.
Answer: Image 1 and 4 are real emails. The others are phishes. Take a look below…
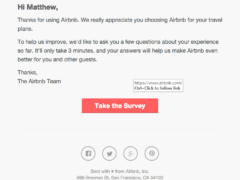
Image 1 details: The biggest sign is that the URL is legitimate. Further, there is nothing in the image that looks phishy.
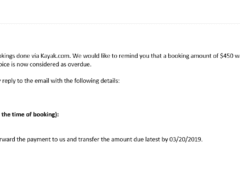
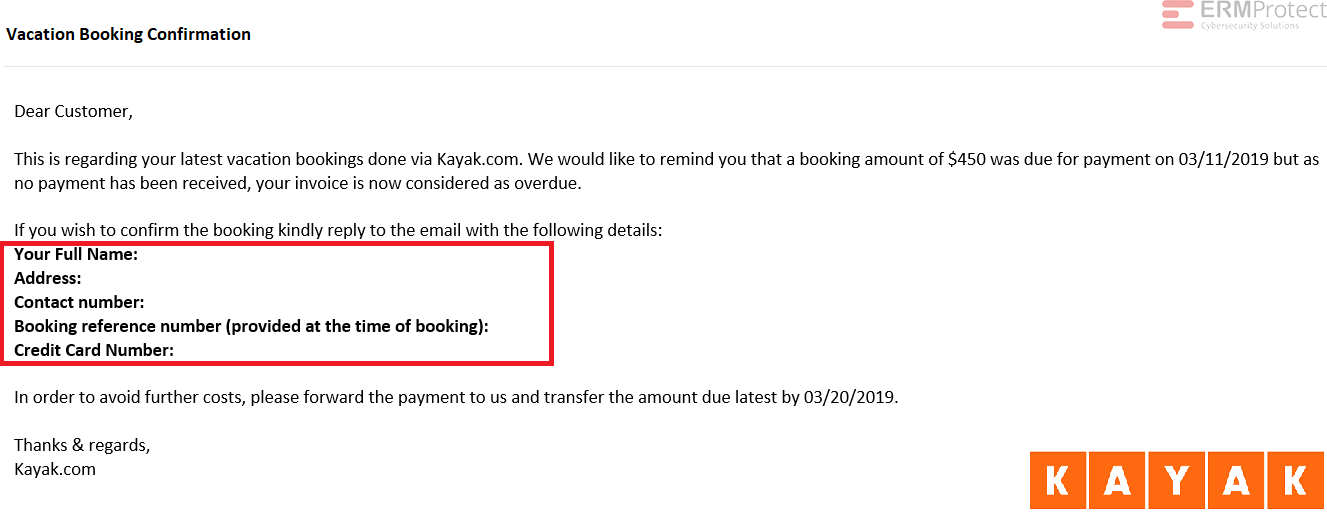
Image 2 details: The email is purportedly sent from an online travel booking website, Kayak.com. They are asking for personal details including a contact number and address which is unusual as they should already have these details. They are asking for a credit card number, which is highly phishy. Professional organizations typically won’t request such information over email. All in all, there’s something phishy going on here, and it could well be an e-Commerce scam!
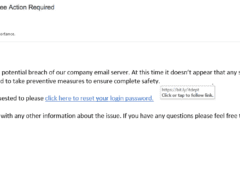
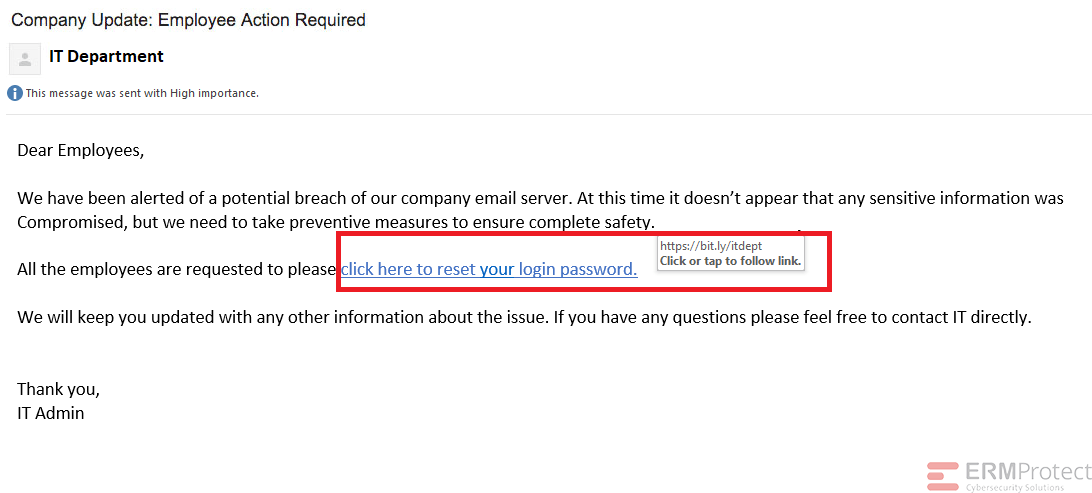
Image 3 details: In cybersecurity awareness you should understand an IT department wouldn’t likely ask employees to click a link to reset passwords.
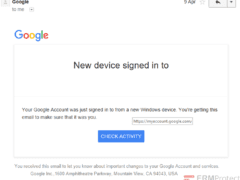
Image 4 details: There is nothing phishy in the hyperlink if you run it through your typical URL check. Overall, it looks like a typical login notification email sent from Google.

Get a curated briefing of the week's biggest cyber news every Friday.

Turn your employees into a human firewall with our innovative Security Awareness Training.
Our e-learning modules take the boring out of security training.
Intelligence and Insights

Are You Prepared for an AI-Powered Cyber Attack?

AI Privacy Risks