Spot the Phishing Attempt - Cybersecurity Awareness
The images displayed below are a combination of phishing emails and real emails. Spot the phish! Click on the images to zoom in.
Spoiler Alert: Answers are below.
Answer: All the emails are phishes! Let’s take a look below…
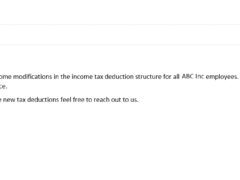
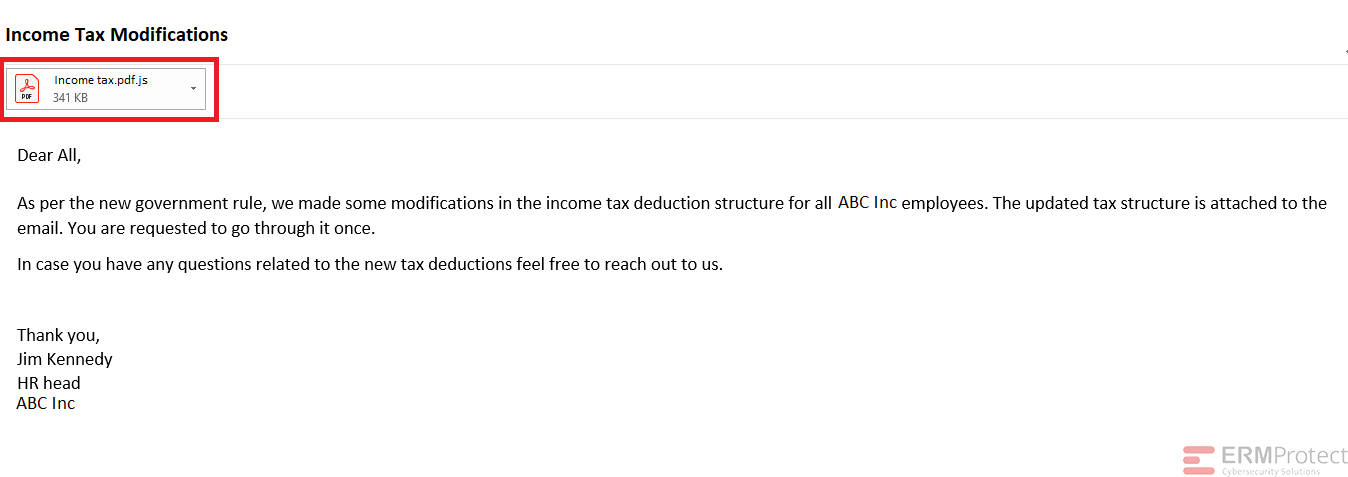
Image 1 details: The attachment is actually a .js file, not a PDF as the icon indicates. Take a closer look at the attachment and you’ll see it. In cybersecurity awareness you should never rely on the icon of the attachment as it can easily be manipulated. Instead, closely analyze the actual extension of the attachment.
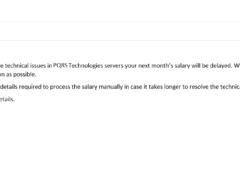
Image 2 details: Once again, the attachment has a .com extension. It’s a clear phish!
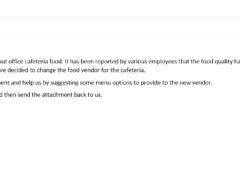
Image 3 details: Here comes another malicious attachment! This one is a .bat extension which is essentially a batch script that can execute whatever code it holds on your machine. Plus, the email has spelling errors. It’s a phish!
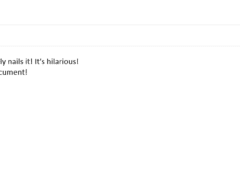
Image 4 details: Here’s an instance when you need to go beyond analyzing the attachment and use your common sense. The chances of the President of an organization sending out this kind of email are pretty slim. Although the attachment appears legitimate, there is embedded code that can be used to join a typical Word document with a malicious executable file. It’s important to rely on your gut feeling from time to time. This is an attempted phishing attack!

Get a curated briefing of the week's biggest cyber news every Friday.

Turn your employees into a human firewall with our innovative Security Awareness Training.
Our e-learning modules take the boring out of security training.
Intelligence and Insights

Red, Blue, & Purple Teaming: Unified Strategy Organizations Can’t Ignore

Quantum Computing Puts Today’s Encryption at Risk