Which of these are phishing attempts?
The images displayed below are a combination of phishing and real emails. Can you spot which are real and which are phony?
Spoiler Alert: Answers are below.
Answer: Images 2 and 4 are the real ones. The rest are phishes. Let’s take a look.
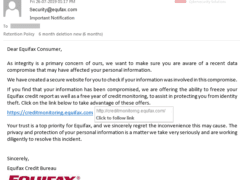
Image 1 details: First, the “from” address in the email clearly uses a fake domain that tries to look like Equifax’s real domain. Such misspellings are a big giveaway. Second, the URL in the email tries to take you to the same phishy domain “equfax.com,” not to mention that “monitoring” has an “i” missing in there.
Image 2 details: This email from LinkedIn is legitimate. It provides all the significant details of a data breach including cause, data involved, actions taken, and where to get more information. Further, it doesn’t contain any links. Always be cautious and look closely at notices of data breaches. Scammers often use these incidents to send their own versions of phishing emails.
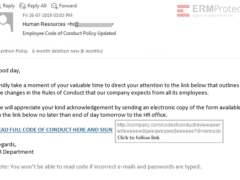
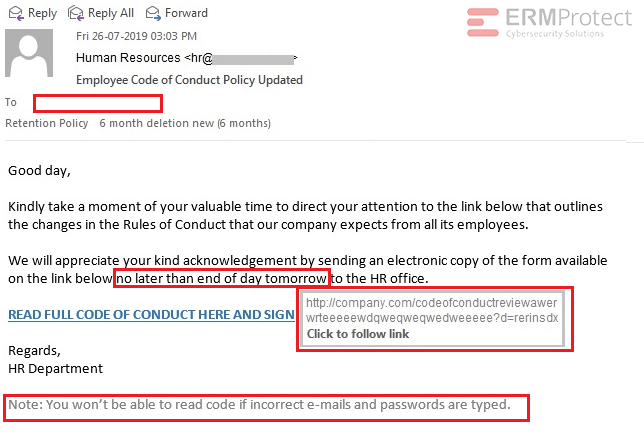
Image 3 details: There are a lot of phishy signs in this email, starting with the “To” field which is blank. The email then tries to create a sense of urgency by placing a deadline on sending the forms by “end of day tomorrow.” The URL is an “http” link instead of an “https” link. Finally, the “Note” at the end of the email is quite phishy.
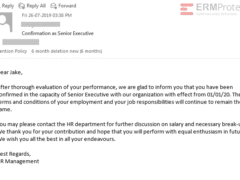
Image 4 details: This one is legit. What’s important to note is that there are no links in this email. That lowers the risks. While it’s possible the sender might get back in touch again with a phishy email, this email isn’t one.

Get a curated briefing of the week's biggest cyber news every Friday.

Turn your employees into a human firewall with our innovative Security Awareness Training.
Our e-learning modules take the boring out of security training.
Which of these are phishing attempts?

Red, Blue, & Purple Teaming: Unified Strategy Organizations Can’t Ignore

Quantum Computing Puts Today’s Encryption at Risk