Spot the Phishing Attempt - Cybersecurity Awareness
The images displayed below are a combination of phishing and real emails related to healthcare. Spot the phish! Click on the images to zoom in.
Spoiler Alert: Answers are below.
Answer: Email 2 is the real email. The others are phishes! Let’s take a look below…
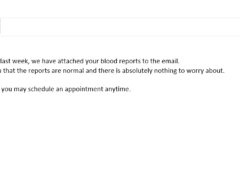
Image 1 details: First of all, it’s not a good idea to send health checkup reports to the patient via e-mail. Second, it’s unencrypted! A legitimate healthcare provider will never do that from a HIPAA compliance standpoint. This is a phish.
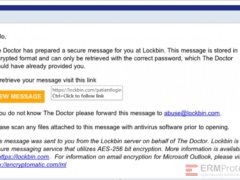
Image 2 details: The email passes our link checks, format checks, and grammar checks. Nothing seems fishy. Still, it’s wise to be cautious when it comes to cybersecurity. Rather than click the link and to be extra safe, log in to “lockbin” separately using your browser.
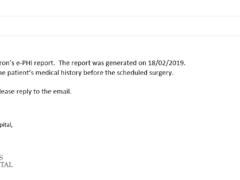
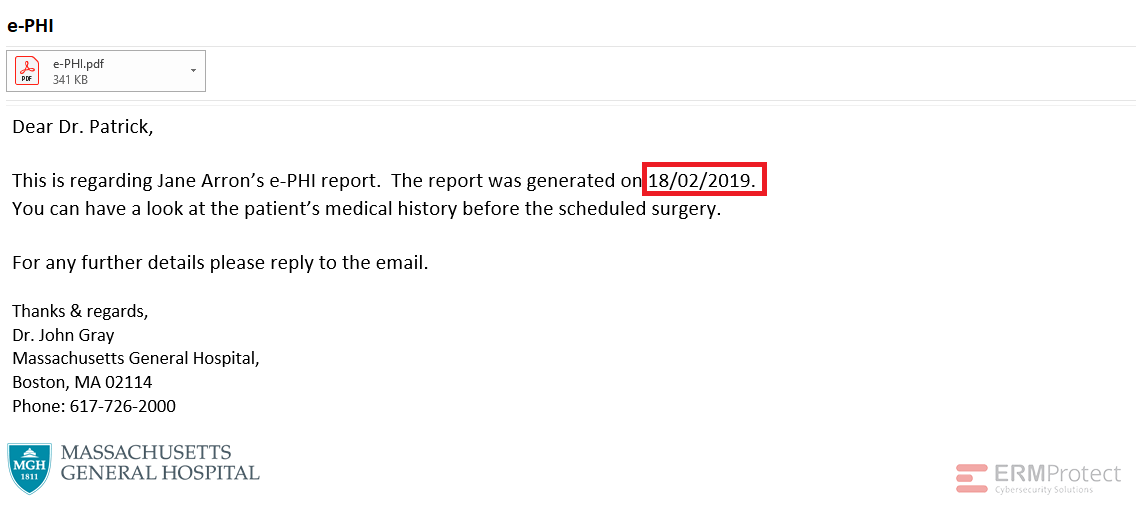
Image 3 details: First, the date format is a non-U.S. one. Second, it’s an unencrypted attachment once again. That’s not allowed under HIPAA, and no professional healthcare provider would want to violate HIPAA. This one’s an attempted phishing attack, too!
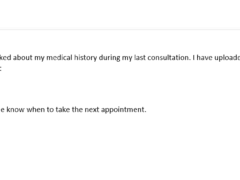
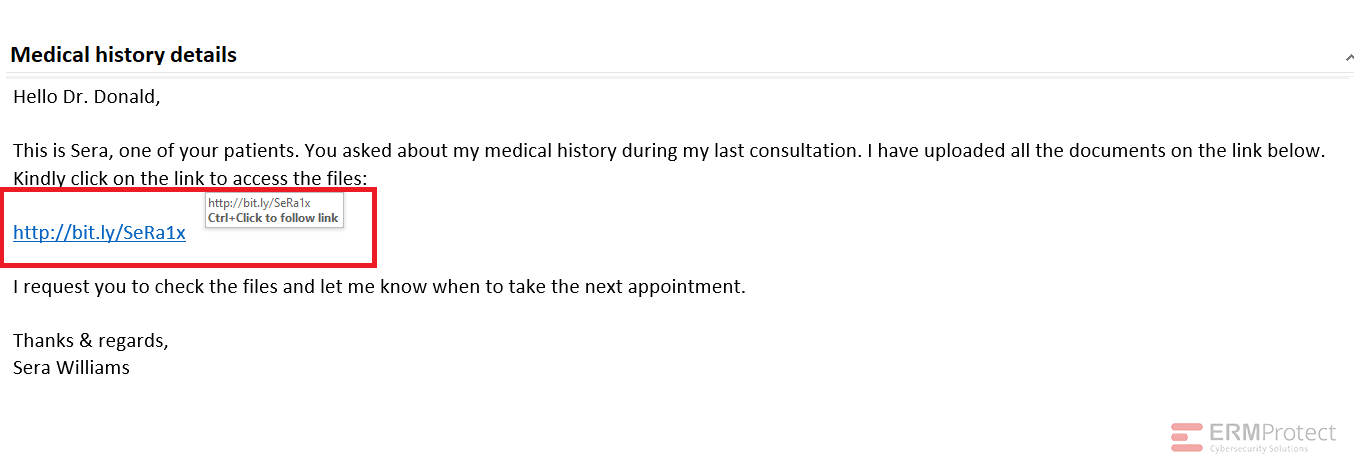
Image 4 details: While the email gives very little away, the short bit.ly link doesn’t inspire confidence at all. This one is best avoided and is most likely a phish!

Get a curated briefing of the week's biggest cyber news every Friday.

Turn your employees into a human firewall with our innovative Security Awareness Training.
Our e-learning modules take the boring out of security training.
Intelligence and Insights

Are You Prepared for an AI-Powered Cyber Attack?

AI Privacy Risks