Spot the Phishing Attempt - Cybersecurity Awareness
The images displayed below are a combination of phishing and real emails. Spot the phish! Click on the images to zoom in.
Spoiler Alert: Answers are below.
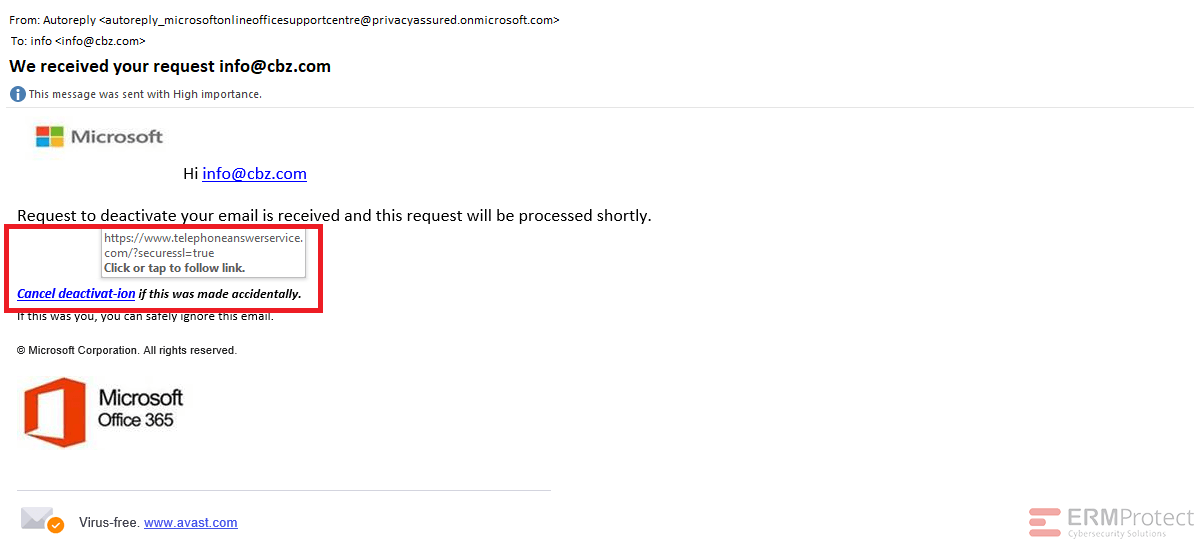
Answer: Email 1 is the phish! All the others are real. Let’s take a look below…
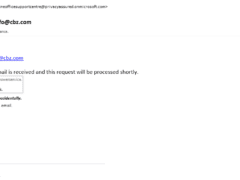
Image 1 details: The hyperlink appears to be from a phishy domain. When focusing on cybersecurity awareness, the sender’s email address also looks suspicious. Apart from these signs, there’s also the italicized text which isn’t very typical of Microsoft emails.
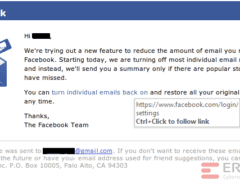
Image 2 details: The email is indeed a real email from Facebook. It ticks all our checkboxes. Nothing phishy overall.
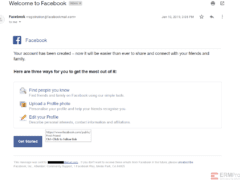
Image 3 details: The email looks alright overall. The sender’s email is from a facebookmail.com domain, and if you check online, Facebook states that it does send notifications from that domain. Though Facebook scams are very popular when it comes to cyber attacks, this is not one of them.
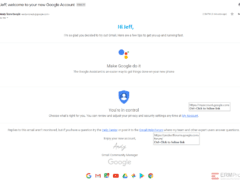
Image 4 details: It looks like a typical welcome email from Gmail. It passes all the typical checks. The links look good. too.

Get a curated briefing of the week's biggest cyber news every Friday.

Turn your employees into a human firewall with our innovative Security Awareness Training.
Our e-learning modules take the boring out of security training.
Intelligence and Insights

Are You Prepared for an AI-Powered Cyber Attack?

AI Privacy Risks