Spot the Phishing Attempt - Cybersecurity Awareness
The images displayed below are a combination of phishing and real emails. Spot the phish! Click on the images to zoom in.
Spoiler Alert: Answers are below.
Answer: Image 4 is the only real one.
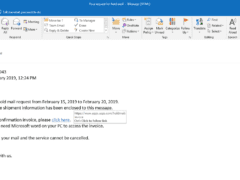
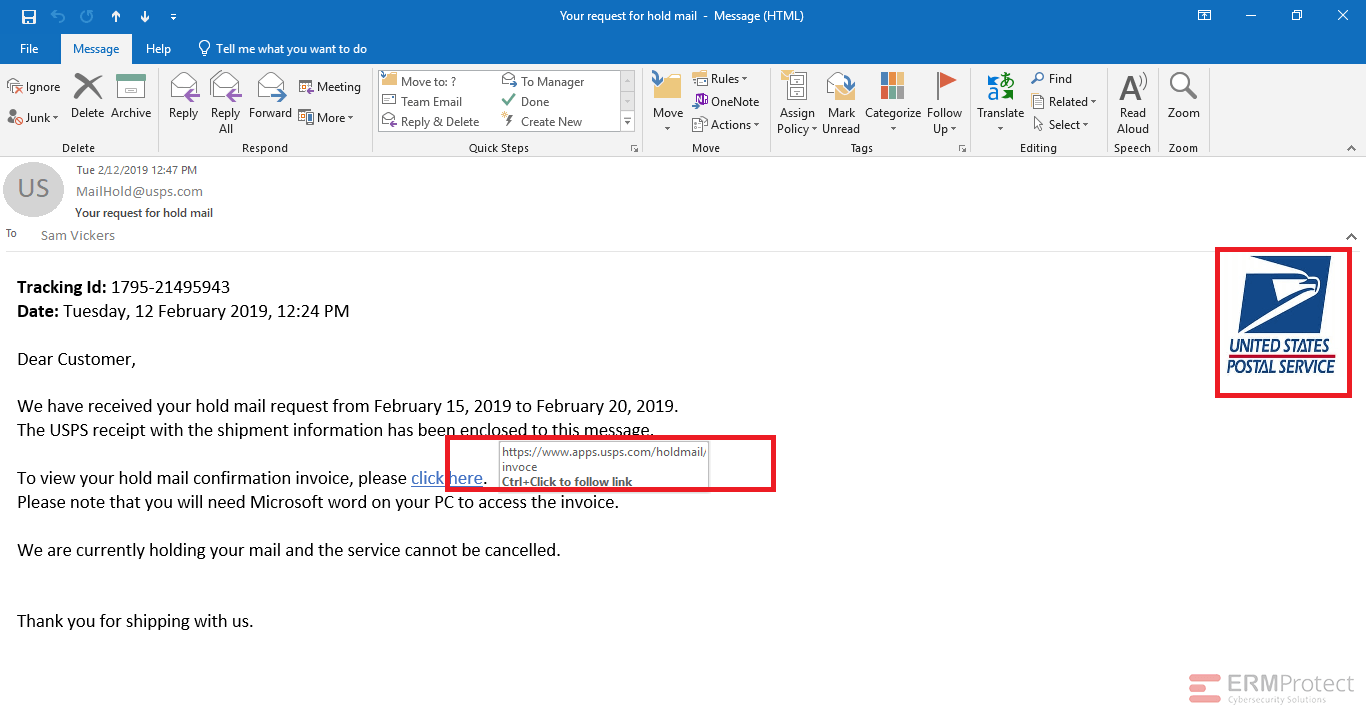
Image 1 details: The sender and the email format are clear, but if you check the URL carefully it has a spelling mistake. Invoice is spelled as invoce, and that can be phishy! Also, they forgot to use the latest logo of USPS. Totally phishy!
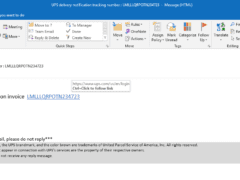
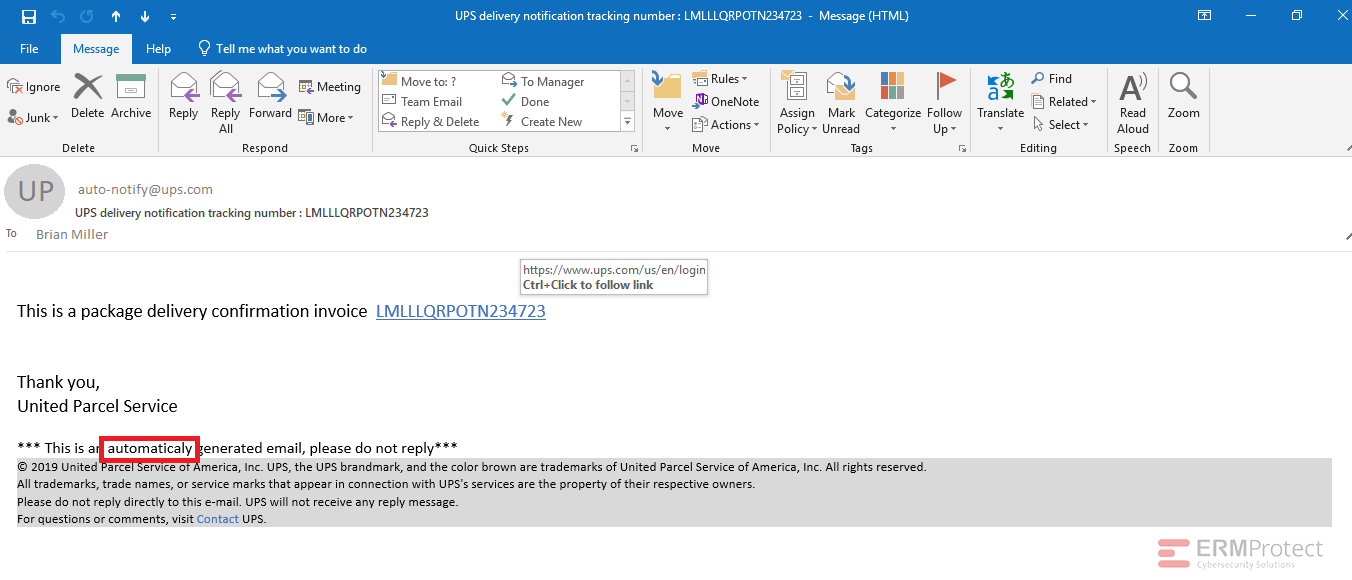
Image 2 details: The email looks clean and the URL also looks legitimate. But as we always say, you need to be very cautious while judging an email. One simple spelling mistake can make it phishy. So, it’s always better to download the invoice directly from the UPS site rather than using the hyperlink.
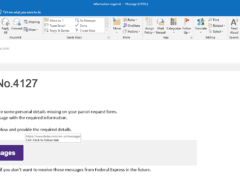
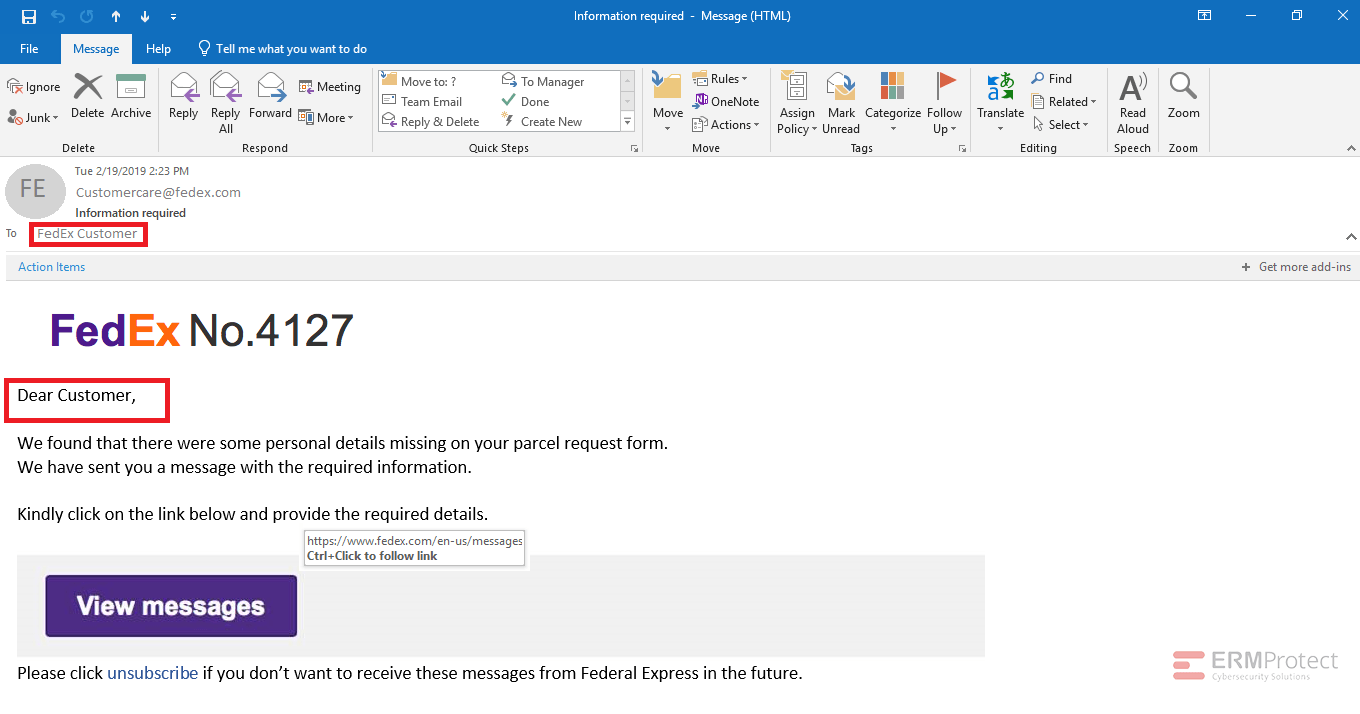
Image 3 details: The third email is a typical phishing email. First, they are asking for your personal details. Second, customer name is not mentioned anywhere in the email. Normally, we check the URL first and, if it looks good, we think that the email is legitimate. But remember: it is always better to check every aspect of the email and use your cybersecurity instincts. It doesn’t make sense that FedEx would reach out in this way.
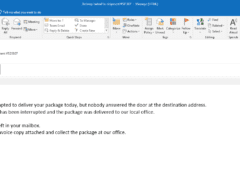
Image 4 details: The image has an attachment which might make you think it’s a possible phishing attack. But the attachment’s name and extension are clear and there are no other mistakes visible in the email.

Get a curated briefing of the week's biggest cyber news every Friday.

Turn your employees into a human firewall with our innovative Security Awareness Training.
Our e-learning modules take the boring out of security training.
Intelligence and Insights

Are You Prepared for an AI-Powered Cyber Attack?

AI Privacy Risks