The Importance of Risk Assessment Services in Cybersecurity: A Comprehensive Guide
By Rey LeClerc Sveinsson, PhD
In today’s rapidly evolving digital landscape, organizations face an unprecedented range of cybersecurity threats. From sophisticated ransomware attacks to insider data breaches, the risks are many and complex.
For any organization striving to safeguard its assets, systems, and data, a solid cybersecurity strategy is essential, and at the heart of this strategy lies one of the most critical practices: cybersecurity risk assessment services.
This comprehensive guide explores the importance of risk assessment services in identifying vulnerabilities and managing threats in organizations.
What is are Cybersecurity Risk Assessment Services?
Cybersecurity risk assessment services are structured processes used to identify, evaluate, and prioritize risks that could negatively affect an organization’s information systems. It helps organizations understand the potential threats they face, the vulnerabilities within their infrastructure, and how they can allocate resources to mitigate those risks effectively.
Risk assessment companies like ERMProtect provide expertise in evaluating these risks and developing strategies tailored to the specific needs of an organization. Risk assessment services from ERMProtect help businesses adopt a proactive approach to cybersecurity, mitigating risks before they turn into real threats.
Why are Risk Assessments Essential in Cybersecurity?
1. Proactive Threat Management
Risk assessments allow organizations to adopt a proactive approach to cybersecurity. Instead of waiting for a cyberattack to occur, assessments enable companies to identify and address potential risks before they can be exploited. By continuously monitoring and reassessing their security posture, organizations can stay ahead of emerging threats.
2. Resource Allocation
Cybersecurity resources, both financial and human, are often limited. A well-executed risk assessment helps organizations prioritize their cybersecurity efforts, focusing on the most critical vulnerabilities and high-impact risks. This ensures that the most valuable assets are protected, and resources are allocated efficiently.
3. Regulatory Compliance
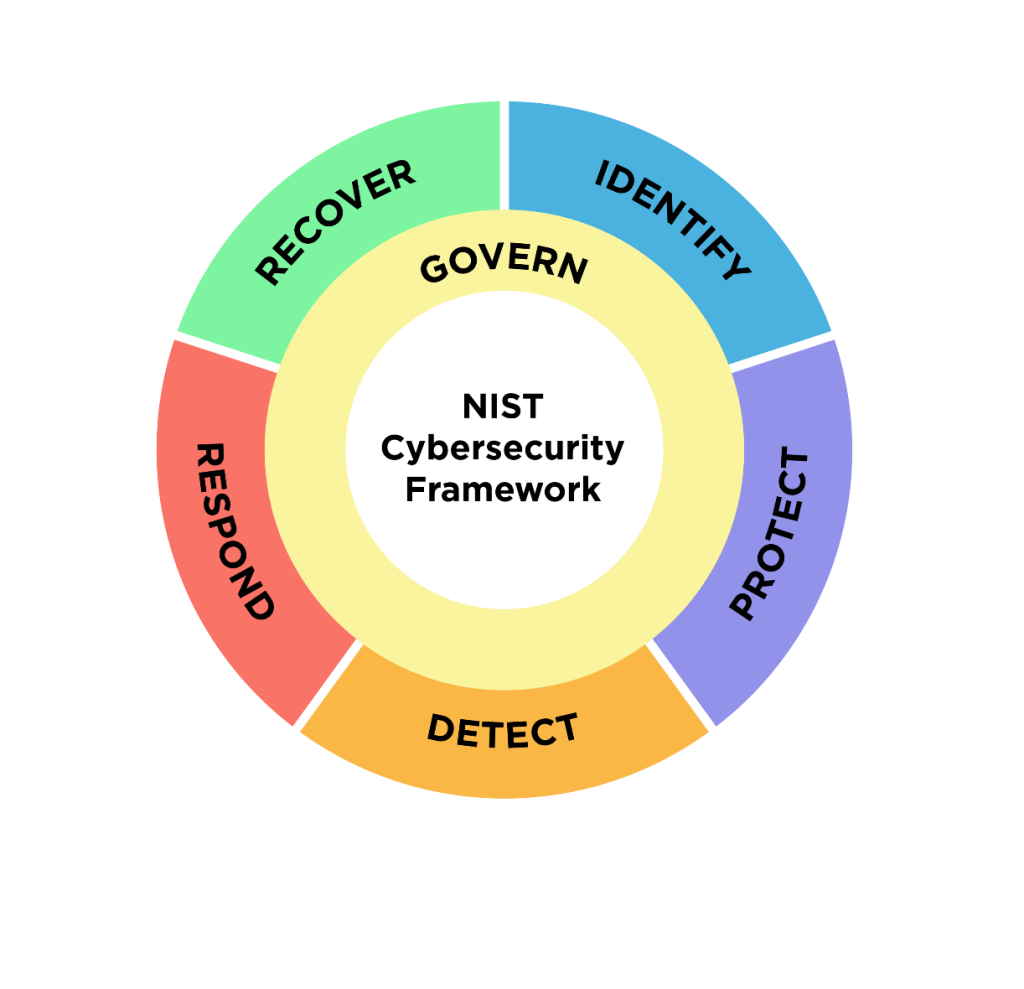
Many regulatory frameworks, such as the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and the NIST Cybersecurity Framework, mandate risk assessments as part of compliance requirements. Regular assessments ensure organizations are meeting legal obligations, avoiding costly penalties and reputational damage due to non-compliance.
4. Enhanced Incident Response
A comprehensive risk assessment improves an organization’s ability to respond effectively to cyber incidents. By understanding potential threats and vulnerabilities in advance, businesses can develop tailored incident response plans, reducing the damage caused by breaches or other security incidents.
5. Protecting Business Continuity
Cybersecurity incidents can disrupt operations, leading to financial losses, reputational damage, and regulatory fines. A thorough risk assessment helps organizations identify risks that could threaten their business continuity, allowing them to implement proper safeguards and recovery plans to ensure minimal disruption.
6. Building a Cybersecurity Culture
Conducting regular risk assessments encourages a culture of cybersecurity awareness across the organization. Employees become more aware of potential threats and are better equipped to recognize and prevent security incidents. This cultural shift is essential in defending against insider threats and human error, which are significant contributors to cyberattacks.
Key Steps in Conducting Risk Assessment Services
To effectively assess and manage cybersecurity risks, organizations should follow a structured approach:
1. Establish a Risk Management Framework
Organizations should adopt a risk management framework such as ISO/IEC 27005, NIST SP 800-30, or OCTAVE (Operationally Critical Threat, Asset, and Vulnerability Evaluation). These frameworks provide guidelines for identifying and evaluating risks, ensuring a systematic and comprehensive approach.
2. Identification of Assets: Cataloging Critical Data, Systems, and Processes
Identifying the organization's critical assets, such as sensitive data, intellectual property, and key business systems, is the first step in understanding what needs to be protected. This involves creating an inventory of all your information assets. These assets can include:
- Data: Sensitive information like customer data, personally identifiable information (PII), intellectual property, and financial records.
- Systems: IT infrastructure components such as servers, databases, networks, cloud systems, and business-critical applications.
- Processes: Internal workflows, business operations, and services that are essential to your organization’s functioning.
While this task may seem straightforward, understanding the full scope of what needs protection can be challenging without external expertise. By identifying what needs protection, organizations can begin to understand the magnitude of risks they face and set the stage for further assessment.
3. Identification of Threats: Recognizing Potential Sources of Threats
Identifying the range of threats facing your organization is the next critical step in the risk assessment process. Organizations must conduct a threat analysis to identify potential internal and external threats. This can include cybercriminals, insider threats, third-party risks, and environmental hazards.
Identifying vulnerabilities involves reviewing systems, networks, and applications for potential weaknesses that could be exploited. Common sources of threats include:
- External Threats: Malicious actors, such as hackers or nation-state actors, who may attempt to breach your systems for financial gain, espionage, or other motivations.
- Insider Threats: Employees, contractors, or business partners who, either through malice or error, may expose your organization to risk. Insider threats are particularly dangerous because insiders often have privileged access to sensitive data.
- Third-Party Risks: Vendors, contractors, and partners can also introduce cybersecurity risks. A breach in their systems can potentially provide an entry point into the organization.
- Environmental Threats: Natural disasters, pandemics, or power outages that could disrupt operations and expose vulnerabilities in your digital infrastructure.
It is important to specialize in identifying these threats by analyzing global cybersecurity trends, evaluating industry-specific risks, and conducting scenario-based threat modeling. Partnering with risk assessment companies allows organizations to stay one step ahead of attackers by anticipating emerging threats.
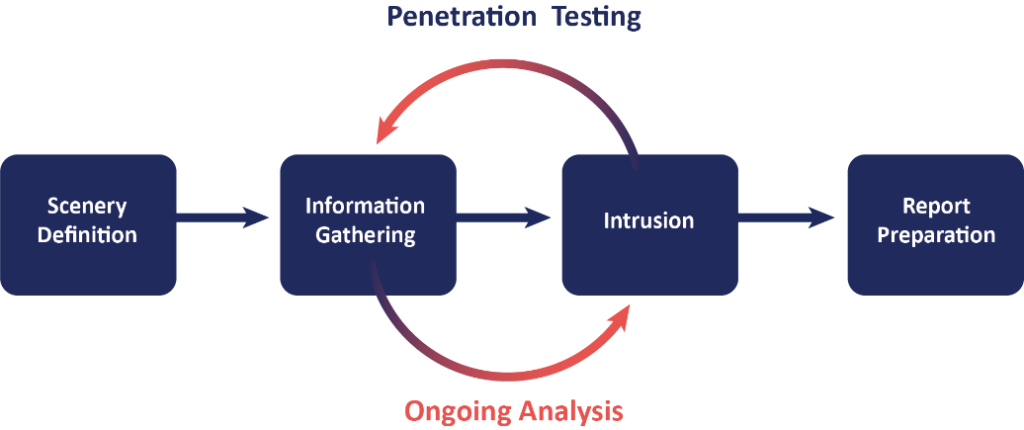
In addition to general threat identification, penetration testing play a unique role in simulating cyberattacks to uncover real-world vulnerabilities.
Through these simulated attacks, penetration testing companies can help organizations see how their defenses perform under pressure and identify gaps that need to be addressed before a genuine attack occurs.
4. Identification of Vulnerabilities: Identifying Weaknesses in Systems, Networks, and Applications
Once assets and threats are identified, the next step is to uncover vulnerabilities that could be exploited. Vulnerabilities come in many forms, including:
- Outdated Software: Failure to update and patch systems and applications regularly can leave exploitable weaknesses.
- Misconfigured Systems: Poorly configured databases, servers, or network devices can expose critical data or create backdoors into your system.
- Weak Security Practices: Lack of encryption, inadequate password policies, or insufficient access controls are all vulnerabilities that increase the likelihood of a breach.
- Human Error: Whether it’s falling victim to phishing attacks or using weak passwords, human error remains one of the biggest cybersecurity risks.
Companies can leverage various tools and techniques, such as automated vulnerability scanning and configuration reviews, to uncover these weak points. For more in-depth evaluations, penetration testing companies can perform manual and automated tests, simulating real-world attacks to see how easily vulnerabilities can be exploited. This process is critical for identifying vulnerabilities that automated tools might miss.
Once vulnerabilities are identified, digital forensic companies come into play when there is suspicion of an actual breach or compromise. These companies use forensic techniques to investigate how a vulnerability may have been exploited and what data or systems may have been affected. This retrospective analysis helps companies understand the scope of an incident and take corrective action.
5. Evaluate Risks and Their Impact
Once threats and vulnerabilities are identified, organizations must assess the likelihood of these risks materializing and their potential impact. The risk matrix, which evaluates the probability and severity of risks, can be a useful tool for ranking risks and determining which areas require the most attention.
Not all risks carry the same weight. Some threats may pose catastrophic consequences, while others may only result in minor disruptions. Evaluating the potential impact of different risks involves assessing:
- Financial Impact: This includes direct costs, such as ransomware payments, legal fees, and compensation for affected customers, as well as indirect costs like loss of business or reputational damage.
- Operational Impact: Cyber incidents can disrupt critical business operations, potentially causing downtime, delays, or loss of productivity.
- Reputational Impact: Public breaches can erode customer trust, damaging the organization’s brand and leading to long-term financial loss.
- Legal and Regulatory Impact: Data breaches can result in hefty fines and legal penalties, particularly under stringent regulations such as the GDPR or CCPA.
To conduct this evaluation effectively, companies use qualitative and quantitative approaches to determine the potential impact of various risks. This impact assessment helps organizations prioritize which risks addressing first and where to allocate resources.
6. Prioritization of Risks: Ranking Risks Based on Likelihood and Impact
Once the risks have been evaluated, organizations need to prioritize their response efforts. Risk assessment help by developing a risk matrix that ranks risks according to two key factors:
- Likelihood: How probable is it that this risk will materialize?
- Impact: What would the consequences be if this risk were to occur?
By combining these two dimensions, risk assessments help organizations focus on the most critical risks—those that are both highly likely and highly impactful. This strategic prioritization ensures that cybersecurity resources are allocated efficiently, addressing the biggest threats first.
In many cases, risk assessors collaborate with penetration testing companies to simulate the most likely attack vectors and validate which risks are most urgent. This collaborative approach provides an additional layer of assurance, allowing businesses to implement targeted mitigation strategies.
7. Implement Mitigation Strategies
After assessing the risks, organizations should develop and implement strategies to mitigate or eliminate the most critical vulnerabilities. This can include technical solutions such as firewalls, encryption, and multi-factor authentication, as well as organizational measures like employee training, access controls, and incident response planning.
Implementing mitigation strategies is a crucial step in strengthening an organization’s cybersecurity defenses. By combining technical controls, organizational measures, and cultural adjustments, companies create a robust, layered defense that addresses vulnerabilities across the entire attack surface. Regular testing, continuous monitoring, and collaboration with cybersecurity partners—such as risk assessment, penetration testing, and digital forensic companies—ensure that mitigation strategies remain effective in the face of evolving threats.
An effective mitigation strategy allows organizations to reduce the likelihood and impact of cyber incidents, ultimately protecting sensitive data, maintaining business continuity, and upholding stakeholder trust.
8. Monitor and Review
Risk assessments are not a one-time activity; they require continuous monitoring and regular updates to reflect changes in the threat landscape, business operations, or regulatory requirements. Periodic reviews ensure that the organization’s cybersecurity measures remain effective and up to date.
In the ever-evolving world of cybersecurity, a risk assessment is only as effective as its ability to adapt to new threats, emerging vulnerabilities, and shifting regulatory requirements. Monitoring and reviewing risk assessments continuously is essential for maintaining a resilient security posture. Organizations that incorporate ongoing monitoring and periodic reviews into their cybersecurity strategy are better positioned to address changes proactively and mitigate risks before they escalate into full-blown incidents.
Risk assessments are not a static exercise but an ongoing commitment to protecting the organization from ever-changing cyber threats. Continuous monitoring provides real-time insights into current risks, while periodic reviews ensure that the organization’s cybersecurity framework remains robust and aligned with its needs. By incorporating these practices into a comprehensive risk management strategy and collaborating with specialized risk assessment companies, penetration testing companies, and digital forensic companies, organizations can stay agile and responsive in the face of evolving threats.
Effective monitoring and reviewing enable organizations to identify and address vulnerabilities quickly, adapt to new regulations, and continuously improve their cybersecurity posture. This proactive approach helps protect sensitive data, maintain compliance, and reduce the likelihood of costly cyber incidents, ultimately contributing to a more resilient and secure organization.
For further insights, explore resources like NIST’s Guide to Risk Management, European Union Agency for Cybersecurity (ENISA) Risk Management Framework and the National Cyber Security Centre (NCSC) Risk Management Guidance.
Risk Assessment Services To Safeguard Your Organization
Cybersecurity risk assessment services are essential in today’s digital world, where cyber threats are increasingly sophisticated and pervasive. Cybersecurity risk assessments are foundational to any robust security strategy. They help organizations identify their most valuable assets, recognize the threats they face, and understand where their vulnerabilities lie.
By identifying vulnerabilities, assessing risks, and prioritizing mitigation efforts, organizations can protect their critical assets and maintain business continuity. Moreover, regular assessments ensure compliance with regulatory standards, enhancing the organization's resilience against cyber threats. Ultimately, a strong risk assessment framework serves as the cornerstone of a robust cybersecurity strategy.
As cybersecurity threats continue to evolve, so must your risk management efforts. Regular assessments, ongoing testing, and a solid incident response plan will ensure that your organization remains resilient in the face of new and emerging threats.
ERMProtect’s Risk Assessment Services
ERMProtect’s range of services offers a holistic approach to cybersecurity risk management. From proactive risk assessment services and vulnerability testing to employee training and regulatory compliance, ERMProtect provides the tools, expertise, and ongoing support needed to create a resilient cybersecurity strategy.
By partnering with ERMProtect, organizations can navigate the complexities of cybersecurity and protect their assets, data, and reputation in a rapidly evolving threat landscape.
For more information, explore ERMProtect’s risk assessment services here.
About the Author
Dr. Rey Leclerc Sveinsson is an expert in Privacy and Data Protection, Information Security, and Technology Governance, Risk & Compliance (IT GRC). He has developed information assurance programs for major organizations globally during his career as well as serving as a Consultant for ERMProtect. He has a PhD in Information Systems and multiple master’s degrees in the areas of privacy, information technology, and cybersecurity laws.
Subscribe to Our Weekly Newsletter

Turn your employees into a human firewall with our innovative Security Awareness Training.
Our e-learning modules take the boring out of security training.
Intelligence and Insights

Quantum Computing Puts Today’s Encryption at Risk

Are You Prepared for an AI-Powered Cyber Attack?