Aligning Your Incident Response Plan with NIST SP 800-61 Rev. 3: What’s Changed and What to Do Now
By Rey LeClerc Sveinsson, PhD
The National Institute of Standards and Technology (NIST) recently released Revision 3 of its Special Publication 800-61, the Computer Security Incident Handling Guide. This update aligns with the new NIST Cybersecurity Framework 2.0 and introduces a broader, more integrated view of incident response (IR). It emphasizes risk management, cross-functional coordination, and continuous improvement.
This article outlines the key updates in the latest NIST guidance, why they’re significant, and what practical steps you can take to update your organization’s incident response plan.
Whether you’re overseeing a security team, supporting compliance efforts, or developing an IR program from scratch, understanding these changes is essential to keeping your strategy aligned with industry’s best practices.
What’s New in SP 800-61 Rev. 3?
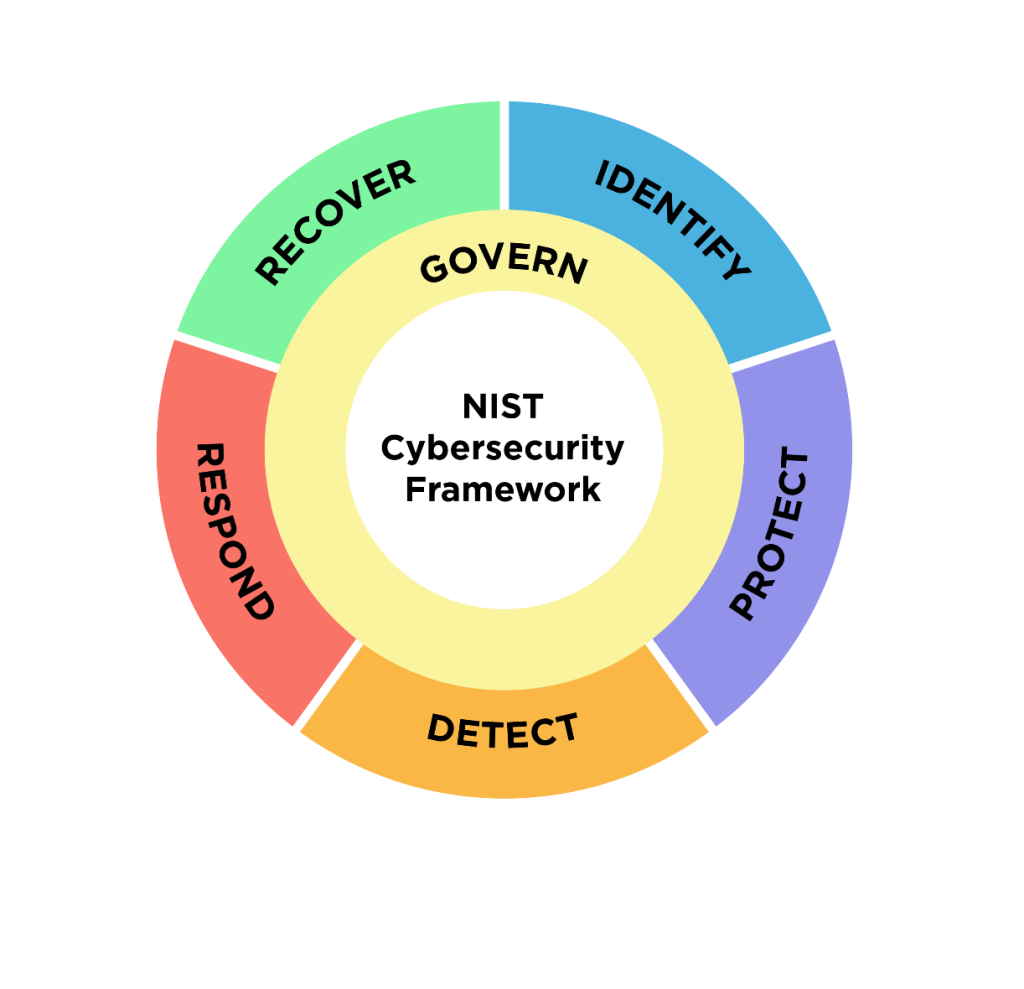
1. Integration with NIST Cybersecurity Framework (CSF) 2.0
NIST's revised Incident Response (IR) guidance directly connects to the CSF 2.0's functions — especially Detect, Respond, and Recover. This alignment helps organizations ensure that incident response efforts fit within the broader cybersecurity strategy, promoting consistency and accountability across the board.
By aligning your IR plan with CSF 2.0, you help ensure that everyone — from your technical teams to your business leaders speaks the same language when it comes to cybersecurity. It makes your response efforts more efficient, reduces confusion during high-pressure situations, and creates a clearer path for reporting to senior management and regulators.
This alignment also promotes consistency across teams and systems and reinforces accountability by making sure responsibilities are tied to specific outcomes within your broader security program.
2. Incident Response as Risk Management
Revision 3 places IR firmly within the enterprise risk management framework. It’s no longer about technical containment; it’s about protecting business operations and supporting informed, strategic decisions. In earlier versions of NIST’s guidance, incident response was mostly treated as a technical process, something handled by the IT or security team to contain and clean up after a breach. With Revision 3, that’s changed. Incident response is now viewed as a core part of your organization’s overall risk management strategy.
That means it’s not just about isolating a malware infection or restoring a server — it’s about protecting the continuity of your operations, minimizing financial loss, managing reputational damage, and staying compliant with legal and regulatory obligations. In short, incident response isn’t just an IT issue anymore. It’s a business issue.
This broader view requires closer coordination with other functions such as legal, compliance, Human Resources, and executive leadership. When something goes wrong, the response shouldn’t be limited to the SOC or IT department scrambling behind the scenes. Instead, decisions need to be made quickly and strategically, based on how the incident affects the organization’s most critical assets, services, and people.
By treating incident response as a risk management function, organizations can make better-informed decisions under pressure. It also allows leadership to allocate resources more effectively, understand what’s truly at stake, and respond in a way that supports the long-term interests of the business, not just a short-term technical fix.
3. Lifecycle Approach and Continuous Improvement
NIST calls for a feedback-driven lifecycle model. Lessons learned after incidents should lead to meaningful changes in training, playbooks, tooling, and detection capabilities. One of the standout messages in Revision 3 is that incident response shouldn’t be a static, one-time exercise. Instead, NIST now frames incident response as a living, continuous lifecycle — one that evolves with every new incident, near-miss, or change in the threat landscape.
This means your IR plan isn’t something you dust off once a year or only after a breach. It’s a working document and process that should constantly be refined based on what happens in your environment. Every incident — whether large or small — presents an opportunity to improve. What worked well? What took too long? Where were communication gaps? What resources were lacking? These are the kinds of questions that should be asked in structured after-action reviews (AARs) and incorporated into updated policies, training, and technical controls.
The new guidance encourages organizations to treat these lessons not as footnotes, but as drivers for meaningful change. That could mean refining detection rules, updating escalation paths, improving documentation, or even changing the way incidents are categorized or prioritized.
By building a culture of continuous improvement, organizations become more agile, more resilient, and better prepared not just for the next attack, but for the next set of challenges the business may face. It also demonstrates to regulators and stakeholders that the organization takes a mature, proactive approach to security and risk management.
4. Expanded Stakeholder Engagement
IR is now a shared responsibility. Legal, HR, Privacy, Communications, and Executive Leadership should be actively involved in planning and response activities. An important shift in NIST’s updated guidance is the clear message that incident response is no longer just a job for IT or cybersecurity teams. It’s a shared responsibility that touches every corner of the organization.
That includes departments you might not traditionally associate with cyber incidents —Legal, Human Resources, Privacy, Communications, and Executive Leadership. Each of these groups brings a critical perspective and set of responsibilities that must be part of both the planning and execution of your response strategy.
Legal needs to advise on potential liability, regulatory obligations, and notification requirements. Privacy teams assess whether personal data was involved and how data protection laws come into play. Human Resources may need to coordinate disciplinary actions or respond to insider threat scenarios. Communications must manage both internal messaging and public statements, while leadership must make swift, informed decisions that balance risk, business continuity, and stakeholder expectations.
When these teams are brought in after an incident occurs, you lose time, introduce confusion, and risk making poor decisions. But if they are part of the process from the start — trained, informed, and included in tabletop exercises — you gain speed, clarity, and coordination.
This expanded involvement isn’t just good practice. It reflects the reality that cyber incidents are business incidents, and effective response requires input from everyone who plays a role in managing risk, protecting the organization’s reputation, and keeping operations on track.
5. Business Impact Over Technical Severity
Incident prioritization should focus on how events affect business goals, customer trust, and regulatory obligations, not just the type of malware or exploit involved. Traditionally, incidents have been ranked based on technical factors — how sophisticated the attack was, what systems were affected, or how quickly it spread. But in today’s environment, technical severity doesn’t always tell the full story.
NIST’s updated guidance encourages a shift in mindset: prioritize incidents based on their impact on the business, not just their technical characteristics. That means looking at how an event affects your ability to deliver services, maintain customer trust, meet legal obligations, and uphold your organization’s reputation.
For example, a minor phishing incident that exposes customer data could have far greater consequences than a failed intrusion attempt on a non-critical server. Likewise, an outage that interrupts operations in a key business unit — even if caused by a low-level misconfiguration — could be more damaging than a high-tech exploit that was quickly contained.
This approach demands closer coordination between technical teams and business leaders. It also requires building out your incident classification and response models to reflect the real-world consequences of an event not just the tools or tactics used in the attack.
By focusing on business impact, your organization can respond more strategically, allocate resources where they matter most, and ensure that executive decision-makers have the information they need to act quickly and appropriately. It also helps demonstrate to regulators and stakeholders that you understand the bigger picture and are managing cyber risk in a way that truly supports your mission.
Six Key Actions to Align Your IR Plan
1. Integrate IR into Enterprise Risk Management (ERM)
Your incident response (IR) strategy shouldn’t operate in a vacuum. It needs to be fully aligned with how your organization views and manages risk overall. That means understanding your company’s risk appetite — how much risk leadership is willing to tolerate — and incorporating that into how you prepare for and respond to incidents.
For example, if your organization has a low tolerance for operational downtime or data exposure, your IR plan should prioritize rapid containment and communication strategies that reflect those priorities. On the other hand, if you're in an industry where regulatory scrutiny is especially high, your plan should emphasize legal review, documentation, and timely notification protocols.
It's also important to connect your incident response reporting to your broader risk management tools, such as your risk register or GRC platform. When you track IR metrics — such as incident frequency, time to resolution, or the business impact of various events — and tie those back to identified enterprise risks, you get a clearer picture of where your vulnerabilities really lie and how effective your controls are.
Your IR strategy should be informed and fed into the same frameworks your risk and compliance teams are using. This ensures that your response planning is not only technically sound but aligned with what matters most to the business. It also gives leadership the visibility they need to make decisions and allocate resources with confidence.
2. Build a Continuous Improvement Process
After every incident — no matter how big or small — there’s a valuable opportunity to learn and improve. But too often, organizations skip over that step in the rush to move on. NIST’s updated guidance encourages teams to treat every incident as a chance to get better, not just recover.
That starts with creating a repeatable, structured process for post-incident reviews. This isn’t about pointing fingers or assigning blame — it’s about asking honest questions: What happened? How did we detect it? What went well? What didn’t? Where were the delays or breakdowns in communication? And what would we do differently next time?
These reviews should happen regularly and follow a consistent format, so they become a natural part of your response lifecycle — not an afterthought. Most importantly, the insights gained shouldn’t just sit in a meeting summary. They should be put to work.
Feed those lessons into your training programs, so teams are better prepared for the next incident. Use them to identify gaps in tools or technology and make the case for needed upgrades. Update your procedures and playbooks to reflect what you’ve learned because an outdated plan, no matter how well-written, won’t help you during the next real-world event.
When you build this kind of feedback loop into your incident response program, you’re not just fixing problems, you’re steadily increasing your organization’s resilience over time.
3. Define Stakeholder Roles and Responsibilities
Incident response isn’t just a job for the IT or security team — it takes a coordinated effort across the entire organization.
One of the most important updates in the new NIST guidance is the emphasis on clearly defining how non-technical teams play a role during and after a security incident. That means your IR playbook should include not only who’s responsible for the technical investigation and containment, but also how departments such as Legal, Human Resources, Communications, Privacy, and Executive Leadership are expected to engage. For example:
- Legal may need to assess contractual or regulatory obligations, advise on notification requirements, and help shape the incident timeline for reporting purposes.
- Human Resources might be involved if the event involves an internal employee or impacts staff operations.
- Communications will need to prepare internal messaging, draft public statements, and manage media inquiries.
- Privacy teams must evaluate whether personal data was involved and help determine whether regulatory bodies or individuals need to be notified.
- Leadership will be responsible for making big-picture decisions, whether that’s notifying the board, informing stakeholders, or approving major response actions.
If these roles aren’t spelled out ahead of time, you risk confusion, duplicated effort, and missed deadlines when the pressure is on. By defining everyone’s responsibilities before an incident occurs, and running practice scenarios to test them, your organization can respond in a faster, more organized, and legally sound way.
4. Align IR Plan with NIST CSF 2.0
Take the time to map your incident response activities to the key functions of the NIST Cybersecurity Framework (CSF) specifically, Detect, Respond, and Recover. This isn’t just a paperwork exercise; it helps ensure that your IR plan fits seamlessly into your broader cybersecurity program. For example, detection activities — such as monitoring, alerting, and threat intelligence — should clearly tie into the “Detect” function. Containment, mitigation, and communication protocols belong under “Respond,” while restoration of systems, lessons learned, and improvements to defenses support the “Recover” function.
By linking each phase of your incident response process to these framework categories, you create a clearer structure, improve coordination across teams, and make it easier to demonstrate alignment with best practices during audits or reviews. It also helps leadership see how IR efforts directly support the organization’s overall resilience and risk management strategy.
5. Add Business Impact Ratings to Incident Categorization
When categorizing incidents, it’s no longer enough to focus solely on the technical details such as whether a system was compromised or what type of malware was involved. Today’s risks demand a broader view.
You need to refine your incident classification system to consider the real-world impact on your organization. That means accounting for factors such as business disruption —how the event affects your ability to operate normally, serve customers, or meet deadlines.
It should also reflect the extent of any data loss or exposure, particularly when sensitive or personal information is involved. And just as important, your categorization should assess the potential for regulatory consequences, including data breach notification requirements, legal liability, and reputational damage.
This kind of impact-based categorization helps prioritize response efforts more effectively. For instance, a technically minor event that results in the loss of customer data may deserve a higher priority — and faster escalation — than a more complex attack that’s quickly contained and has a limited fallout.
By incorporating these business-focused criteria into your incident taxonomy, you enable your teams to focus on what matters most and ensure that leadership can make timely, informed decisions when it counts. It also helps to demonstrate to regulators, customers, and internal stakeholders that you understand the full scope of cyber risk—and are prepared to respond accordingly.
6. Refresh Communication Plans and External Coordination
A strong incident response plan doesn’t just outline what technical actions need to be taken — it also needs to clearly define who communicates with whom when an incident occurs. In the middle of a crisis, confusion around roles and messaging can lead to delays, inconsistent information, or even legal mistakes.
Your plan should lay out a clear communication structure that covers both internal coordination and external outreach.
Internally, it’s essential to know who is responsible for informing executive leadership, engaging legal and privacy teams, briefing the board if necessary, and keeping employees informed.
Externally, the plan should identify who will handle communication with regulators, affected customers or clients, media outlets, and third-party vendors who may need to be involved in the response.
This includes preparing for regulatory notifications, which often have strict timelines and specific reporting requirements. It also means having templates or protocols ready for customer communications, so you can provide timely, accurate, and transparent updates if personal data or services are affected.
And don’t overlook vendor coordination—if your partners or service providers play a role in your operations or security stack, you’ll need a way to quickly loop them in and manage shared responsibilities.
By documenting these communication pathways ahead of time—and regularly testing them in tabletop exercises, you’ll ensure your team can respond quickly and with confidence, helping to reduce confusion, limit damage, and maintain trust with stakeholders when it matters most.
Why These NIST Updates Matter Now
Today’s cybersecurity landscape is fast-moving and at high stakes. A well-written incident response plan that sits on a shelf is not enough. NIST’s revised guidance offers a roadmap to making IR a living, responsive part of your business continuity and security strategy.
By updating your IR plan to reflect the new standards, you not only stay in compliance with best practices, but you also position your organization to respond faster, smarter, and more collaboratively.
ERMProtect’s Role In Keeping Up With NIST Updates
ERMProtect has decades of experience in building and enhancing IR programs across industries. We can help you:
- Evaluate current IR plans against NIST SP 800-61 Rev. 3
- Facilitate multi-team tabletop exercises
- Build stakeholder-specific escalation paths
- Integrate IR metrics into GRC dashboards
- Draft customized communication plans
- Support full NIST CSF 2.0 alignment
If you need to modernize your IR approach and prepare for what’s next, we’re here to help. Contact Silka Gonzalez at [email protected] or Judy Miller at [email protected] to get started.
About the Author
Dr. Rey Leclerc Sveinsson is an expert in Privacy and Data Protection, Information Security, and Technology Governance, Risk & Compliance (IT GRC). He has developed information assurance programs for major organizations globally during his career as well as serving as a Consultant for ERMProtect. He has a PhD in Information Systems and multiple master’s degrees in the areas of privacy, information technology, and cybersecurity laws.
Subscribe to Our Weekly Newsletter

Turn your employees into a human firewall with our innovative Security Awareness Training.
Our e-learning modules take the boring out of security training.
Intelligence and Insights

Are You Prepared for an AI-Powered Cyber Attack?

AI Privacy Risks