Spot the Phishing Attempt - Cybersecurity Awareness
The images displayed below are a combination of phishing emails and real email messages. Can you tell which of them are phishing attempts? Click on the images to zoom in.
Spoiler Alert: Answers are below.
Image 1 details: The email overall appears legitimate. It does not contain any spelling mistakes; it has a hyperlink which appears to be real (leads to the amazon.com domain). It is always good to have heightened cybersecurity awareness, but no red flags here.
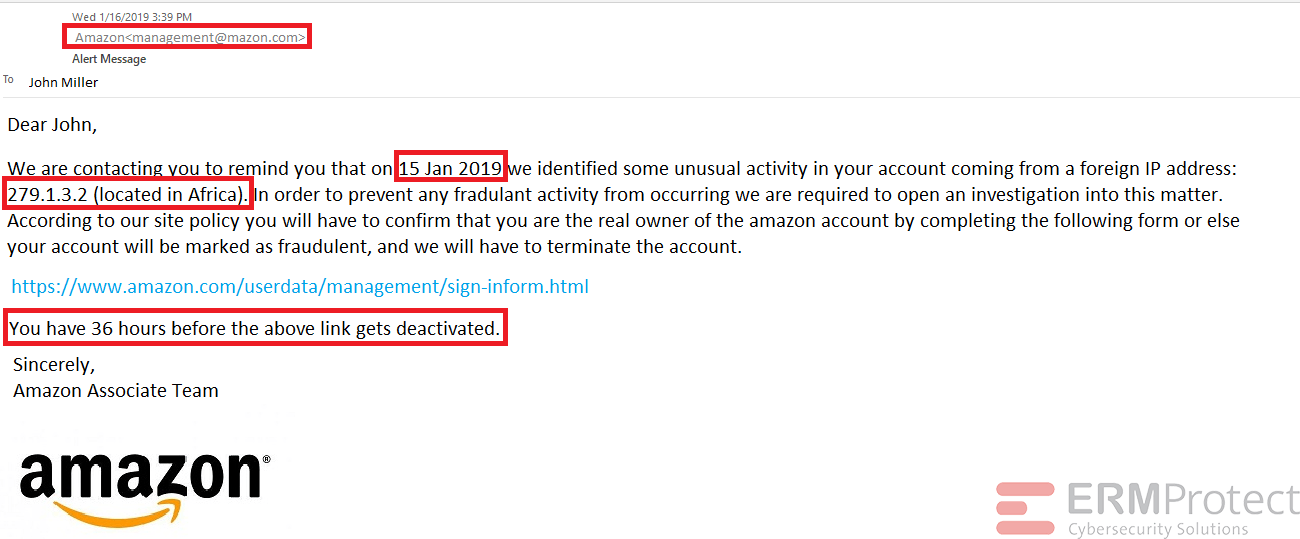
Image 2 details: The email depicts a phony sender name and a non-US date format. The IP address shown is fake and there is sense of urgency in the email. The email contains spelling and grammar errors, looks like a phishing email.
Image 3 details: The image has an actual amazon.com domain link and there are no other phishy red flags.
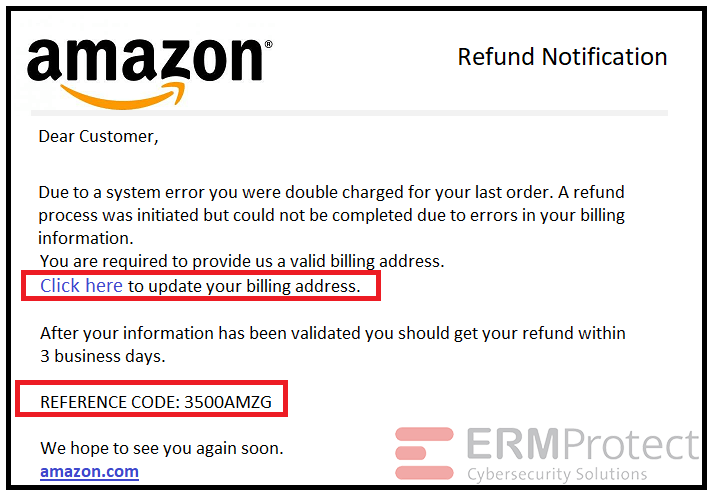
Image 4 details: In the email, Amazon is purportedly providing the customer a refund to lure him/her to click on the given link. Also, it asks for the billing address at the time of purchase. This is not normal cybersecurity protocol if you’ve shopped online before with Amazon. Regarding the reference code, it’s always a good idea to do a quick Google search for the code to see if it is a real reference code. Often, search results will tell you if a code is legitimate, as there would be other discussions going on about it. Looks like an attempted phishing attack.

Get a curated briefing of the week's biggest cyber news every Friday.

Turn your employees into a human firewall with our innovative Security Awareness Training.
Our e-learning modules take the boring out of security training.
Intelligence and Insights

Are You Prepared for an AI-Powered Cyber Attack?

AI Privacy Risks