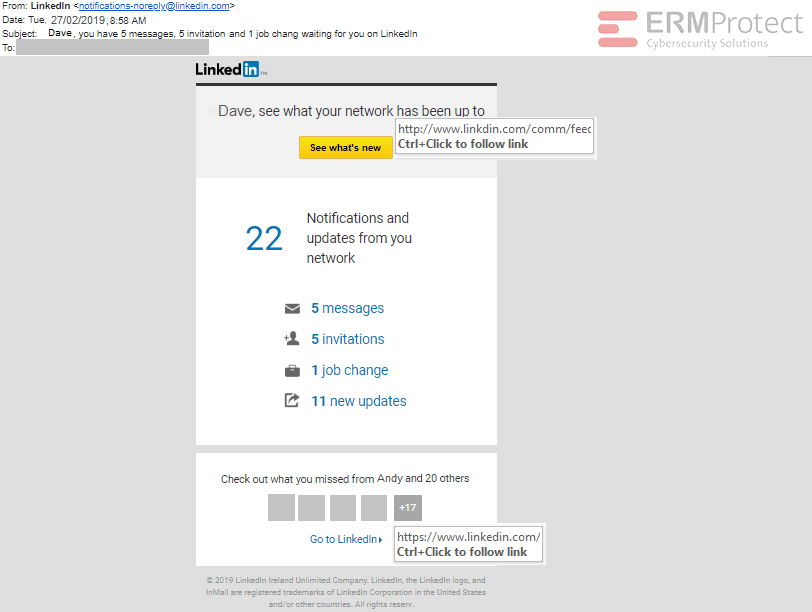
Count the Phish: LinkedIn Email
The LinkedIn email below is an attempted phishing attack. There are quite a few red flags in there. Let’s see if you can find them all!
Answer:
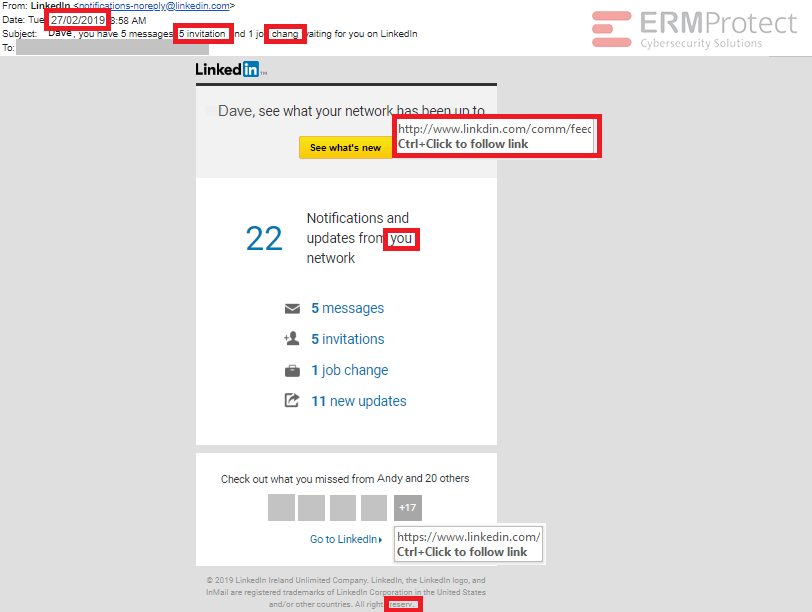
There are 6 red flags in total.
- The date is in a non-US format.
- The subject of the email has one grammatical and one spelling
- In the body of the email, the very first hyperlink has a phishy domain name. It says ‘www.linkdin.com,’ so as you can see the letter “e” is missing.
- The writeup in the center of the email also has a grammatical error.
- And lastly, the footer of the email has a spelling mistake.
When reviewing an email, never rely on one indicator alone. Review the email as a whole and see if it sets off any alarms in your mind, which may look like a possible phishing attack.

Get a curated briefing of the week's biggest cyber news every Friday.

Turn your employees into a human firewall with our innovative Security Awareness Training.
Our e-learning modules take the boring out of security training.
Intelligence and Insights

Are You Prepared for an AI-Powered Cyber Attack?
The question is no longer whether AI will impact cybersecurity, but whether organizations are prepared for the reality of AI-powered cyberattacks …

AI Privacy Risks
Users face a range of privacy concerns with AI – from models training on sensitive user data to attackers using AI tools to study their targets …

The Risk of the AI Notetaker
While AI notetakers can enhance efficiency, their adoption introduces serious risks for organizations, mainly surrounding data privacy, regulatory compliance, reputational harm, and AI security …