Spot the Phish: eCommerce Promotions
The images displayed below are a combination of images which are phishing attacks and real images. Challenge your cybersecurity awareness and spot which ones are real and which ones are phony:
Spoiler Alert: Answers are below.
Answer: Images 2 and 3 are phishes. Let’s see why:
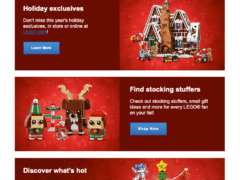
Image 1 details: The image shows an email from Lego with Christmas deals. No obvious red flags stand out.
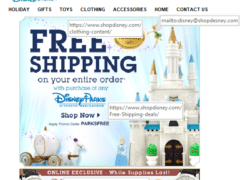
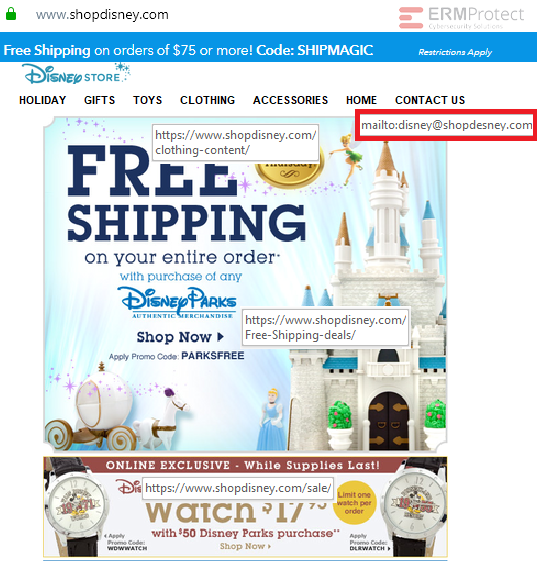
Image 2 details: The image is purportedly that of the Disney online store. The website has several hyperlinks to take you to linked pages. While most of the links appear legit, take a look at the “Contact Us” link. Clicking that will load your default mail client to send an email to that email address. The “shopdesney.com” domain in that address is clearly a fake. An email sent to this address will likely end up being the first of many exchanges where the scammer will launch cyber attacks and try to steal your money, information, or both. This one is a phishing attack!
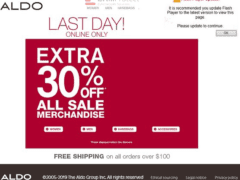
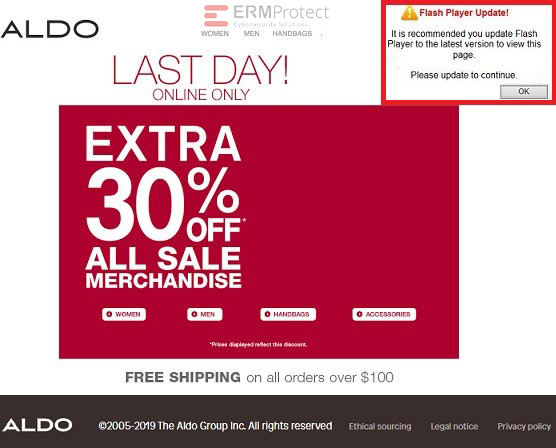
Image 3 details: This is a clear phish. You may have noticed the “Flash Player Update” pop-up on the website. Flash, ActiveX, and other such active website components are easy for hackers to infect and launch a cyber attack. If you see a message like this, chances are that either the website or your browser may be have been targeted by a malicious hacker and a victim of a phishing attack.
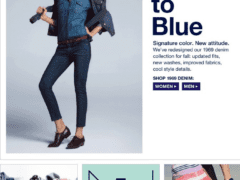
Image 4 details: This one doesn’t appear to have any red flags or signs of a cyber attack. Looks legit.

Get a curated briefing of the week's biggest cyber news every Friday.

Turn your employees into a human firewall with our innovative Security Awareness Training.
Our e-learning modules take the boring out of security training.
Intelligence and Insights

Cybersecurity Blind Spot: Why Physical Security Is Now the Easiest Way In

Red, Blue, & Purple Teaming: Unified Strategy Organizations Can’t Ignore