Spot the Phishing Attempt
The images displayed below are a combination of real and phishing sites. Spot the phish! Click on the images to zoom in.
Spoiler Alert: Answers are below.
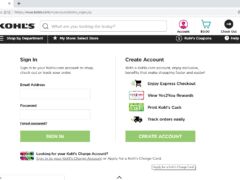
Answer: Image 1 shows a real website. The others are phishes! Let’s take a look below…
Image 1 details: The image passes our link checks, format checks, and grammar checks. Nothing seems amiss.
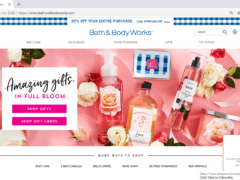
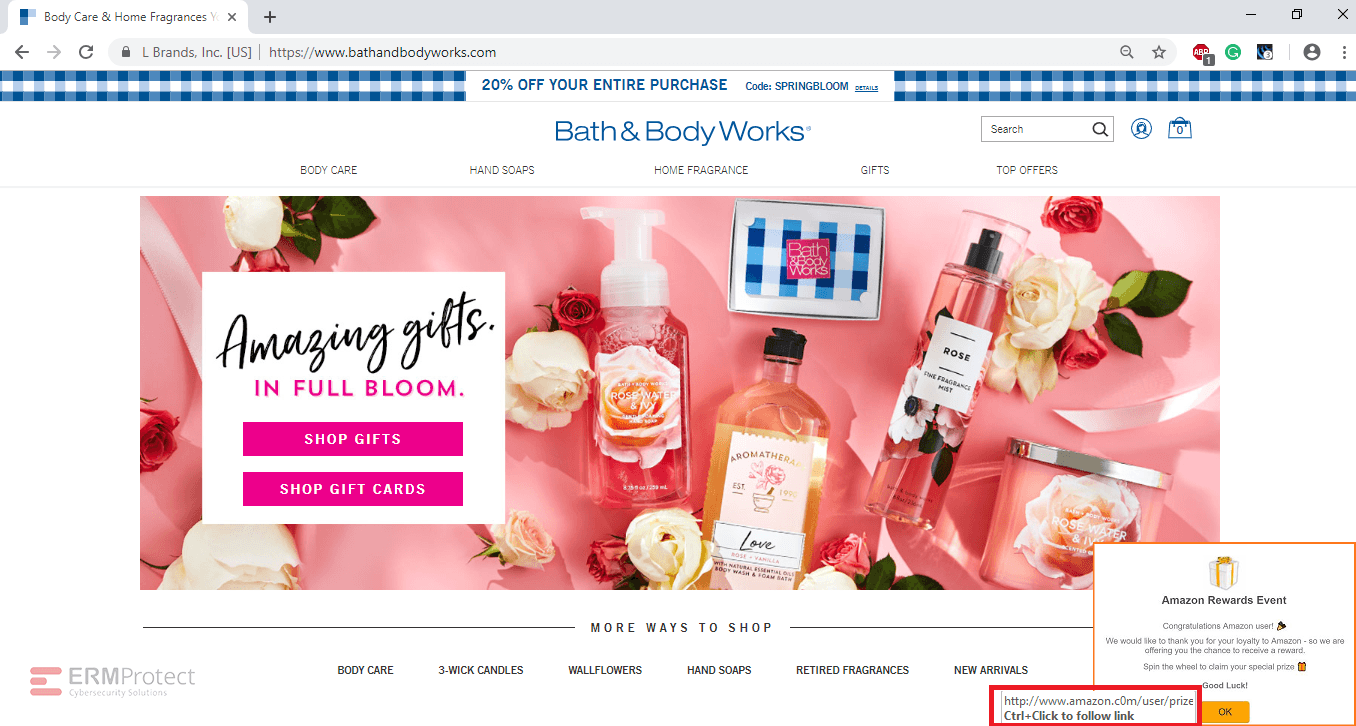
Image 2 details: The biggest giveaway is the ‘Amazon Rewards Event’ pop up ad. The hyperlink in the ad has a spoofed domain: amazon.com is replaced by amazon.c0m. Remember, even if the main site you’re visiting is a reputable one, it doesn’t mean you should trust the ads and pop-ups as well. Hackers can place malicious ads on sites and redirect you to a bad website. Never let your guard down. Inspect pop-ups and ads as closely as you would an email or website.
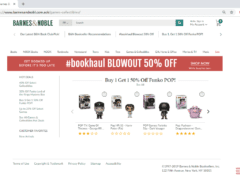
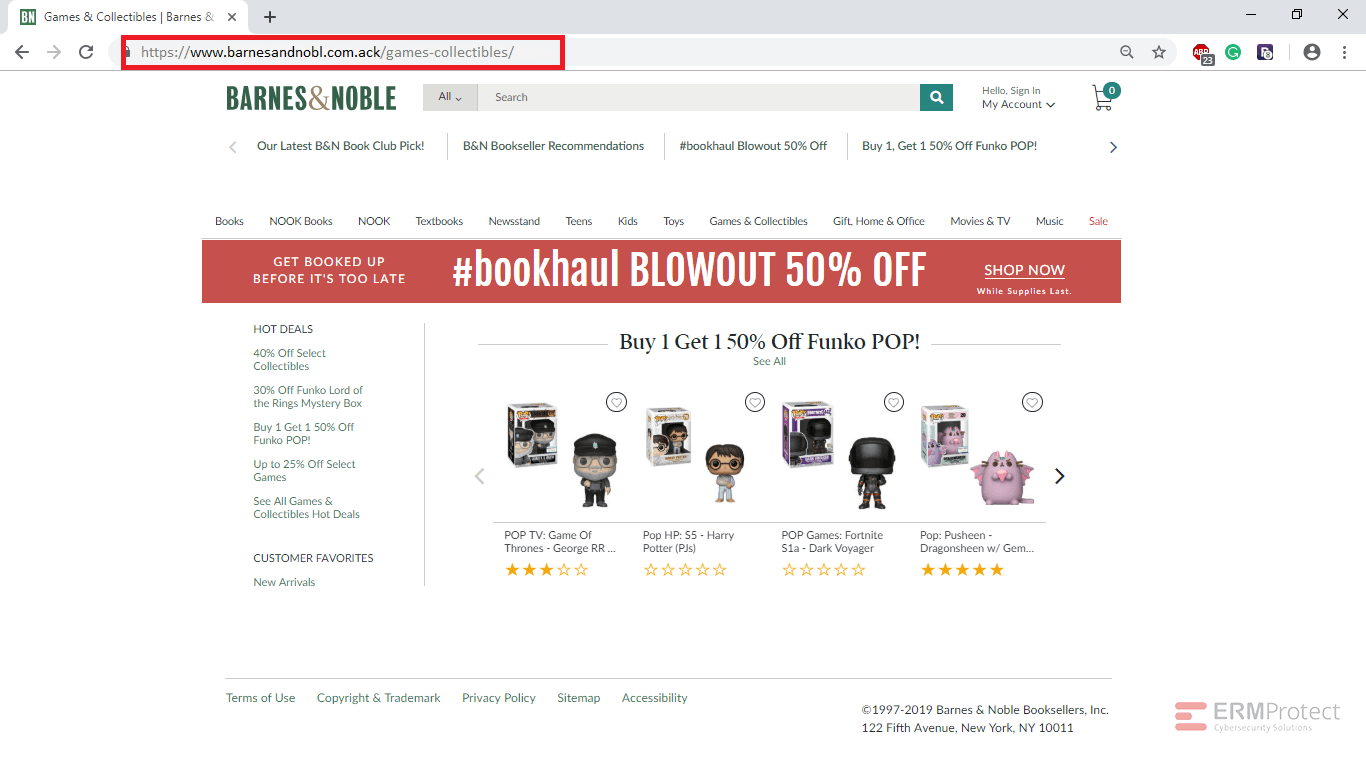
Image 3 details: The URL of the website has typo – “nobl.” Also, the URL has a weird multi domain – ‘.com.ack.’ What professional organization would have such a domain? There is absolutely no need to perform a link check on this one. Totally phishy!
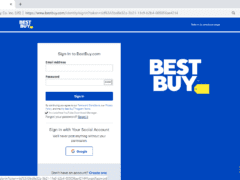
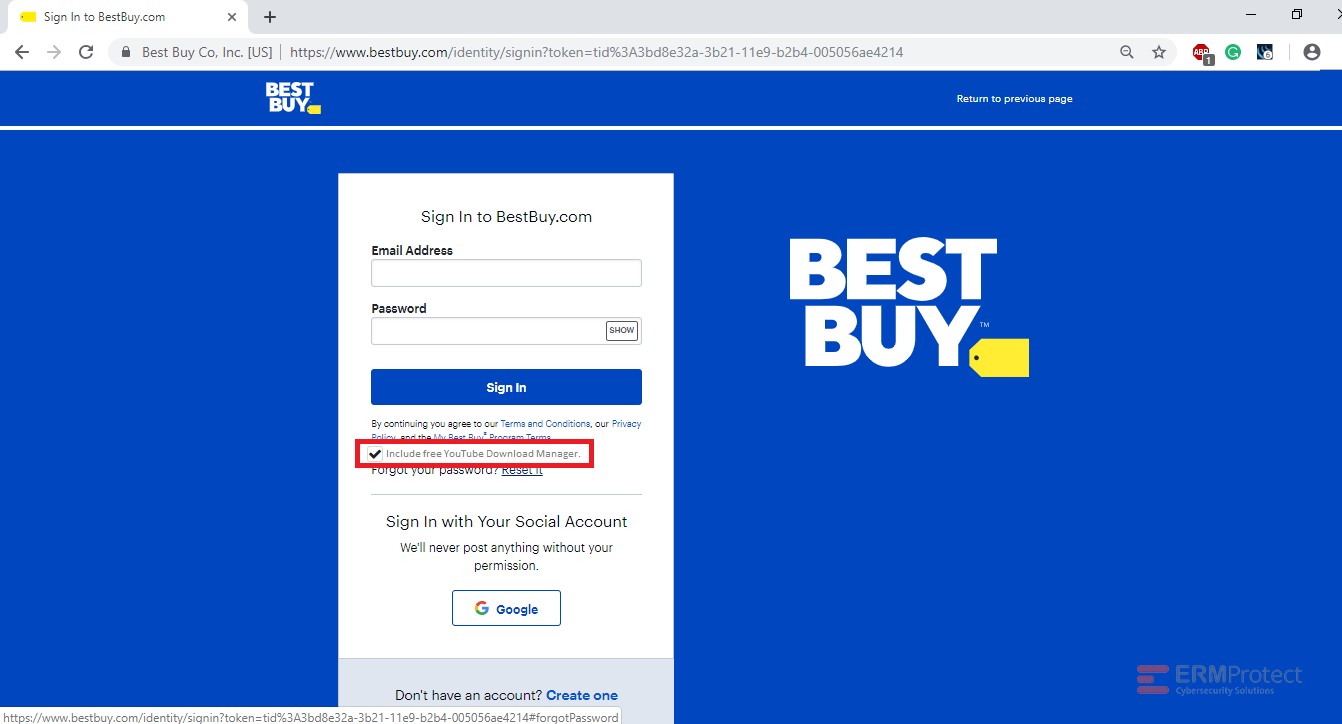
Image 4 details: Now, this is a tricky one. There are no typos, spelling or grammatical errors and even the URL looks good. The only giveaway is that one of the checkboxes says: “Include free YouTube Download Manager.” A pre-checked tool download option is an immediate red flag! If you’re in a hurry and accidentally forget to uncheck the box, it might trigger an adware or malware download in the background that adversely affects your computer and leads to a compromise of your personal or sensitive organizational information.

Turn your employees into a human firewall with our innovative Security Awareness Training.
Our e-learning modules take the boring out of security training.

Get a curated briefing of the week's biggest cyber news every Friday.
Intelligence and Insights

Quantum Computing Puts Today’s Encryption at Risk

Are You Prepared for an AI-Powered Cyber Attack?