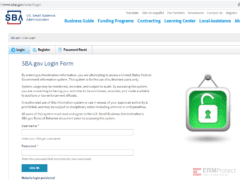
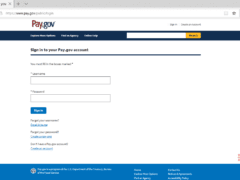
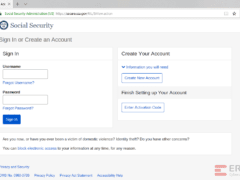
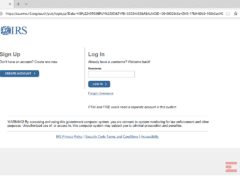
Which of these are phishing attempts?
The images displayed below are a combination of phishing and real emails. Spot which ones are real and which ones are phony:
Spoiler Alert: Answers are below.
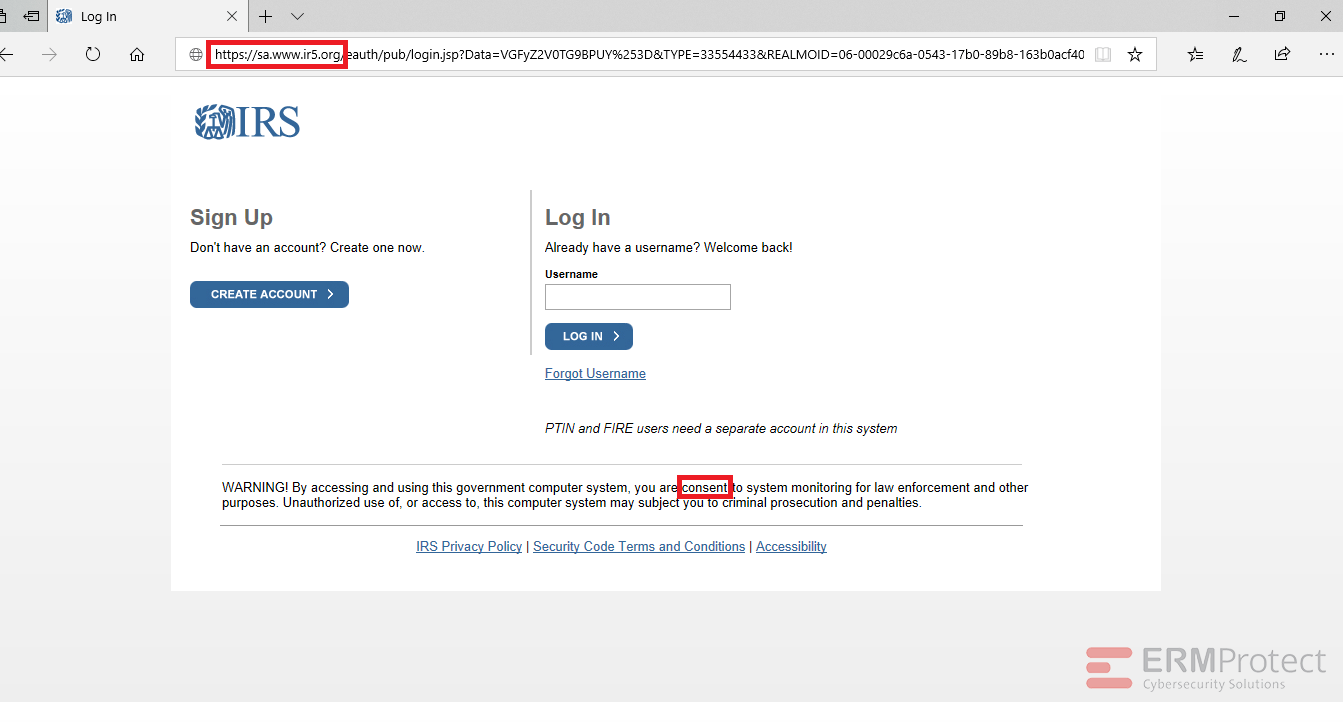
Answer: Image number 4 is the only phish. Let’s take a look.
Image 4 details: The biggest giveaway is the phony domain in the link. The real domain is “irs.gov” but this one says “ir5.org.” Remember that hackers will try to make a URL look as similar as possible to the real one to increase chances you will overlook it. There is also a minor grammatical mistake in the “WARNING!” section of the website. It says you are “consent” rather than “consenting” to system monitoring. The phishy signs can hide in the tiniest of places!

Get a curated briefing of the week's biggest cyber news every Friday.

Turn your employees into a human firewall with our innovative Security Awareness Training.
Our e-learning modules take the boring out of security training.
Intelligence and Insights

Red, Blue, & Purple Teaming: Unified Strategy Organizations Can’t Ignore

Quantum Computing Puts Today’s Encryption at Risk