Spot the Phishing Attempt - Cybersecurity Awareness
The images below are a combination of phishing emails and real emails related to job search and professional networking sites. Spot The Phish! Click on the images to zoom in.
Spoiler Alert: Answers are below.
Answer: Image 1 and Image 3 are the real ones. And the rest are phishes. Take a look below...
Image 1 details: The email comes from a linkedin.com sender domain. The links in the email pass our cybersecurity link checks. They’re not masquerading or fake domains.
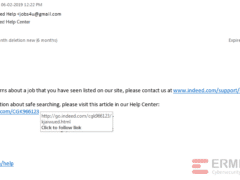
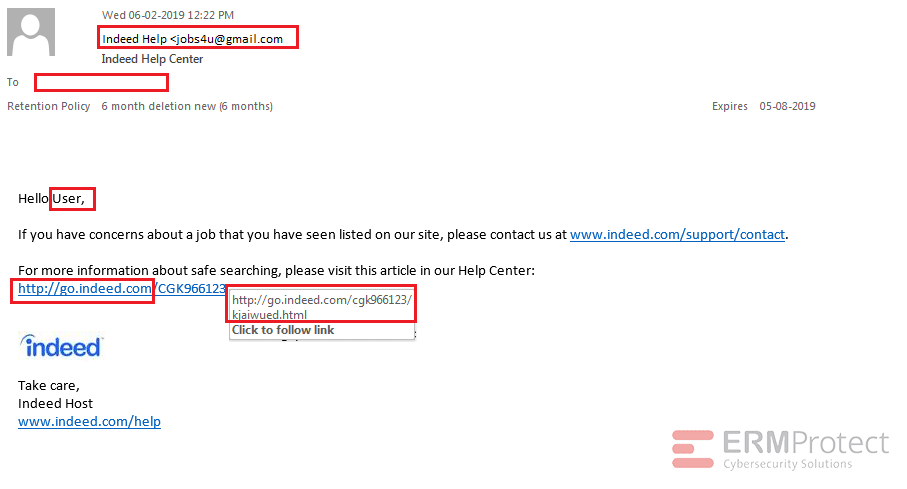
Image 2 details: There are a lot of phishy indicators in this email. The sender sends the email from a gmail.com domain versus an indeed.com domain. The “To” field is empty, meaning that this was probably an email that was sent out in bulk. The salutation used is very generic, which isn’t typical of professional organizations. Yes, the link domain is an indeed.com domain - but remember that there are several ways hackers can redirect you to a malicious domain once you click on this link. So, when it comes to cybersecurity awareness, never rely on only one indicator. Review the email in its entirety to see if it sets off any alarms.
Image 3 details: The email comes from a legitimate domain (careerbuilder.com). The look and feel of the email seem legitimate as well. There are no red flags in terms of outdated logos, poor grammar, or other formatting oversights. The link includes a legitimate domain, as well. Overall, no cybersecurity red flags in sight.
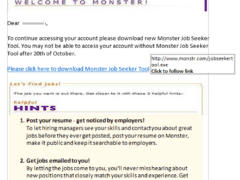
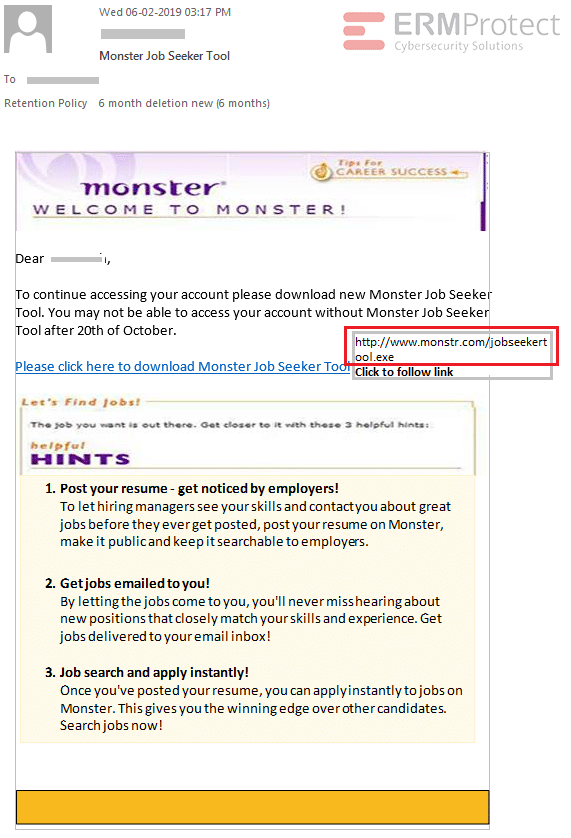
Image 4 details: The biggest giveaway is the phony domain in the link. There’s an “e” missing in the domain name. Further, take a closer look at the link. It’s actually an executable file as can be seen from “.exe” extension at the end. The logo is outdated as well. This one’s an attempt at a phishing attack!

Get a curated briefing of the week's biggest cyber news every Friday.

Turn your employees into a human firewall with our innovative Security Awareness Training.
Our e-learning modules take the boring out of security training.
Intelligence and Insights

Are You Prepared for an AI-Powered Cyber Attack?

AI Privacy Risks