Spot the Phishing Attempt - Cybersecurity Awareness
The images displayed below are a combination of phishing attacks and real websites. Spot which ones are real and which ones are phony:
Spoiler Alert: Answers are below.
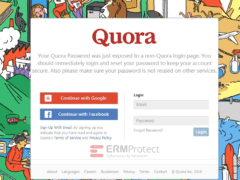
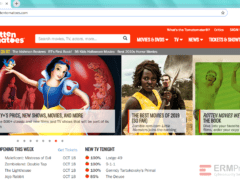
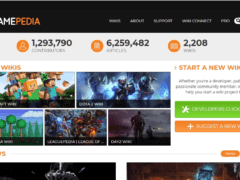
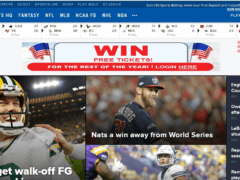
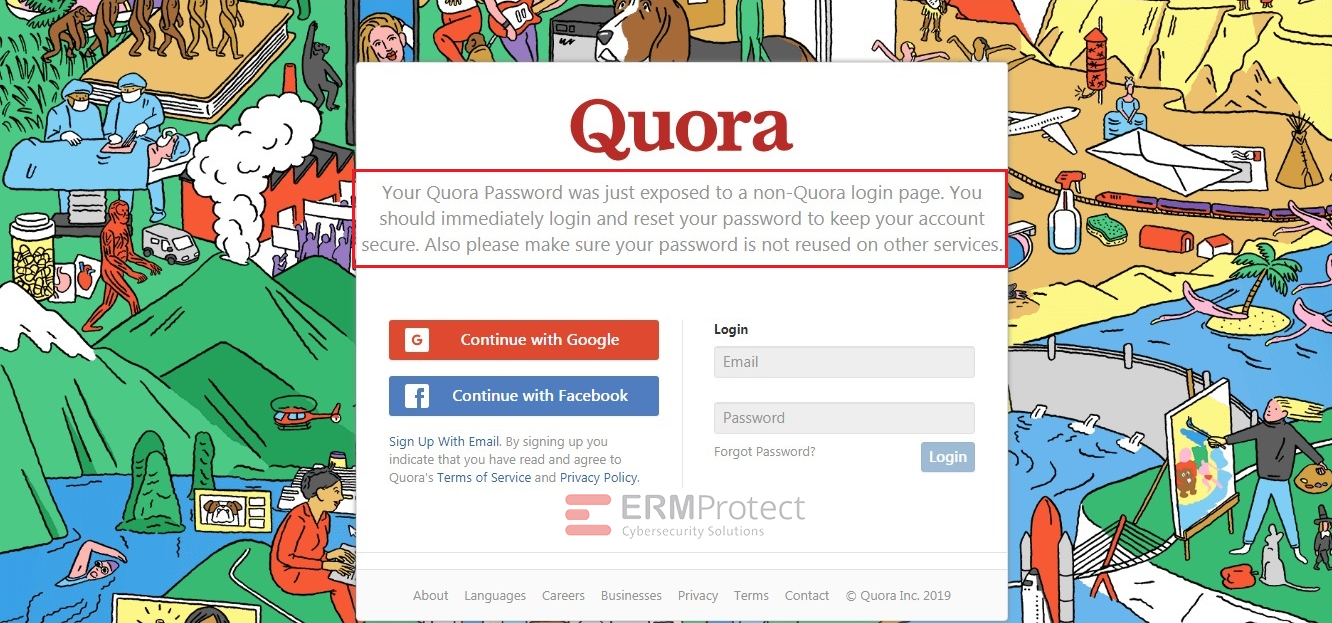
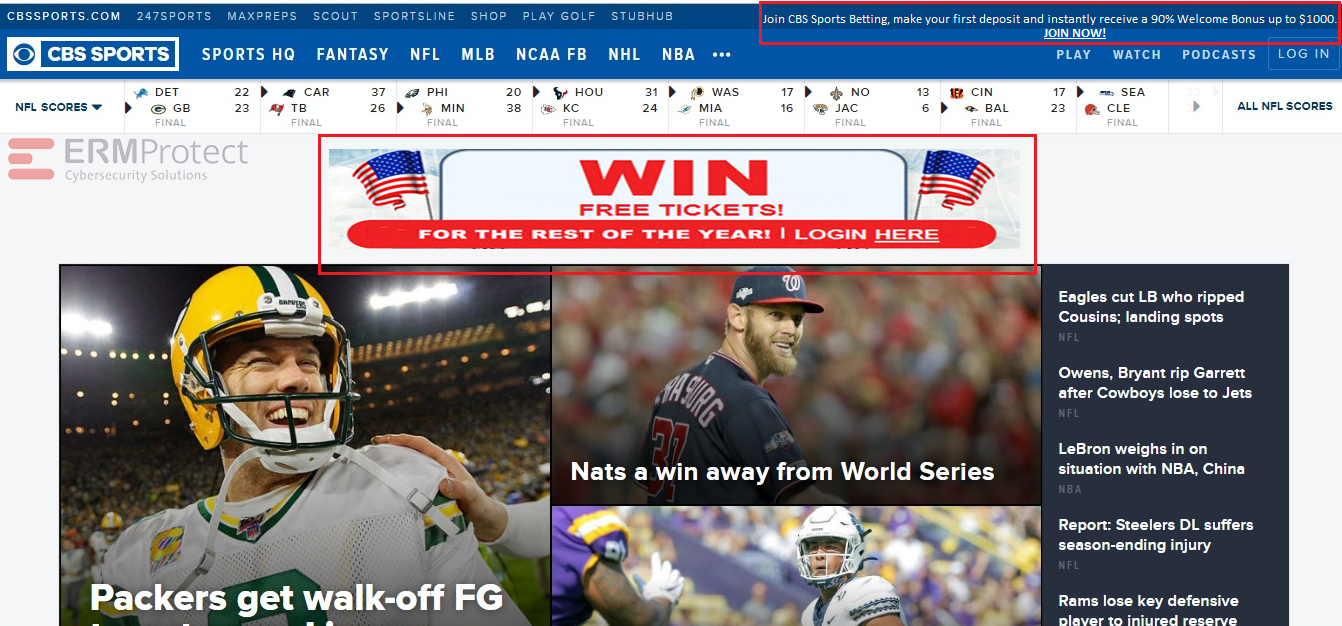
Answer: Images 1 and 4 are phishes. The rest are real. Let’s take a look.
Image 1 details: The Quora webpage asks users to login immediately and reset their password as their “password has been exposed on a non-Quora login page.” This should immediately raise cybersecurity awareness. Fist, this is not how any reputable organization would go about this process, even if there were such a password breach. Second, it’s asking users to reset the password by logging in using the same credentials that it claims were breached! That doesn’t make sense.
Image 2 & Image 3 details: These pages pass all our typical link, format, and grammar checks. Nothing seems amiss. Chances are high that they’re not phishes.
Image 4 details: The ad on this page is clearly phishy, not just by the way it looks but based on the hard-to-believe prize it offers. Remember: Even if a website is trustworthy, the ads on it might not be. Also, the offer on the top-right corner of the webpage looks too good to be true, looks like an attempt at a phishing attack

Get a curated briefing of the week's biggest cyber news every Friday.

Turn your employees into a human firewall with our innovative Security Awareness Training.
Our e-learning modules take the boring out of security training.
Intelligence and Insights

Cybersecurity Blind Spot: Why Physical Security Is Now the Easiest Way In

Red, Blue, & Purple Teaming: Unified Strategy Organizations Can’t Ignore