What Banks Need to Do Now to Replace the FFIEC’s Cybersecurity Assessment Tool (CAT)
By Rey LeClerc Sveinsson, PhD
The Federal Financial Institutions Examination Council (FFIEC) has officially announced that its Cybersecurity Assessment Tool (CAT) will be retired on August 31, 2025. This marks a significant shift in how financial institutions are expected to assess their cybersecurity maturity and preparedness going forward. This article explains alternative frameworks banks can use to replace the FFIEC CAT and remain compliant.
Background on the FFIEC Cybersecurity Assessment Tool (CAT)
Introduced in June 2015, the FFIEC CAT was developed as a voluntary but widely adopted framework that enabled financial institutions to identify their inherent cybersecurity risks and assess their cybersecurity maturity.
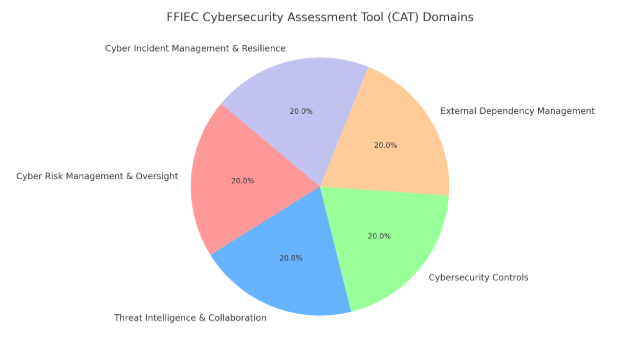
The tool provided a structured methodology, allowing banks and credit unions to evaluate their security posture across key domains, including:
- Cyber risk management and oversight
- Threat intelligence and collaboration
- Cybersecurity controls
- External dependency management
- Incident response and resilience
For nearly a decade, the FFIEC CAT has been instrumental in helping financial institutions meet regulatory expectations while providing a consistent approach for cybersecurity self-assessment.
Many organizations integrated the tool into their risk management programs, using it to benchmark security practices, identify gaps, and prioritize improvements.
Why Is the FFIEC Retiring the CAT?
The decision to retire the FFIEC CAT reflects the rapid evolution of cybersecurity threats and regulatory expectations in the financial sector. Since 2015, cyber risks have become more sophisticated and pervasive, requiring a more dynamic and adaptable approach to cybersecurity assessment.
Additionally, financial regulators and industry groups have increasingly encouraged the adoption of more comprehensive cybersecurity frameworks that offer greater flexibility, scalability, and alignment with global best practices.
The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) and other industry-recognized frameworks have gained prominence as more robust alternatives.
What This Means for Banks and Financial Institutions
With the CAT's retirement, banks and financial institutions will need to transition to alternative cybersecurity assessment frameworks to ensure compliance, resilience, and effective risk management.
The FFIEC has not mandated a specific replacement framework but has encouraged institutions to evaluate options that best fit their size, complexity, and risk profile.
Regulatory agencies, including the Office of the Comptroller of the Currency (OCC), the Federal Reserve, and the Federal Deposit Insurance Corporation (FDIC), will likely assess financial institutions’ cybersecurity practices based on broader industry standards rather than the FFIEC CAT.
Key FFIEC Risk Assessment Considerations for Banks Moving Forward
As the FFIEC Cybersecurity Assessment Tool (CAT) is phased out, banks must take proactive steps to ensure a seamless transition to alternative cybersecurity assessment frameworks that align with regulatory expectations and the evolving threat landscape.
This transition is not just about compliance, it is an opportunity to enhance cybersecurity resilience, improve risk management, and adopt a more proactive stance against cyber threats.
Below are four key considerations that financial institutions should prioritize to ensure a successful transition.
1. Evaluate Alternative Frameworks
Financial institutions should explore and adopt alternative cybersecurity frameworks that offer greater flexibility, depth, and adaptability in risk assessment and management. Several leading frameworks can provide the structure needed for a robust cybersecurity program:
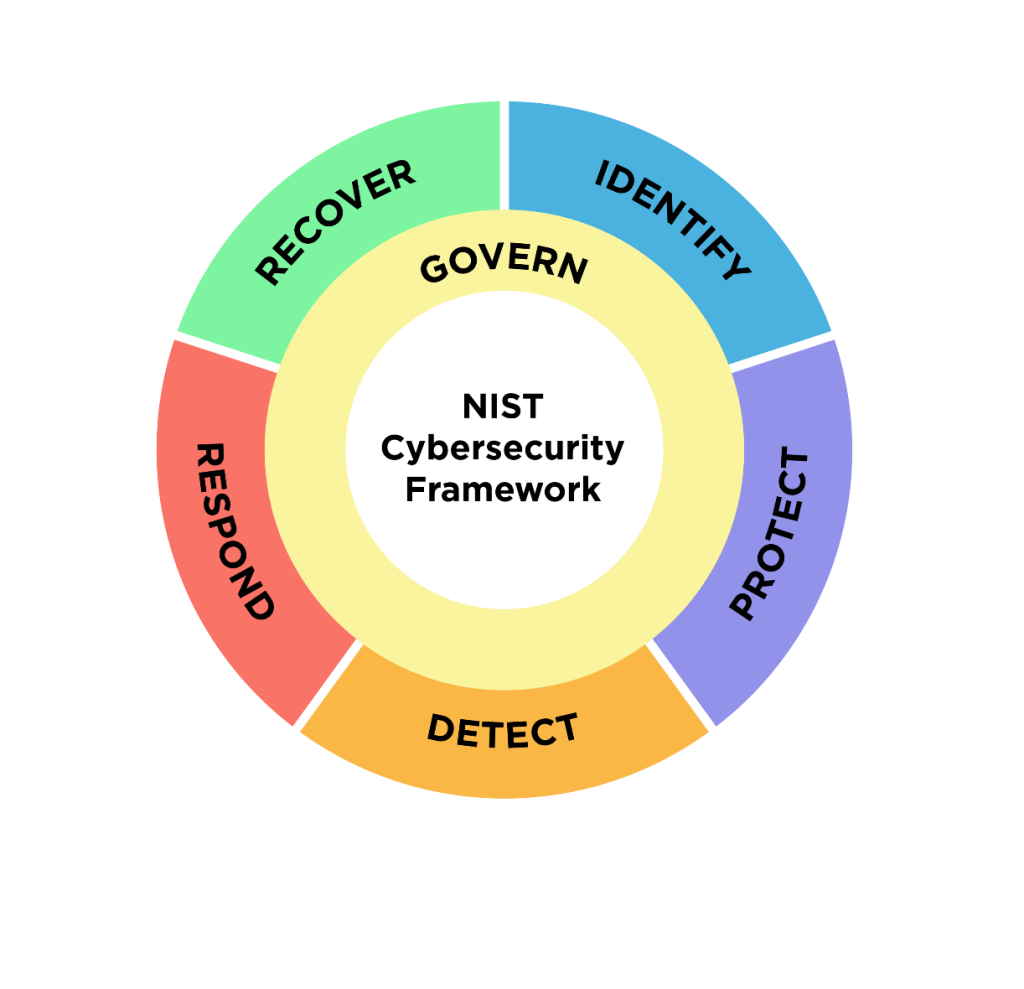
- NIST Cybersecurity Framework (CSF) 2.0 – Developed by the National Institute of Standards and Technology (NIST), the CSF is one of the most widely recognized cybersecurity frameworks. For banks exploring cybersecurity assessment frameworks, the NIST Cybersecurity Framework (CSF) 2.0 offers a well-structured, industry-recognized approach to cybersecurity risk management. The updated version (CSF 2.0) includes six core functions — Govern, Identify, Protect, Detect, Respond, and Recover — providing financial institutions with a flexible yet comprehensive strategy for mitigating cyber risks. Many financial institutions already leverage NIST CSF due to its alignment with regulatory requirements and scalability across different business sizes.
- CIS Critical Security Controls (CIS Controls) – The Center for Internet Security (CIS) has developed a set of 18 prioritized cybersecurity controls that help organizations defend against common cyber threats. CIS Controls provide practical, actionable guidance and are categorized into Implementation Groups (IGs) to help organizations of varied sizes and risk profiles prioritize security efforts.
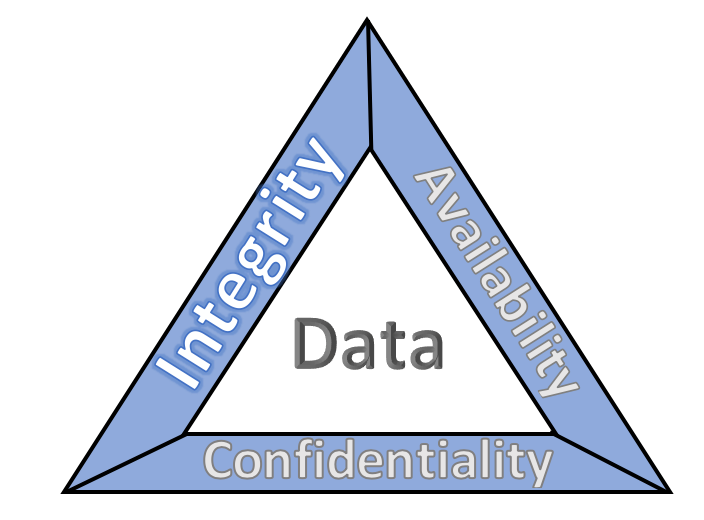
- ISO/IEC 27001 – This international standard, developed by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC), outlines best practices for information security management systems (ISMS). It provides a structured framework for managing cybersecurity risks, ensuring confidentiality, integrity, and availability of information assets. Achieving ISO 27001 certification can also enhance a bank’s credibility and demonstrate compliance with global security standards.
- Cyber Risk Institute (CRI) Profile – Tailored specifically for the financial sector, the CRI Profile integrates multiple regulatory requirements and industry frameworks (including NIST CSF and FFIEC guidance) into a unified, standardized assessment methodology. This framework helps banks streamline compliance efforts and align cybersecurity practices with regulatory expectations.
- CISA Cybersecurity Performance Goals (CPGs) – The Cybersecurity and Infrastructure Security Agency (CISA) has developed baseline cybersecurity performance goals that serve as a starting point for financial institutions looking to enhance their security posture. These goals align with NIST CSF and help organizations focus on key security priorities, such as asset management, access control, and incident response.
By selecting and implementing a robust, industry-recognized framework, banks can ensure regulatory compliance, improve security posture, and build resilience against cyber threats.
2. Perform a Gap Analysis
Once a bank identifies the most suitable cybersecurity framework, it is crucial to assess current cybersecurity maturity and perform a gap analysis between the existing FFIEC CAT-based assessments and the new framework. This process involves:
- Mapping the FFIEC CAT components to the new framework to identify overlaps and deficiencies.
- Evaluating existing security controls to determine whether they meet the requirements and recommendations of the chosen framework.
- Identifying gaps and weaknesses in cybersecurity policies, procedures, and technical controls.
- Developing an action plan to address identified deficiencies, ensuring a structured and methodical approach to framework adoption.
Conducting a thorough gap analysis will help financial institutions avoid disruptions in compliance and risk management, allowing for a smooth, well-planned transition to a new cybersecurity framework that meets both regulatory and business needs.
3. Enhance Cyber Resilience Strategies
With cyber threats increasing in frequency and sophistication, banks must move beyond traditional compliance-driven assessments and focus on proactive cybersecurity strategies.
The financial sector remains a prime target for cybercriminals, and institutions must adopt holistic resilience measures to protect against threats such as ransomware, data breaches, insider threats, and supply chain attacks.
Key elements of a strong cyber resilience strategy include:
- Continuous Monitoring and Threat Intelligence – Implement real-time monitoring to detect and respond to threats before they cause considerable damage. Leverage threat intelligence feeds, anomaly detection, and advanced analytics to stay ahead of cyber adversaries.
- Incident Response and Recovery Planning – Develop and regularly test an incident response plan to ensure a rapid, coordinated, and effective response to cyber incidents. Banks should also establish business continuity and disaster recovery (BC/DR) plans to minimize downtime and financial losses in case of an attack.
- Zero Trust Architecture (ZTA) – Implement a Zero Trust approach by enforcing strict access controls, least privilege principles, and continuous verification of users and devices. This approach reduces the risk of unauthorized access and lateral movement of threats within the network.
- Third-Party Risk Management – Given the increasing reliance on third-party vendors and cloud services, banks must establish robust third-party risk management programs to assess vendor security practices, enforce contractual cybersecurity obligations, and continuously monitor vendor risks.
By integrating proactive defense mechanisms and resilience strategies, financial institutions can significantly strengthen their cybersecurity posture and reduce their exposure to emerging threats.
4. Engage with Regulators and Industry Groups
Cybersecurity in the financial sector is heavily regulated, and maintaining alignment with regulatory expectations is critical. Banks must actively engage with regulators and participate in industry groups to stay informed on emerging threats, evolving compliance requirements, and best practices.
Key actions include:
- Monitoring guidance from financial regulatory bodies such as the FFIEC, OCC, FDIC, Federal Reserve, and SEC to ensure ongoing compliance.
- Participating in cybersecurity forums, working groups, and information-sharing initiatives such as the Financial Services Information Sharing and Analysis Center (FS-ISAC), which provides threat intelligence and fosters industry collaboration.
- Engaging with cybersecurity policymakers and regulators to provide input on evolving security standards and to gain insights into future regulatory trends.
- Leveraging cybersecurity partnerships with organizations such as CISA, NIST, and industry-specific cybersecurity alliances to enhance security readiness.
By actively participating in regulatory discussions and industry initiatives, banks can stay ahead of compliance changes, implement best-in-class security controls, and strengthen their cybersecurity posture in a rapidly evolving digital landscape.
5. Engage Stakeholders
Successful implementation of a new cybersecurity framework requires strong organizational buy-in from all relevant stakeholders. Cybersecurity is no longer just an IT issue — it is a business-critical function that involves risk management, regulatory compliance, and operational decision-making.
To ensure effective stakeholder engagement, banks should:
- Involve Executive Leadership and the Board – Cybersecurity decisions impact financial stability, regulatory compliance, and customer trust. Engaging board members, senior executives, and risk committees in the decision-making process ensures that cybersecurity remains a strategic priority.
- Collaborate with IT and Security Teams – The IT security department and risk management teams will be responsible for implementing technical controls, policies, and monitoring measures. They must be actively involved in assessing the new framework’s feasibility and impact.
- Coordinate with Compliance and Legal Teams – Financial institutions operate under strict regulatory scrutiny, and compliance officers must ensure that the new framework aligns with legal and regulatory requirements. A well-integrated approach prevents compliance risks and regulatory penalties.
- Educate and Train Employees – Cybersecurity awareness training should be an essential part of the transition process. Employees must understand how new security policies and controls affect their roles and be trained on best practices to reduce human error and insider threats.
FFEIC Risk Assessment for Financial Institutions
The CAT retirement presents a critical opportunity for financial institutions to rethink and modernize their cybersecurity assessment strategies. By evaluating alternative frameworks, conducting thorough gap analyses, strengthening cyber resilience strategies, and engaging with regulators and industry groups, banks can not only maintain compliance but also enhance their overall security maturity.
Institutions that embrace this transition as an opportunity to strengthen cybersecurity maturity will be well-positioned to navigate the future of financial sector cybersecurity with confidence and resilience.
How ERMProtect Can Help Banks Navigate the FFIEC CAT Transition
As banks transition away from the FFIEC Cybersecurity Assessment Tool (CAT) and adopt more comprehensive cybersecurity frameworks, the process can be overwhelming. Institutions must carefully evaluate alternative frameworks, perform detailed gap analyses, engage stakeholders — all while ensuring ongoing regulatory compliance.
ERMProtect, with its deep expertise in cybersecurity risk management, compliance, and threat mitigation, is uniquely positioned to help financial institutions navigate this transition smoothly and effectively.
ERMProtect provides expert guidance in selecting and implementing the right cybersecurity framework for your institution’s specific needs. Our team of cybersecurity professionals, risk analysts, and compliance experts helps banks ensure that the chosen methodology aligns with regulatory requirements and business objectives.
Our customized framework mapping and implementation strategy allows banks to transition seamlessly while maintaining the highest level of security and compliance.
We start with a comprehensive gap analysis to identify security vulnerabilities, control deficiencies, and areas for improvement. By comparing current cybersecurity practices against the requirements of the new framework, we provide a clear, actionable roadmap to strengthen security controls, improve cyber resilience, and meet compliance obligations.
Our risk-based approach ensures that banks prioritize the most critical security enhancements, reducing potential threat exposure and financial risks.
In addition, our penetration testing and incident response planning provides banks with real-time visibility into potential vulnerabilities and attack vectors. By implementing AI-driven security analytics, threat hunting, and robust incident response protocols, we help financial institutions stay ahead of emerging cyber threats and regulatory changes.
Furthermore, we assist with policy development, third-party risk management, regulatory reporting, and cybersecurity training, ensuring that your institution is well-prepared for audits and examinations.
By partnering with ERMProtect, financial institutions can confidently transition to a modern cybersecurity framework, enhance their security posture, and meet evolving regulatory expectations.
ERMProtect is here to guide you every step of the way. For a free FFIEC risk assessment consultation or more information, please contact [email protected], [email protected] or call us at 305-447-6750.
About the Author
Dr. Rey Leclerc Sveinsson is an expert in Privacy and Data Protection, Information Security, and Technology Governance, Risk & Compliance (IT GRC). He has developed information assurance programs for major organizations globally during his career as well as serving as a Consultant for ERMProtect. He has a PhD in Information Systems and multiple master’s degrees in the areas of privacy, information technology, and cybersecurity laws.
Subscribe to Our Weekly Newsletter

Turn your employees into a human firewall with our innovative Security Awareness Training.
Our e-learning modules take the boring out of security training.
Intelligence and Insights

Cybersecurity Blind Spot: Why Physical Security Is Now the Easiest Way In

Red, Blue, & Purple Teaming: Unified Strategy Organizations Can’t Ignore