How SOC2+ Additional Subject Matter Assessments Save Organizations Time and Money to Meet Compliance Objectives
SOC 2 examinations are used by many organizations today to obtain an independent and thorough understanding of the security control structure and detailed security control measures of third-party service providers. A “SOC2+ Additional Subject Matter Assessment” allows experts to assess compliance with SOC2 while at the same time reviewing compliance with other privacy laws, standards and regulations such as HIPAA, PCI, GDPR etc.
SOC 2+ provides one integrated internal control report addressing key regulatory risks. It allows third-party service providers to take advantage of the synergies of overlapping control frameworks and satisfy their customers’ evolving control requirements. This has the potential to reduce overall compliance costs and efforts as SOC 2+ reports create substantial efficiencies for organizations.
Issues such as repetitive testing per year, contracting of multiple firms to perform different audits, additional tracking of controls, and other nuances that come with multiple compliance efforts can be greatly reduced and addressed in one report.
Below is a table highlighting the Additional Subject Matters that can be included in a SOC2+:

Turn your employees into a human firewall with our innovative Security Awareness Training.
Our e-learning modules take the boring out of security training.
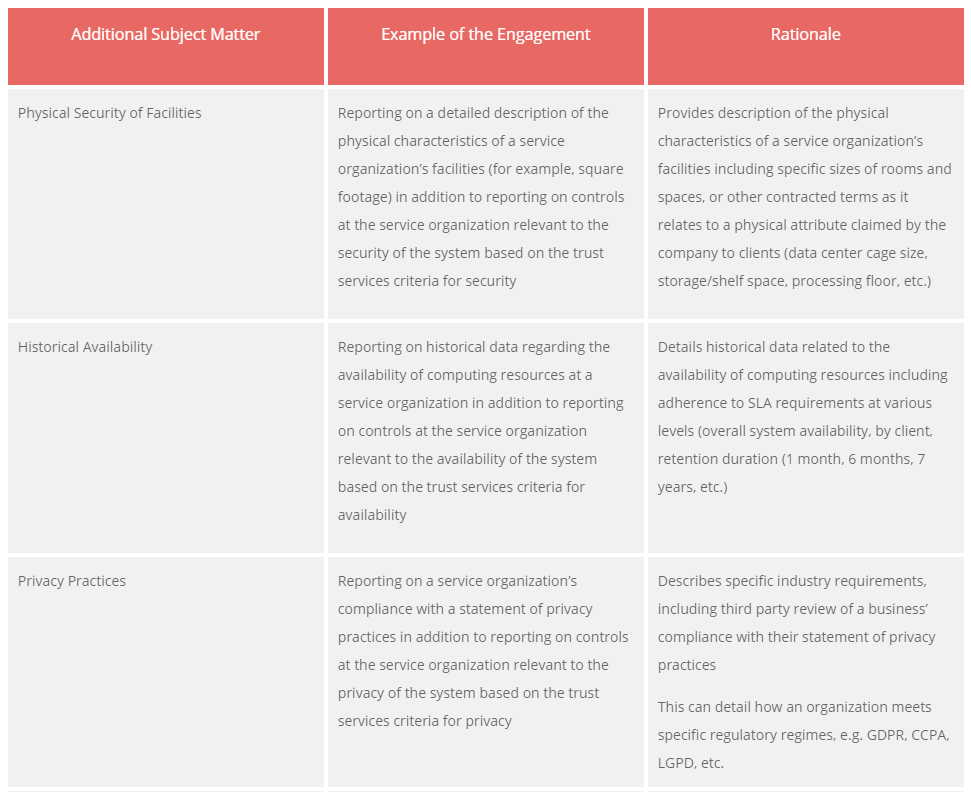
Additional Subject Matter
Example of the Engagement
Rationale
Physical Security of Facilities
Reporting on a detailed description of the physical characteristics of a service organization’s facilities (for example, square footage) in addition to reporting on controls at the service organization relevant to the security of the system based on the trust services criteria for security
Provides description of the physical characteristics of a service organization’s facilities including specific sizes of rooms and spaces, or other contracted terms as it relates to a physical attribute claimed by the company to clients (data center cage size, storage/shelf space, processing floor, etc.)
Historical Availability
Reporting on historical data regarding the availability of computing resources at a service organization in addition to reporting on controls at the service organization relevant to the availability of the system based on the trust services criteria for availability
Details historical data related to the availability of computing resources including adherence to SLA requirements at various levels (overall system availability, by client, retention duration (1 month, 6 months, 7 years, etc.)
Privacy Practices
Reporting on a service organization’s compliance with a statement of privacy practices in addition to reporting on controls at the service organization relevant to the privacy of the system based on the trust services criteria for privacy
Describes specific industry requirements, including third party review of a business’ compliance with their statement of privacy practices
This can detail how an organization meets specific regulatory regimes, e.g. GDPR, CCPA, LGPD, etc.
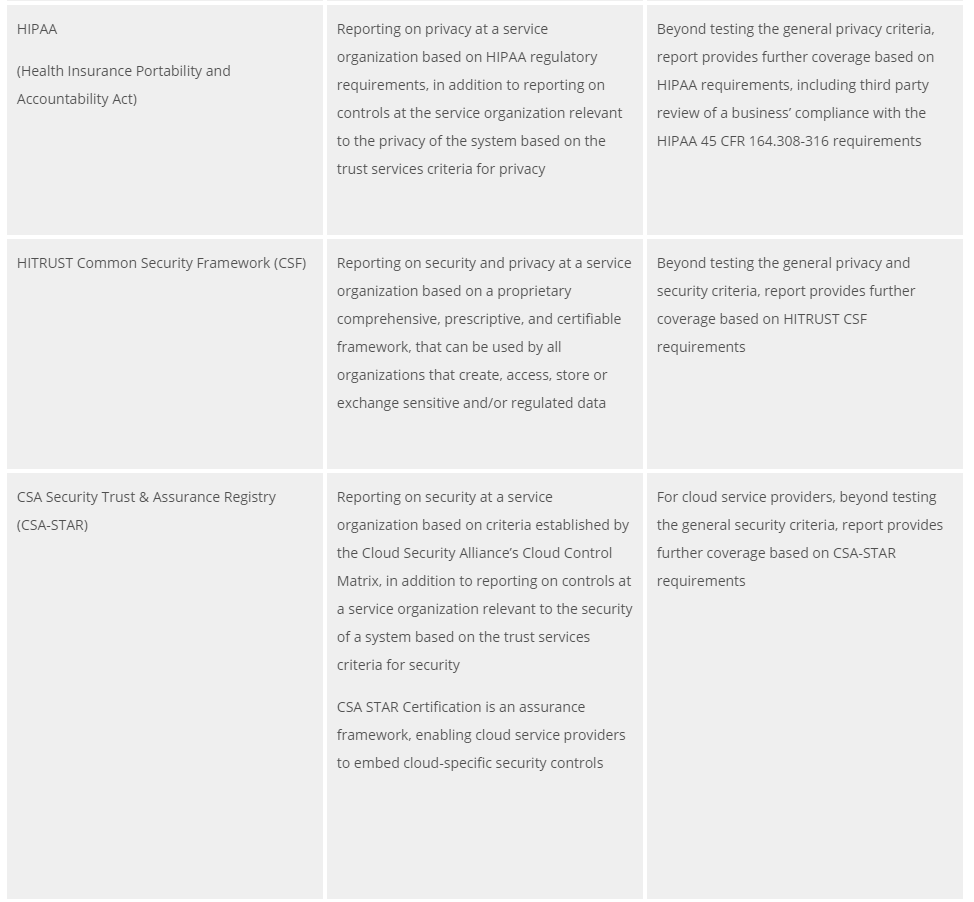
HIPAA
(Health Insurance Portability and Accountability Act)
Reporting on privacy at a service organization based on HIPAA regulatory requirements, in addition to reporting on controls at the service organization relevant to the privacy of the system based on the trust services criteria for privacy
Beyond testing the general privacy criteria, report provides further coverage based on HIPAA requirements, including third party review of a business’ compliance with the HIPAA 45 CFR 164.308-316 requirements
HITRUST Common Security Framework (CSF)
Reporting on security and privacy at a service organization based on a proprietary comprehensive, prescriptive, and certifiable framework, that can be used by all organizations that create, access, store or exchange sensitive and/or regulated data
Beyond testing the general privacy and security criteria, report provides further coverage based on HITRUST CSF requirements
CSA Security Trust & Assurance Registry (CSA-STAR)
Reporting on security at a service organization based on criteria established by the Cloud Security Alliance’s Cloud Control Matrix, in addition to reporting on controls at a service organization relevant to the security of a system based on the trust services criteria for security
CSA STAR Certification is an assurance framework, enabling cloud service providers to embed cloud-specific security controls
For cloud service providers, beyond testing the general security criteria, report provides further coverage based on CSA-STAR requirements
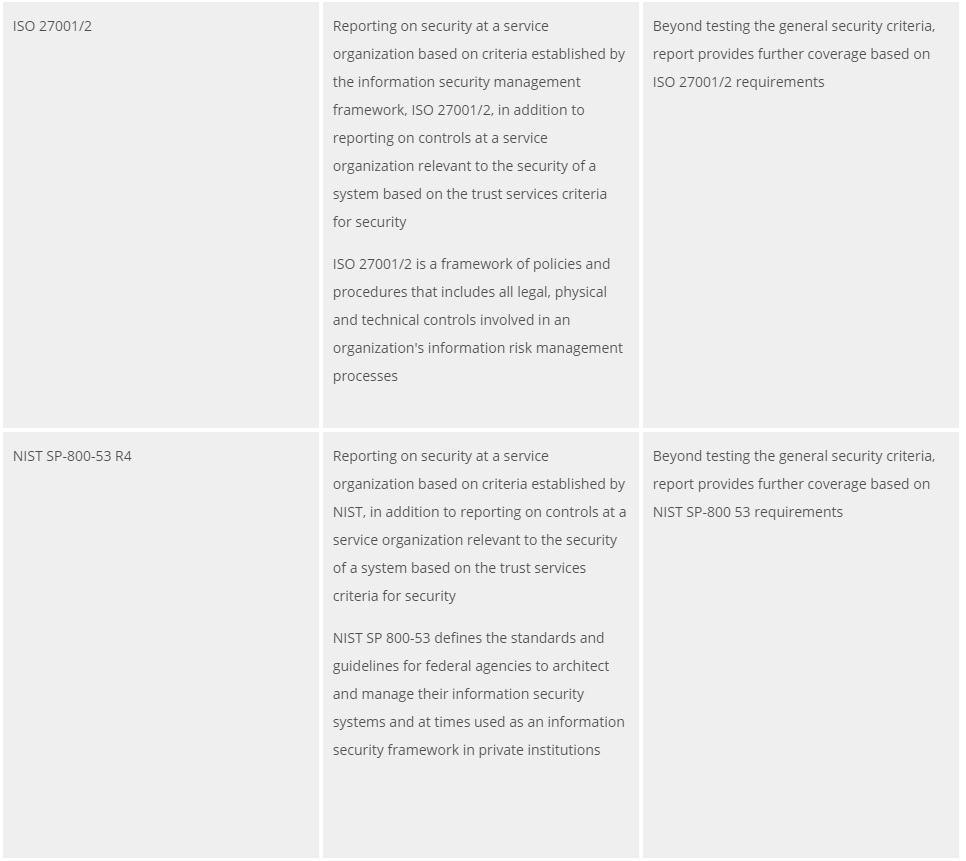
ISO 27001/2
Reporting on security at a service organization based on criteria established by the information security management framework, ISO 27001/2, in addition to reporting on controls at a service organization relevant to the security of a system based on the trust services criteria for security
ISO 27001/2 is a framework of policies and procedures that includes all legal, physical and technical controls involved in an organization's information risk management processes
Beyond testing the general security criteria, report provides further coverage based on ISO 27001/2 requirements
NIST SP-800-53 R4
Reporting on security at a service organization based on criteria established by NIST, in addition to reporting on controls at a service organization relevant to the security of a system based on the trust services criteria for security
NIST SP 800-53 defines the standards and guidelines for federal agencies to architect and manage their information security systems and at times used as an information security framework in private institutions
Beyond testing the general security criteria, report provides further coverage based on NIST SP-800 53 requirements
PCI DSS
Payment Card Industry – Data Security Standard
Reporting on security at a service organization based on criteria established by PCI standards, in addition to reporting on controls at a service organization relevant to the security of a system based on the trust services criteria for security
PCI DSS is an information security standard for organizations that handle branded credit cards from the major card schemes
For clients that process credit cards, beyond testing the general security controls, report provides further coverage based on PCI requirements
COSO
Committee of Sponsoring Organizations of the Treadway Commission
Reporting on security at a service organization based on criteria established by COSO, in addition to reporting on controls at a service organization relevant to the security of a system based on the trust services criteria for security
COSO board develops guidance documents that help organizations with risk assessment, internal controls and fraud prevention
Beyond testing the general controls, report provides further coverage based on COSO requirements
COBIT
Control Objectives for Information and Related Technologies
Reporting on security at a service organization based on criteria established by COBIT, in addition to reporting on controls at a service organization relevant to the security of a system based on the trust services criteria for security
COBIT is a framework created by ISACA for information technology (IT) management and IT governance that defines a set of generic processes for the management of IT, with each process defined together with process inputs and outputs, key process-activities, process objectives, performance measures and an elementary maturity model
Beyond testing IT general controls, report provides further coverage based on COBIT requirements
Additional Subject Matter items listed above have formal mappings in place with SOC 2 and are available from the American Institute of Certified Public Accountants.
Intelligence and Insights

Are You Prepared for an AI-Powered Cyber Attack?

AI Privacy Risks