A Comprehensive Guide to Penetration Testing – Types, Methods, Benefits and Best Practices
By Rey LeClerc Sveinsson, PhD
Table of Contents
- Different Types of Penetration Testing
- Why is Penetration Testing Important?
- What are the Benefits of Penetration Testing?
- What are the Steps in a Penetration Test?
- How Frequently Should Penetration Testing Occur?
- ERMProtect is Your Trusted Penetration Testing Company
Penetration testing, often referred to as pen testing or ethical hacking, stands as one of the most robust cybersecurity assessments available today, offering organizations a means to validate and mitigate their risks of a cyber-attack. In a penetration test, a qualified "ethical hacker" attempts to breach the cybersecurity defenses a company has established, uncovering vulnerabilities in the process.
This process is not just about finding weaknesses - it’s about understanding the potential impact of these vulnerabilities and prioritizing their remediation to protect the organization's assets. These tests are essential for an organization's security, underscored by their inclusion in numerous data regulations.
Not all penetration tests are alike. Not all penetration testing companies are alike. They can have different goals, target specific systems, deploy varying methodologies, and even test non-technical security components such as physical security or vulnerabilities caused by human error.
This guide explains the different types of penetration testing, their benefits, and their purpose.
What Are the Different Types of Penetration Testing?
Network Penetration Testing
Network penetration testing is a critical component of an organization's overall cybersecurity strategy, focused on evaluating the security and robustness of the network infrastructure. This type of testing involves a thorough examination of all components within the network, including firewalls, routers, switches, wireless access points, and other network devices that play a vital role in maintaining the flow of data and communications.
During a network penetration test, ethical hackers, also known as penetration testers, simulate real-world attacks to probe for vulnerabilities and weaknesses within the network. This process typically involves several stages:
- Reconnaissance and Information Gathering: The testers start by collecting information about the network, such as IP ranges, network topology, and the types of devices in use. This information is crucial for understanding how the network is structured and identifying potential entry points.
- Vulnerability Scanning: Using specialized tools, the testers scan the network for known vulnerabilities, such as outdated software, misconfigurations, or weak passwords. This step helps to pinpoint specific areas that may be susceptible to attack.
- Exploitation: Once vulnerabilities are identified, the testers attempt to exploit them to gain unauthorized access to the network. This could involve bypassing security controls, gaining access to sensitive data, or taking control of network devices. The goal is to determine how far an attacker could penetrate the network and what damage could be done.
- Privilege Escalation: After gaining initial access, the testers may try to escalate their privileges within the network. This involves exploiting more vulnerabilities to gain higher levels of access, such as administrative rights, which would allow them to control more critical systems and data.
- Lateral Movement: Testers also explore the potential for lateral movement within the network, which involves moving from one compromised device to others within the network. This helps to assess how easily an attacker could spread their reach across the network and access additional resources.
- Post-Exploitation and Reporting: After the testing phase, the findings are documented in a detailed report. This report not only outlines the vulnerabilities discovered but also provides actionable recommendations for remediation. The goal is to help the organization understand the risks and implement measures to strengthen their network defenses.
The primary aim of network penetration testing is to identify and address security gaps that could be exploited by malicious actors, whether they are external attackers or insider threats. By proactively uncovering these weaknesses, organizations can take the necessary steps to bolster their network security, protect sensitive information, and ensure the integrity and availability of their network resources.
Moreover, network penetration testing is not only about finding vulnerabilities; it also serves as a crucial tool for compliance with industry standards and regulations. Many regulatory frameworks, such as PCI DSS, HIPAA, and ISO/IEC 27001, require regular penetration testing as part of their security requirements. By conducting thorough network penetration tests, organizations can show their commitment to maintaining a secure environment, thereby reducing the risk of non-compliance and the associated penalties.
Network penetration testing is a proactive and essential practice for any organization seeking to protect its network infrastructure from potential threats. By identifying and addressing vulnerabilities before they can be exploited, organizations can maintain a strong security posture, safeguard their assets, and ensure the ongoing security of their network operations.
Application Penetration Testing
Application penetration testing is a specialized type of security assessment that focuses on identifying vulnerabilities within web and mobile applications. Given that applications often serve as the gateway to an organization's critical data and services, ensuring their security is paramount. Application penetration testing involves a comprehensive examination of the application's code, architecture, and deployment, with the goal of uncovering security flaws that could be exploited by attackers. Here’s a breakdown of the key aspects of application penetration testing:
- Code Review: One of the first steps in application penetration testing is a detailed review of the application's source code. This process helps identify insecure coding practices that might lead to vulnerabilities such as SQL injection, cross-site scripting (XSS), and buffer overflows. A thorough code review allows testers to understand how the application processes data, manages user input, and interacts with external systems, all of which are critical in identifying potential security weaknesses.
- Architecture Analysis: The architecture of the application is analyzed to assess how different components of the application interact with each other and with external systems. This includes evaluating the design of the application, its data flow, and how it handles authentication, authorization, and session management. Poorly designed architecture can introduce vulnerabilities such as insecure direct object references (IDOR), which can allow unauthorized access to data or functionality within the application.
- Deployment and Configuration Review: The environment in which the application is deployed is scrutinized to identify any misconfigurations or insecure settings. This can include issues such as improperly configured web servers, default credentials, or unpatched software components. A secure application can still be compromised if it is deployed in an insecure environment, making this aspect of testing critical.
- Testing for Common Vulnerabilities: Application penetration testers use a variety of techniques to identify and exploit common vulnerabilities, including:
- SQL Injection: This involves injecting malicious SQL queries into an application's input fields to manipulate the database, often allowing attackers to retrieve, change, or delete sensitive data.
- Cross-Site Scripting (XSS): Testers try to inject malicious scripts into web pages viewed by other users, potentially enabling the attacker to steal session cookies, redirect users to malicious sites, or perform actions on behalf of the user without their consent.
- Cross-Site Request Forgery (CSRF): This involves tricking a user into performing actions on a web application in which they are authenticated, potentially leading to unauthorized transactions or data modifications.
- Insecure Authentication and Session Management: Testers evaluate the effectiveness of the application's authentication mechanisms, looking for flaws such as weak password policies, lack of multi-factor authentication, or insecure session handling that could be exploited to gain unauthorized access.
- Business Logic Testing: In addition to testing for technical vulnerabilities, application penetration testers also examine the business logic of the application. This involves understanding how the application is intended to function and identifying ways in which an attacker could manipulate the application’s logic to achieve unintended outcomes, such as bypassing payment processes or altering user roles.
- Dynamic and Static Analysis: Application penetration testing often involves both dynamic (runtime) and static (code-based) analysis. Dynamic analysis is performed while the application is running, simulating real-world attacks and observing how the application responds. Static analysis, on the other hand, involves reviewing the source code or binary code of the application to identify vulnerabilities without executing the code.
- Reporting and Remediation Guidance: After completing the penetration test, the findings are compiled into a comprehensive report that details each identified vulnerability, its potential impact, and specific recommendations for remediation. This report serves as a roadmap for developers and security teams to address the identified issues and strengthen the security of the application.
Application penetration testing is essential for any organization that develops, deploys, or relies on web and mobile applications. As applications increasingly serve as the front line of digital interactions with customers, partners, and employees, the risks associated with application vulnerabilities have never been higher. By conducting regular and thorough application penetration tests, organizations can proactively identify and remediate vulnerabilities, protect sensitive data, and ensure that their applications are secure against the latest threats.
Application penetration testing is a critical process for safeguarding applications from a wide range of potential attacks. It offers invaluable insights into the security posture of an application, enabling organizations to address vulnerabilities before they can be exploited by malicious actors.
Social Engineering Penetration Testing
Social engineering penetration testing is a crucial aspect of an organization's overall security assessment that focuses on evaluating the human element of security. Unlike other forms of penetration testing that target technical vulnerabilities within systems or applications, social engineering tests assess the susceptibility of employees to manipulation and deception tactics that could be exploited by attackers to gain unauthorized access to sensitive information or systems.
Here’s a deeper look into what social engineering penetration testing entails:
- Phishing Attacks: One of the most common forms of social engineering is phishing. In a social engineering penetration test, ethical hackers may craft realistic phishing emails designed to trick employees into clicking on malicious links, downloading infected attachments, or providing sensitive information such as login credentials. These emails often appear to come from trusted sources, such as colleagues, vendors, or even executives within the organization, making them highly effective. The goal is to measure how many employees fall for the phishing attempt and identify the factors that contributed to their susceptibility.
- Spear Phishing: A more targeted version of phishing, spear phishing involves crafting highly personalized messages aimed at specific individuals or small groups within the organization. These messages might reference specific projects, roles, or responsibilities, making them more convincing and increasing the likelihood of success. Spear phishing tests are particularly useful for assessing the awareness and vigilance of high-profile targets, such as executives or key decision-makers, who may have access to critical systems or sensitive data.
- Pretexting: In pretexting scenarios, the ethical hacker creates a fabricated scenario or pretext to convince an employee to provide information or perform an action that compromises security. For example, the hacker might pose as an IT support person requesting login credentials to "fix" a problem, or as a vendor needing access to internal systems for a routine check. The success of pretexting relies on the attacker’s ability to establish trust and credibility with the target, and the test evaluates how employees verify the identities of individuals requesting sensitive actions or information.
- Baiting: Baiting involves tempting employees with a physical or digital "bait" designed to exploit their curiosity or greed. For instance, an ethical hacker might leave USB drives labeled as "confidential" or "salary information" in strategic locations, such as the company parking lot or break room. When an employee inserts the drive into their computer, it could execute malicious code or trackable software that simulates a security breach. The test measures how employees handle unexpected or suspicious items and whether they follow established security protocols.
- Tailgating: Also known as "piggybacking," tailgating is a physical social engineering tactic where an attacker gains unauthorized access to secure areas by following closely behind an authorized employee. During a social engineering penetration test, ethical hackers may try to tailgate employees into restricted areas, such as server rooms or executive offices, to see if employees challenge the intruder or follow proper procedures, like requiring badge scans or escorting visitors.
- Vishing (Voice Phishing): Vishing tests involve using phone calls to trick employees into revealing sensitive information or performing actions that compromise security. An ethical hacker might call an employee, pretending to be from the company’s IT department, and request password resets, access to systems, or other sensitive actions. The test evaluates how employees handle phone-based requests for sensitive information and whether they adhere to verification procedures.
- Impersonation: Impersonation tests involve ethical hackers posing as trusted individuals, such as maintenance workers, delivery personnel, or even senior executives, to gain access to secure areas or gather information. The test assesses whether employees adhere to security protocols, such as verifying identities and challenging unfamiliar faces, even when the person appears to have legitimate reasons for their actions.
- Post-Test Analysis and Training: After conducting social engineering tests, the findings are compiled into a detailed report that highlights the vulnerabilities in the human element of the organization’s security. The report includes data on the types of attacks that were successful, the reasons for success, and the potential impact of these breaches. Importantly, the report also provides actionable recommendations for strengthening the organization’s human defenses, such as implementing more training programs, refining security policies, and reinforcing the importance of security awareness.
Social engineering penetration testing serves as a powerful tool for identifying weaknesses in an organization’s human defenses, which are often the weakest link in security. Despite having robust technical controls in place, the human element can be easily exploited by attackers who use deception and manipulation tactics to bypass these controls.
By conducting regular social engineering tests, organizations can better understand their employees’ susceptibility to such attacks and take proactive measures to enhance security awareness, enforce security policies, and ultimately reduce the risk of successful social engineering attacks.
Social engineering penetration testing is essential for assessing and improving the resilience of an organization’s human element against manipulation and deception. It provides valuable insights into how employees respond to social engineering tactics and helps organizations develop more effective training and security protocols to protect against these increasingly sophisticated threats.
Wireless Penetration Testing
Wireless penetration testing is a specialized type of security assessment focused on evaluating the security and integrity of an organization’s wireless networks. Given the widespread use of wireless networks in modern businesses, ensuring their security is critical to protecting sensitive data and preventing unauthorized access.
Wireless networks, by their very nature, can extend beyond the physical boundaries of an organization, making them a prime target for attackers looking to exploit weaknesses in Wi-Fi configurations, encryption standards, and authentication protocols.
Here’s a closer look at what wireless penetration testing entails:
- Assessment of Wi-Fi Configurations: One of the first steps in wireless penetration testing is to evaluate the configuration of the organization's wireless networks to ensure they are protecting against vulnerabilities and security threats. This includes examining the settings for access points, routers, and other wireless devices to ensure they are properly configured. Misconfigured devices can create vulnerabilities that attackers can exploit to gain unauthorized access to the network. For example, using a vendor’s publicly known default settings and passwords might leave a network exposed. Similarly, improperly configured guest networks could provide a backdoor into the main corporate network.
- Evaluation of Encryption Standards: Encryption is a critical component of wireless network security, as it protects data transmitted over the network from being intercepted by unauthorized parties. During a wireless penetration test, the encryption standards in use - such as WPA2, WPA3, or older, less secure protocols like WEP - are thoroughly assessed. Ethical hackers try to break the encryption to see if they can decipher the data being transmitted. Weak or outdated encryption standards can allow attackers to eavesdrop on network traffic, capturing sensitive information such as passwords, financial data, or intellectual property.
- Authentication Protocol Testing: Authentication protocols determine how users and devices are granted access to the wireless network. In a wireless penetration test, the robustness of these protocols is assessed to ensure they effectively prevent unauthorized access. This involves evaluating the strength of password policies, the use of multi-factor authentication (MFA), and the implementation of enterprise-grade authentication methods like RADIUS (Remote Authentication Dial-In User Service). Weak authentication mechanisms can be exploited by attackers to gain entry to the network, either by guessing or stealing credentials or by using social engineering techniques.
- Rogue Access Point Detection: Attackers sometimes deploy rogue access points to trick users into connecting to a malicious network that appears legitimate. Once connected, the attacker can intercept communications or launch further attacks on connected devices. Wireless penetration testing involves scanning for unauthorized or rogue access points within the vicinity of the organization’s premises. Identifying and eliminating these rogue access points is crucial to maintaining the integrity of the wireless network.
- Man-in-the-Middle (MitM) Attack Simulations: Ethical hackers may attempt to perform Man-in-the-Middle (MitM) attacks during a wireless penetration test. In a MitM attack, the hacker intercepts and potentially alters the communication between two devices on the network. By simulating such attacks, the penetration test helps identify whether the network is vulnerable to eavesdropping, data interception, or session hijacking. The test also evaluates the network's ability to detect and respond to such attacks.
- Assessment of Wireless Client Security: The security of devices connecting to the wireless network - such as laptops, smartphones, and tablets - is also evaluated. This includes checking for vulnerabilities in the wireless adapters, drivers, and software configurations of these devices. If these are not secure, they can serve as an entry point for attackers to infiltrate the network. The test might involve attempting to exploit known vulnerabilities in wireless drivers or configurations to gain control of the device and, by extension, the network.
- Physical Security Considerations: Wireless penetration testing also considers the physical security of wireless network devices, such as access points and routers. If these devices are not physically secured, an attacker could gain direct access to them, either by resetting them to factory settings or by connecting directly to the device via Ethernet. Ensuring that these devices are properly secured and not easily accessible to unauthorized individuals is a key component of the test.
- Reporting and Recommendations: Upon completion of the wireless penetration test, the findings are documented in a comprehensive report. This report details the vulnerabilities discovered, the methods used to exploit them, and the potential risks to the organization. It also includes actionable recommendations for mitigating these risks, such as upgrading encryption protocols, enhancing authentication mechanisms, reconfiguring access points, and improving overall network monitoring.
Wireless penetration testing is essential for any organization that relies on wireless networks for daily operations. The security of these networks is paramount because they often carry sensitive information and provide access to critical resources. By identifying and addressing vulnerabilities in wireless configurations, encryption, and authentication protocols, organizations can significantly reduce the risk of unauthorized access, data breaches, and other cyber threats.
Wireless penetration testing provides a thorough evaluation of an organization's wireless network security, helping to identify and mitigate weaknesses that could be exploited by attackers. It ensures that wireless networks are configured securely, use strong encryption and authentication protocols, and are protected from both external and internal threats.
By regularly conducting wireless penetration tests, organizations can maintain the security of their wireless infrastructure and protect against the growing number of attacks targeting wireless networks.
Physical Penetration Testing
Physical penetration testing is a critical aspect of an organization's overall security strategy, focusing on evaluating the effectiveness of physical security controls that protect its facilities, data centers, and other secure areas. Unlike cyber penetration testing, which targets digital assets, physical penetration testing assesses the tangible measures in place to prevent unauthorized access to sensitive environments.
This type of testing is essential for ensuring that an organization’s physical defenses are robust enough to withstand attempts by attackers to gain unauthorized access.
Here’s an in-depth look at what physical penetration testing entails:
- Assessment of Physical Barriers: One of the primary focuses of physical penetration testing is evaluating the effectiveness of physical barriers such as fences, gates, walls, and doors. Ethical hackers may try to breach these barriers using a variety of methods, such as climbing fences, bypassing locked doors, or finding and exploiting weak points in the physical structure. This testing helps figure out whether these barriers are sufficient to prevent unauthorized entry or if they need to be reinforced.
- Testing Access Control Systems: Access control systems, including keycard readers, biometric scanners, and security codes, are critical components of physical security. During a physical penetration test, ethical hackers will try to bypass these systems using various techniques. This could involve techniques such as tailgating (following an authorized person into a secure area without being noticed), using stolen or cloned access cards, or even exploiting vulnerabilities in biometric systems. The goal is to find whether the access control mechanisms effectively prevent unauthorized individuals from gaining entry to restricted areas.
- Evaluation of Surveillance Systems: Surveillance systems, including CCTV cameras and motion detectors, play a vital role in monitoring and securing facilities. Physical penetration testing involves assessing the coverage, placement, and effectiveness of these surveillance systems. Ethical hackers may try to evade detection by finding blind spots in camera coverage, disabling cameras, or exploiting weaknesses in the surveillance infrastructure. This testing helps organizations figure out whether their surveillance systems can detect and record unauthorized activities in real-time.
- Security Personnel Response Testing: Security personnel are often the first line of defense against physical intrusions. During a physical penetration test, ethical hackers might try to engage or bypass security personnel to evaluate their response to suspicious behavior. This could involve simulating social engineering tactics, such as impersonating an employee or vendor, to test whether security staff follow proper verification procedures. The test assesses the alertness, training, and procedures of security personnel, ensuring they are prepared to manage real-world threats.
- Tailgating and Piggybacking Scenarios: Tailgating, also known as piggybacking, is a common method used by attackers to gain unauthorized access to secure areas by closely following an authorized individual. Physical penetration testers will simulate these scenarios to see if employees challenge or report such behavior. This testing highlights whether staff are aware of and adhere to security protocols designed to prevent unauthorized access via tailgating.
- Inspection of Locking Mechanisms: The locking mechanisms used on doors, cabinets, and safes are critical to protecting sensitive areas and assets. Physical penetration testing includes evaluating the strength and effectiveness of these locks. Ethical hackers might use lock-picking techniques, bypass tools, or brute force methods to try to gain access. This testing helps show whether the locks in place are adequate or if they need to be upgraded to more secure options.
- Environmental Controls and Safety Measures: In addition to testing security controls, physical penetration testing also assesses the safety and environmental controls in place, such as fire alarms, sprinkler systems, and emergency exits. The test ensures that these systems are not only functional but also secure from tampering or accidental activation by unauthorized individuals. This aspect of testing is crucial for ensuring the overall safety and security of the facility.
- Social Engineering Tactics: Physical penetration testing often incorporates social engineering techniques to assess the human element of physical security. For example, ethical hackers might pose as delivery personnel, maintenance workers, or even employees to gain access to secure areas. These scenarios evaluate whether staff are vigilant and follow security protocols, such as verifying the identity of visitors or contractors and barring unknown individuals from restricted areas without proper authorization.
- Assessment of Secure Areas and Data Centers: Secure areas such as server rooms, data centers, and executive offices are often the most critical parts of an organization to protect. Physical penetration testing focuses heavily on these areas, as they typically have the most sensitive and valuable assets. The test involves trying to breach these areas through physical means, social engineering, or a combination of both. The goal is to assess whether the security measures in place, such as reinforced doors, access controls, and surveillance systems, are adequate to protect these high-value targets.
- Reporting and Remediation: After conducting the physical penetration test, a detailed report is provided that outlines the methods used, vulnerabilities discovered, and potential risks to the organization. The report also includes recommendations for improving physical security measures, such as enhancing access control systems, increasing surveillance coverage, improving the training and protocols for security personnel, and reinforcing physical barriers. This actionable guidance helps organizations strengthen their physical security posture and reduce the risk of unauthorized access.
Physical penetration testing is essential for any organization that needs to protect sensitive areas, assets, and personnel from unauthorized access or physical threats. By identifying weaknesses in physical security controls, organizations can take proactive steps to fortify their defenses, ensuring that their facilities are secure against potential intrusions or attacks.
Physical penetration testing provides a comprehensive evaluation of an organization’s physical security measures. It tests the effectiveness of physical barriers, access control systems, surveillance systems, and the human element, ensuring that all aspects of physical security are robust and capable of defending against real-world threats. Regular physical penetration testing is crucial for maintaining a strong security posture and safeguarding an organization's critical assets and infrastructure.
Why is Penetration Testing Important?
The importance of penetration testing cannot be overstated. It is a vital part of a comprehensive cybersecurity strategy, helping organizations secure mission-critical assets, prevent financial losses, maintain regulatory compliance, and enhance their overall cybersecurity posture.
More importantly, it enhances overall cybersecurity posture, protecting both enterprises and their customers from cyber threats. By proactively identifying and addressing vulnerabilities, penetration testing protects enterprises and their customers from the ever-evolving landscape of cyber threats, ensuring the security and integrity of valuable data and systems.
What Are the Benefits of Penetration Testing?
- Enhanced Security Posture: By identifying and addressing vulnerabilities, organizations can significantly improve their overall security posture. Penetration testing helps in patching weaknesses before they can be exploited by malicious actors.
- Regulatory Compliance: Many regulations and standards, such as PCI DSS, HIPAA, and GDPR, require regular penetration testing. Compliance with these regulations helps organizations avoid legal penalties and maintain customer trust.
- Risk Management: Penetration testing provides a realistic assessment of the organization's security risks. It helps in prioritizing security investments based on the criticality of vulnerabilities and the potential impact of their exploitation.
- Protection of Sensitive Data: By identifying vulnerabilities that could lead to data breaches, penetration testing helps in protecting sensitive information such as personal data, financial information, and intellectual property.
- Business Continuity: Identifying and mitigating security risks ensures the continuous operation of business processes. Penetration testing helps in preventing disruptions caused by cyberattacks, safeguarding the organization's reputation and financial stability.
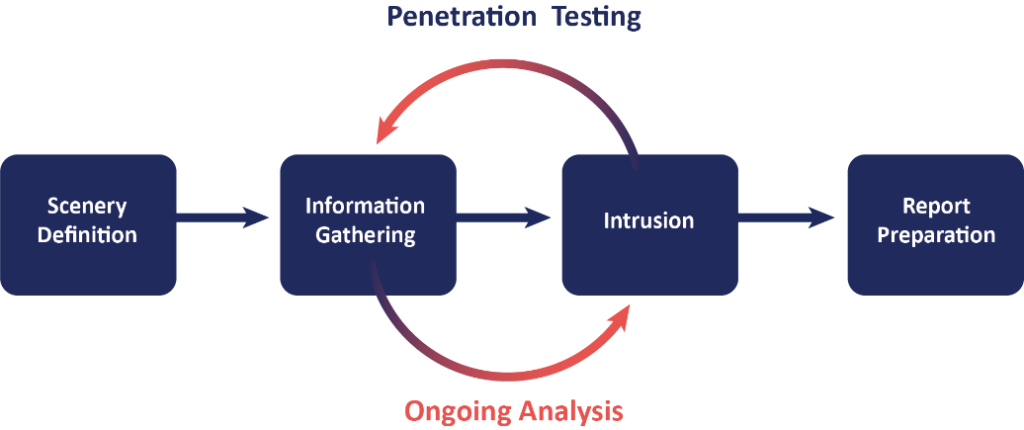
What Are the Steps in a Penetration Test?
- Planning and Preparation: This first phase involves defining the scope and objectives of the test. It includes understanding the systems and networks to be tested, identifying potential risks, and establishing the rules of engagement.
- Reconnaissance: Also known as information gathering, this phase involves collecting as much information as possible about the target. This can include network ranges, IP addresses, domain names, and organizational structure. Techniques such as social engineering, dumpster diving, and open-source intelligence (OSINT) are often employed.
- Scanning: This phase involves using automated tools and manual techniques to identify open ports, services, and potential vulnerabilities. Common tools include Nmap for network scanning and Nessus for vulnerability scanning.
- Exploitation: In this phase, ethical hackers try to exploit the identified vulnerabilities. The goal is to gain access to systems and data, showing the potential impact of the vulnerabilities. This could involve techniques such as SQL injection, buffer overflows, or exploiting weak passwords.
- Post-Exploitation: After gaining access, ethical hackers will assess the extent of the breach, maintain access, and gather as much data as possible. This phase helps to understand the potential damage a real attacker could cause.
- Reporting: The final phase involves documenting the findings of the penetration test. The report should detail the vulnerabilities discovered, the methods used to exploit them, the potential impact, and recommendations for remediation. It should be clear, concise, and actionable, aimed at both technical and non-technical stakeholders.
How Frequently Should Penetration Testing Occur?
- Annual Testing: At a minimum, organizations should conduct penetration tests annually to ensure their defenses are up to date with current threat vectors.
- After Major Changes: Any significant changes to the IT infrastructure, such as new system deployments, updates to existing systems, or changes in network architecture, should prompt immediate penetration testing.
- Regular Reviews: Periodic reviews, such as quarterly or bi-annual assessments, can help identify vulnerabilities that may arise between annual tests. These reviews can include fewer comprehensive scans and tests compared to full-scale penetration tests.
- Incident Response: Following any security incident or breach, immediate penetration testing is essential to understand the extent of the compromise and to prevent future occurrences.
For further reading on the importance and methodologies of penetration testing, you can refer to resources such as the OWASP Testing Guides and the NIST Penetration Testing Guidance.
ERMProtect is Your Trusted Penetration Testing Company
ERMProtect is a trusted leader in the cybersecurity industry, offering extensive expertise in penetration testing to help organizations safeguard their digital assets. With a deep understanding of the ever-evolving threat landscape, our team of certified security professionals conducts thorough penetration tests designed to identify vulnerabilities before malicious actors can exploit them. By simulating real-world attacks, we provide organizations with a clear view of their security posture and actionable insights to strengthen defenses.
Our penetration testing services are tailored to meet the unique needs of each client, whether you're a small business or a large enterprise. We assess your systems, networks, and applications to uncover weaknesses that could lead to data breaches, financial loss, or reputational damage. Our approach is not just about finding vulnerabilities; it's about helping you understand the risks and guiding you on how to remediate them effectively.
In addition to threat mitigation, ERMProtect’s penetration testing services play a crucial role in helping organizations achieve and maintain compliance with industry standards and regulations, such as PCI DSS, HIPAA, and GDPR. Our comprehensive reports are designed to meet the stringent requirements of auditors and regulators, giving you confidence that your organization is compliant and secure.
If you’re ready to take the next step in protecting your organization, contact [email protected] or call 305-447-6750 today for a free consultation. Our experts are here to help you navigate the complexities of cybersecurity and ensure your systems are resilient against the latest threats.
About the Author
Dr. Rey Leclerc Sveinsson is an expert in Privacy and Data Protection, Information Security, and Technology Governance, Risk & Compliance (IT GRC). He has developed information assurance programs for major organizations globally during his career as well as serving as a Consultant for ERMProtect. He has a PhD in Information Systems and multiple master’s degrees in the areas of privacy, information technology, and cybersecurity laws.
Intelligence and Insights

Aligning Your Incident Response Plan with NIST SP 800-61 Rev. 3

CEO Checklist: How To Know If Your Organization Is Cyber Secure