Cybersecurity – What’s with the Attitude?
In 2014, we saw the Heartbleed vulnerability arrive on the Cybersecurity scene. ERMProtect had written about Heartbleed a couple of weeks after it was identified and talked about the simplicity with which it can be exploited to render the world’s most favorite Cybersecurity jargon – encryption – completely useless. So it wouldn’t matter if you did your bank transactions on a million bits of encryption, it could still be easily compromised thanks to Heartbleed. So you’d expect the reaction, the world over, to be shellshock (which, ironically, is the name of another equally dangerous vulnerability that soon followed Heartbleed) and one of swift and decisive action to fix the vulnerability and see the back of it.
Well…Surprise!
Shodan – which is like your Google for Internet-connected devices – recently said that a search it performed on January 22 this year identified close to 200,000 Internet-connected devices that are still vulnerable to the three-year old Heartbleed vulnerability. And let’s look at the top 10 countries where these servers are located:
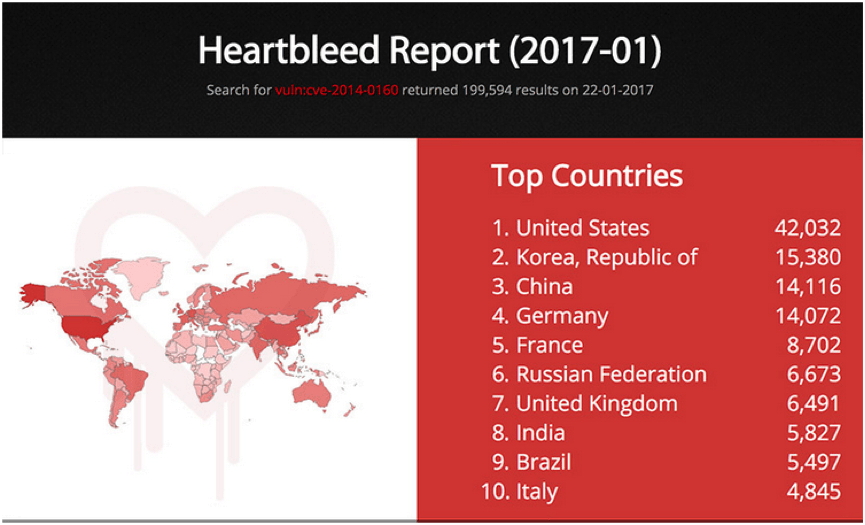
Image Source: Shodan
A count of these top 10 alone gives a staggering 123,635 servers still vulnerable to Heartbleed. And these are all countries that are on the frontlines of world economic discussions. Many of these are developed nations and heading the list by a truly dominating margin is, unbelievably, the United States! Whoever said Americans don’t get irony is dead wrong. Not only do Americans get irony…we practice it!
And here’s the worst part – this situation has no excuse! There are literally hundreds of free tools and websites available online to identify if your server is vulnerable to Heartbleed. And these are the simple point-click-and-fire kind of tools. So folks, this really is an attitude problem! Imagine that – one of the world’s most sinister, easy-to-exploit, and not-so-difficult-to-fix vulnerabilities and our response to it is an invigorating – “yeah, we’ll get to that…soon”.
Cat And Mouse
Cybersecurity has always been a cat and mouse game. Organizations obviously being the mice that are always trying to protect themselves. But the cats in this case have become better – lean-mean-mouse-catching-machine kind of better. Meanwhile, the mice still don’t want to fix something as simple as Heartbleed. Given this scenario, hackers today aren’t even giving it their best shot and still landing a significant amount of prey. It’s no surprise then that hacker attacks are on the rise and we’re drunk to our eyeballs with media stories on hackers looting and pillaging organizations the world over like modern-day pirates without the “Arrr”.
So what do organizations need to do to turn around this “attitude problem”? Let’s take a look –
- Cybersecurity Awareness Training
Ineffective security awareness training or the complete lack of it is one of the root causes for a poor Cybersecurity attitude. And the problem is the kind of training that’s available. We’ve long emphasized that the way our world goes about security awareness training today is dead. A bored employee doesn’t learn. An unengaged employee doesn’t care. You need to be innovative and creative to come up with security awareness training that educates, engages, and enthuses. Videos that are out of this world, fresh, and interesting that will draw them towards getting trained; tips and tricks that speak to them in their language and have no hidden corporate agenda except highlighting to them – what’s in it for them in security awareness; and fun face-to-face training sessions that leave them wanting more. The age of “enforcing” and “policing” is gone. If you want to succeed in security awareness training, try to “sell” your employees the concept. A convinced employee will be a human firewall; a compliant employee will get you exactly that – compliance.
- Cybersecurity Awareness Training…
…for the Board of Directors! That’s right! The biggest reason for poor Cybersecurity attitudes at the bottom is the missing “tone at the top”. While many regulators today are pinning more accountability on top management, why wait for regulators to hiss at you with their menacing fangs showing to make the change? The way hackers have advanced today, it’s no longer going to be enough for top management to say – “Yeah, I’ll just call my CISO in and he can answer that cyber-voodoo question”. It’s critical for top management to improve awareness levels and knowledge about Cybersecurity, the threats their organization faces due to that, and how the organization intends to deal with that. No, we’re not asking the CEO or Board Member to know the make and model of the latest and best security software or equipment, but we are asking them to know about the measures that their organization is putting into place to combat the latest and greatest Cybersecurity threats. Example – let’s go back to the Heartbleed or Shellshock vulnerabilities that exposed organizations worldwide to serious data breach risks. A CEO or a Board Member should at least make the effort to know, high-level, what the vulnerability was, how it could impact her/his organization, and what steps her/his CISO is taking to mitigate the risks that the organization faces. So CEOs and Board Members, security awareness training is no longer just for employees; you need to think about innovative and creative methods to get yourself interested in Cybersecurity. Take a look at this unique and innovative security awareness video specifically made for CEOs, Board Members, and top management.
- The Vending Machine With An Attitude
Many times it’s not even your own employees with the attitude problem. Third-party vendors are increasingly becoming entry routes for hackers and are the seeds of several recent data breaches. SSAE 16 assessments (SOC1 and SOC2) of vendors will go a long way in giving you (and even regulators, by the way) confidence in your third-party security risk containment efforts. At a minimum, have your third-party vendors undergo an assessment by a security assessment firm of your choice. Why? If you were buying a used car, would you trust your mechanic’s advice or the advice of the car dealer’s mechanic who can’t stop smiling ingenuously at you? Yeah…that’s why.

Turn your employees into a human firewall with our innovative Security Awareness Training.
Our e-learning modules take the boring out of security training.

Get a curated briefing of the week's biggest cyber news every Friday.
Intelligence and Insights

Aligning Your Incident Response Plan with NIST SP 800-61 Rev. 3

CEO Checklist: How To Know If Your Organization Is Cyber Secure

