Spot the Phishing Attempt - Cybersecurity Awareness
The images displayed below are a combination of phishing emails and real email messages. Spot the phish! Click on the images to zoom in.
Spoiler Alert: Answers are below.
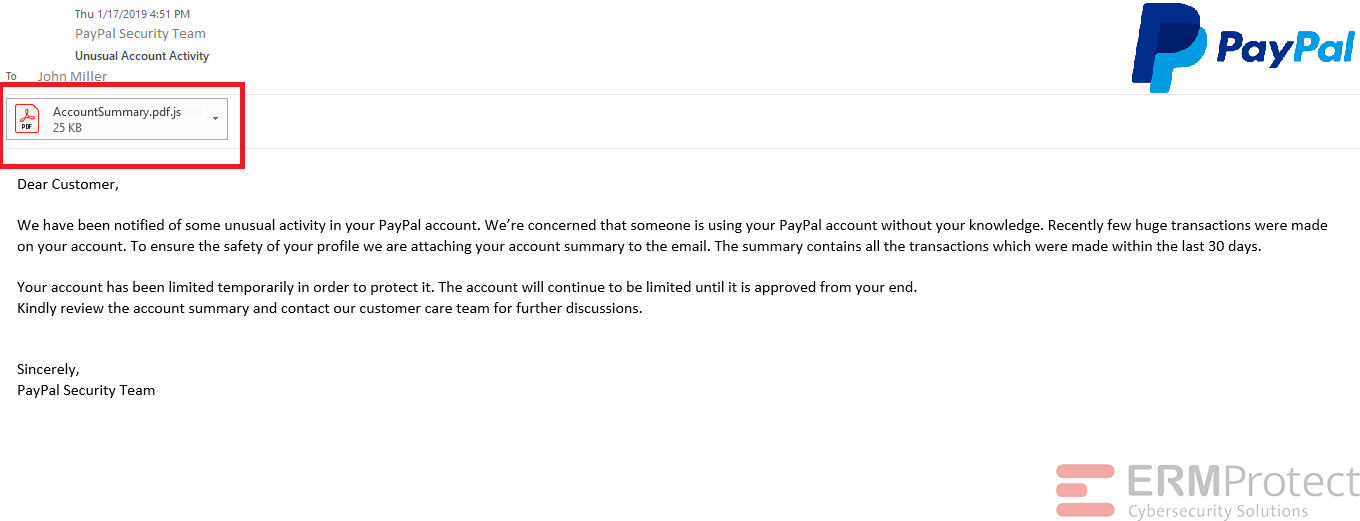
Image 1 details: The email contains a malicious attachment with .js extension. Note that the attachment tries to show it’s a PDF file (look at the icon of the file). But the extension ends with a “.js.” This is a malicious attachment typical of a phishing email.
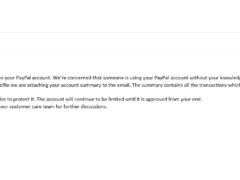
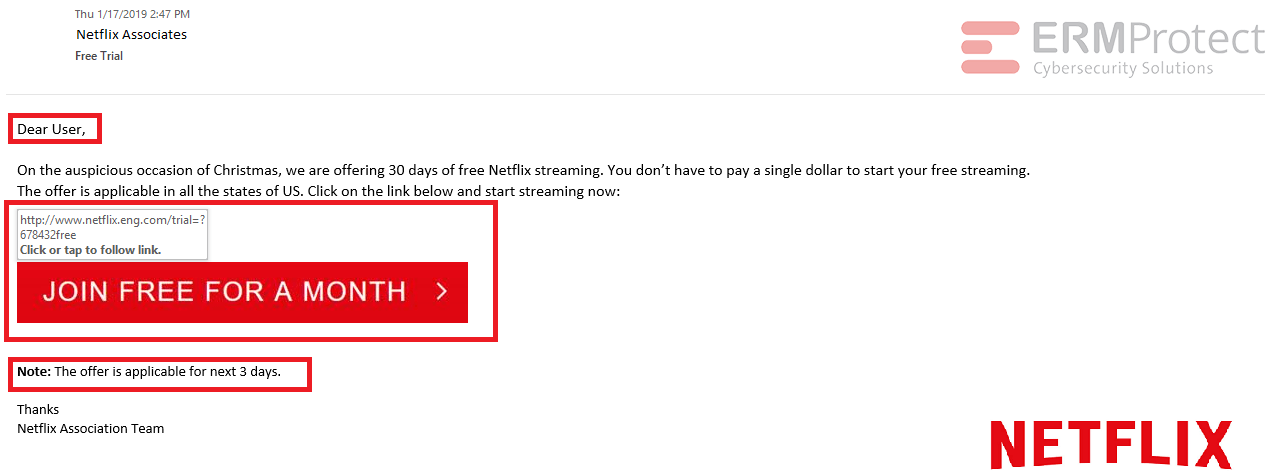
Image 2 details: When you mouse-over the hyperlink, you can see that it is phishy. Also, there is a sense of urgency in the language. The email salutation is generic as well. This raises cybersecurity alarm bells.
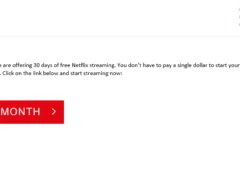
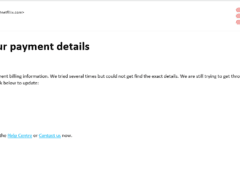
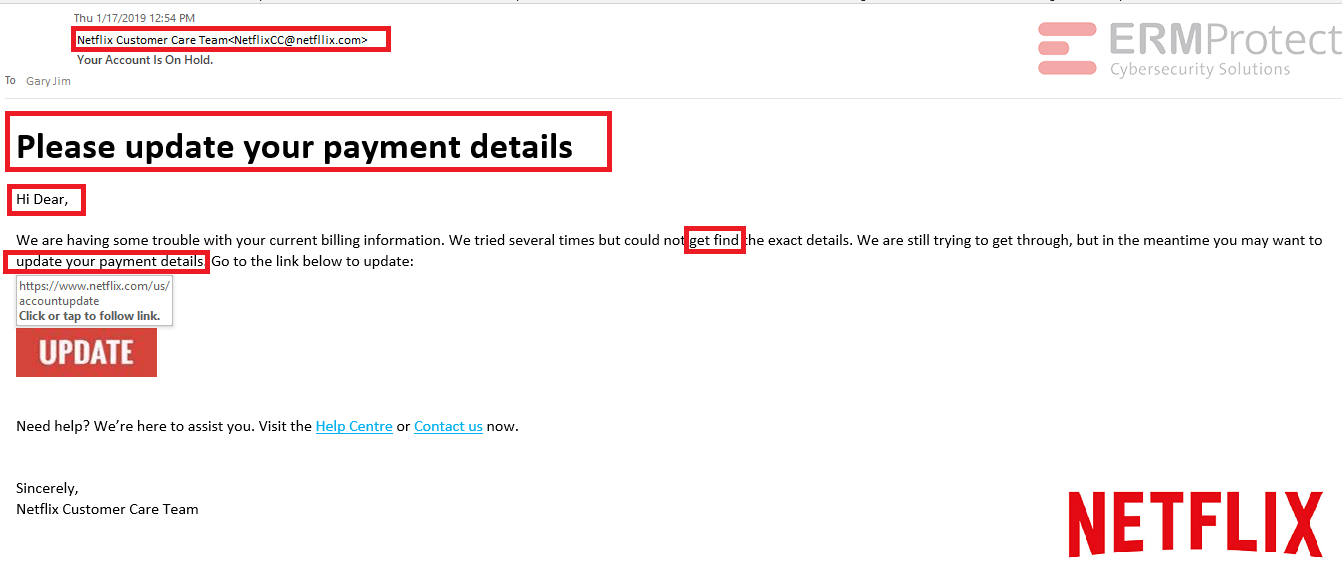
Image 3 details: The sender email ID is phishy. The salutation is completely out of line and there are grammatical mistakes. Phishing email.
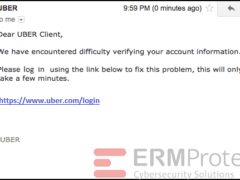
Image 4 details: The hyperlink is a legitimate uber website link. Although you should always have high cybersecurity awareness, there aren’t any typical red flags in the email.

Get a curated briefing of the week's biggest cyber news every Friday.

Turn your employees into a human firewall with our innovative Security Awareness Training.
Our e-learning modules take the boring out of security training.
Intelligence and Insights

Aligning Your Incident Response Plan with NIST SP 800-61 Rev. 3

CEO Checklist: How To Know If Your Organization Is Cyber Secure