New Payment Card Standard Will Tighten Security Rules to Protect Data
By Ama Boateng, ERMProtect, IT Security Consultant
Some clients are already asking what to expect when the next version of the Payment Card Industry Data Security Standards is released next year. That’s no surprise since decisions that are being made now about IT infrastructure and policy could be affected by any changes. As such, having a knowledgeable PCI compliance company to rely on is paramount.
It’s too early to know definitively what will change when Version 4.0 of the PCI DSS is released, but there are evident trends to share. While not cast in concrete, these trends are foreshadowed in the PCI Council’s blogs and feedback reports from industry sources who have reviewed early drafts.
Bottom line: The 12 core PCI DSS requirements are not expected to fundamentally change with PCI DSS v4.0, as these are still critical components of securing credit card data, according to a recent PCI blog.
But changes are afoot that would account for advancements in security technology, risk mitigation techniques, and evolving threats. The changes would also strengthen security control requirements while at the same time adding flexibility to achieve compliance.
Based on the current timetable, v.4.0 won’t be released until mid- to late 2021. A lot could happen between then and now, but based on early drafts, the following areas may be subject to change:
-
- Access Management - The new version of the PCI DSS may contain revisions to the authentication requirements to reflect the latest industry best practices for password and multi-factor authentication. The authentication requirements may include the following:
-
- Multifactor authentication usage for all accounts that have access to the cardholder data, not just administrators accessing the cardholder data environment
-
- Passwords/passphrases for accounts used by applications and systems are changed at least every 12 months and upon suspicion of compromise.
-
- Password/passphrases for accounts used by applications and systems meet the following minimum level of complexity: A minimum of at least 15 characters, contain both numeric and alphabetic characters and prospective passwords/passphrases are compared against the list of known bad passwords as PCI DSS requires.
-
- Access privileges have to be reviewed at least once every six months.
-
- Vendor or third-party accounts may be enabled only as needed and monitored when in use.
-
- Risk Assessment - The risk assessment requirement may be modified to ensure that the risk assessment is not being treated as a “checkbox exercise” by organizations. The risk assessment requirement may be updated to provide greater clarity and guidance for organizations on the risk management process.
- Access Management - The new version of the PCI DSS may contain revisions to the authentication requirements to reflect the latest industry best practices for password and multi-factor authentication. The authentication requirements may include the following:
-
- Evolving technology – A major change in v4.0 may be the customized approach that would allow organizations to design their own controls and implement them based on the intent of the requirements. This would allow companies more flexibility to adopt new technologies or security solutions and not have to wait for the standard to catch up. The draft of PCI DSS v4.0 supports the use of different technologies, such as cloud hosting services, by introducing more flexibility to the wording of requirements and adding intent statements. The updated version addresses the evolving threats to the payment ecosystem and how the security methods and technologies that have been developed to address these threats have evolved.
-
- Testing – The testing documents provide better explanations for sampling, and scoping. Additional direction for assessors on sampling guidance will be included to verify that controls are in place consistently across the entire population.
-
- Scoping - The accuracy of PCI DSS scope is documented and confirmed at least once every 12 months and upon significant changes to the in-scope environment. For service providers, the scope must be reviewed every 3 months and upon significant changes to the in-scope environment.
-
- Security Awareness Training – The requirements for training of end-users may be enhanced to include more information regarding current threats and vulnerabilities that could impact the security of the cardholder data environment, including Phishing and Social Engineering.
-
- Monitoring - The requirement to monitor the cardholder data environment may be updated to reflect advancements in technology, such as the availability of next-gen network and endpoint detection tools. Merchants and service providers may be required to have processes and mechanisms to detect phishing attempts.
- Encryption - Card encryption requirements may be expanded to include all transmissions of cardholder data. A data-discovery methodology may be implemented to locate all sources and locations of cleartext PAN (primary account numbers) at least once every 12 months and upon significant changes to the cardholder data environment or processes. For service providers, every 3 months.
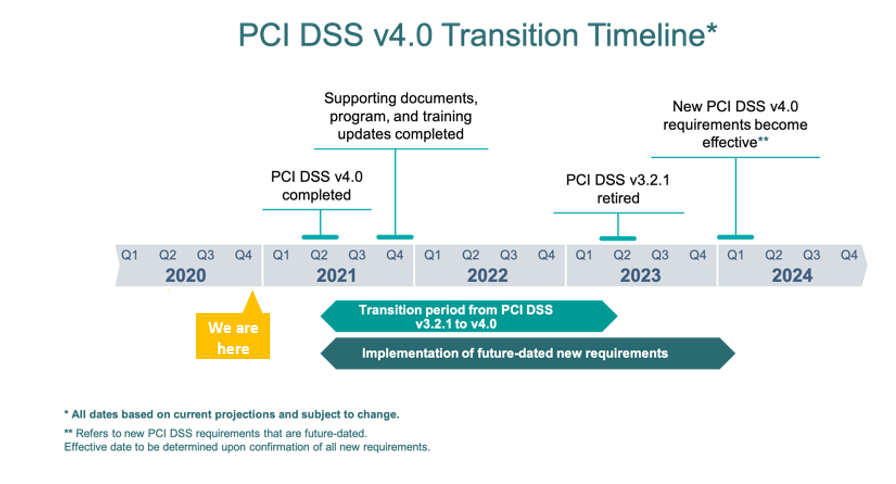
Release Timeline
According to the PCI council, version 4.0 of the PCI DSS is expected to be released in mid-2021. Once the standard, supporting documents (including SAQs, ROCs, and AOCs), training, and program updates are released, organizations will have an extended transition period of 18 months to update from PCI DSS v3.2.1 to PCI DSS v4.0. This extended period will allow organizations time to become familiar with the changes in v4.0, update their reporting templates and forms, and plan for and implement changes to meet updated requirements.
Below is an overview of the planned transition timeline and potential timing for future-dated requirements.
The Council strongly urges organizations with access to early drafts of PCI DSS v4.0 to wait until the final version is released before trying to implement any new or updated requirements.
PCI DSS Compliance with ERMProtect's PCI Compliance Services
We recommend that you bring in professional help to prepare your organization to comply with regulatory changes that v4.0 may require. ERMProtect offers effective and robust PCI DSS v4.0 preparation services, including but not limited to:
- Security assessments
- Employee education and security awareness training
- Vulnerability scanning and penetration testing
Our wide range of PCI compliance services will not only help you get ready for compliance, but improve the overall security posture of your organization.
For More Information:
- https://www.pcisecuritystandards.org/pci_security/maintaining_payment_security
- https://blog.pcisecuritystandards.org/topic/pci-dss-v4-0
- https://blog.pcisecuritystandards.org/pci-dss-looking-ahead-to-version-4.0
- https://blog.pcisecuritystandards.org/pci-dss-v4-0-anticipated-timelines-and-latest-updates
- https://www.pcisecuritystandards.org/get_involved/request_for_comments
To speak with an expert on our Cybersecurity team please call (800) 259-9660.

Get a curated briefing of the week's biggest cyber news every Friday.
Intelligence and Insights

Aligning Your Incident Response Plan with NIST SP 800-61 Rev. 3

CEO Checklist: How To Know If Your Organization Is Cyber Secure