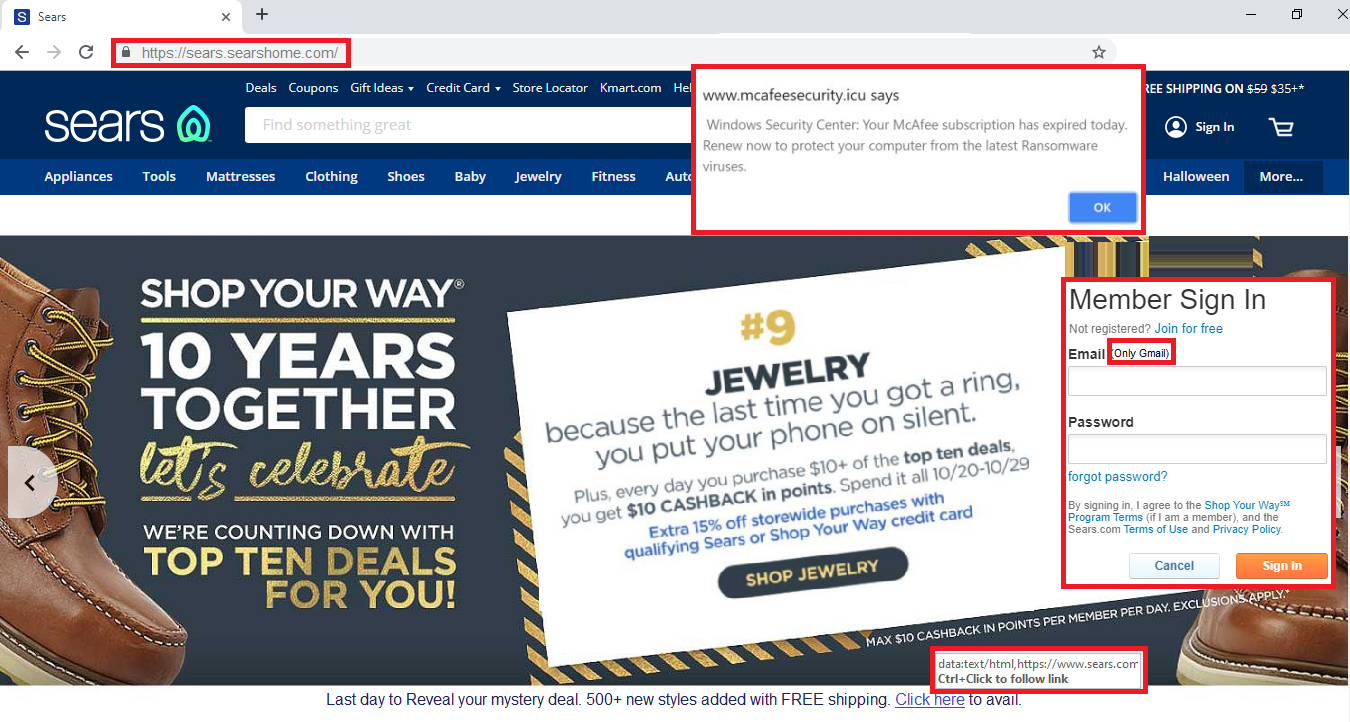
Count the Phish: Sears Webpage
This webpage contains one or more red flags that makes it a phishing site. How many can you find in this phishing example? Click to enlarge.
Answer: There are 5 red flags in total. Let’s take a look.
- Examine the page URL. Here, the attacker has used what’s known as a ‘subdomain attack.’ The domain “searshome.com” is clearly not the real web domain of Sears. Attackers often try to take advantage of the fact that a lot of people wouldn’t be able to tell the difference between a domain and a subdomain.
- The second and most obvious red flag is the “mcafeesecurity.icu” pop-up. It clearly looks phishy and has no place on a reputable website like Sears.
- The attacker has inserted a fake login form directly onto the main homepage to steal your credentials.
- The other strange thing about the login form is that it says “Email (Gmail Only).” That is clearly phishy! Why would a company like Sears do something like that?!
- This last red flag is a bit tricky. If you notice the “Click here” hyperlink, it contains the actual sears.com link to lure you into thinking the link is trustworthy. But if were to click that link, the actual URL would go far past the end of the address bar and contain a malicious script that would execute once you click. The tipoff is the "data:text/html" text at the start of the URL. If you see something like that, avoid the URL completely, as this is a common phishing trick.
Click to enlarge.

Get a curated briefing of the week's biggest cyber news every Friday.

Turn your employees into a human firewall with our innovative Security Awareness Training.
Our e-learning modules take the boring out of security training.
Intelligence and Insights

Aligning Your Incident Response Plan with NIST SP 800-61 Rev. 3
This article offers key updates in the latest NIST guidance, why they’re significant, and what practical steps you can take to update your organization’s incident response plan …

CEO Checklist: How To Know If Your Organization Is Cyber Secure
This CEO Checklist is a starting point for executive oversight – to spot gaps, test what your team is telling you, & prioritize where to invest attention/budget …

Guide to Penetration Testing and Advanced Techniques in Penetration Testing Services
Penetration testing is the interactive nature of the control evaluation. Unlike static assessments, penetration testing services involve dynamic interaction with the system …