Spot the Phish: Black Friday Scams
The images displayed below are a combination of images which are phishing attacks and real images. Spot which ones are real and which ones are phony:
Spoiler Alert: Answers are below.
Answer: Image 2 and 4 are phishes. Let’s see how:
Image 1 details: The email offer has no obvious red flags or signs of a cyber attack, although you should be sure to mouse-over the URL to be sure it shows the company’s legitimate email address, not a phishy one. This one is genuine.
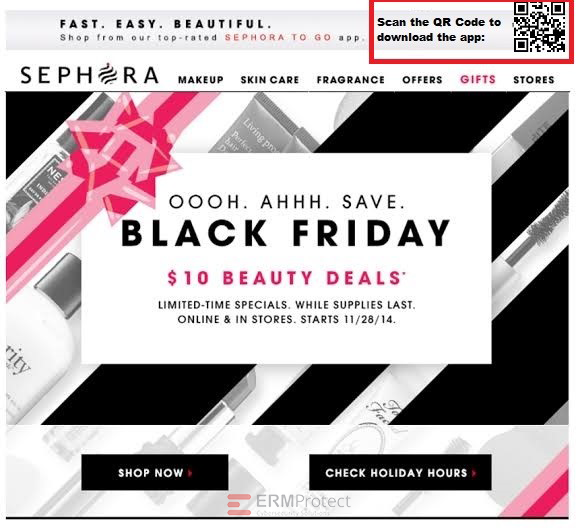
Image 2 details: This is a Black Friday “Deal Reveal” email. It passes almost all of our typical checks – the hyperlinks, the logo, the grammar, and the overall look-and-feel seem okay. But take a look at that QR code on the top-right corner. You’ll realize it’s a fake when you try to check out. Once you come across even one red flag that indicates a phishing attack, that’s enough for you to stop and discard this one completely. It’s a phish!
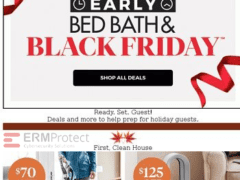
Image 3 details: This looks like an early Black Friday sale notification. No real, visible red flags here. Always keep your guard up, regardless. This one looks genuine.
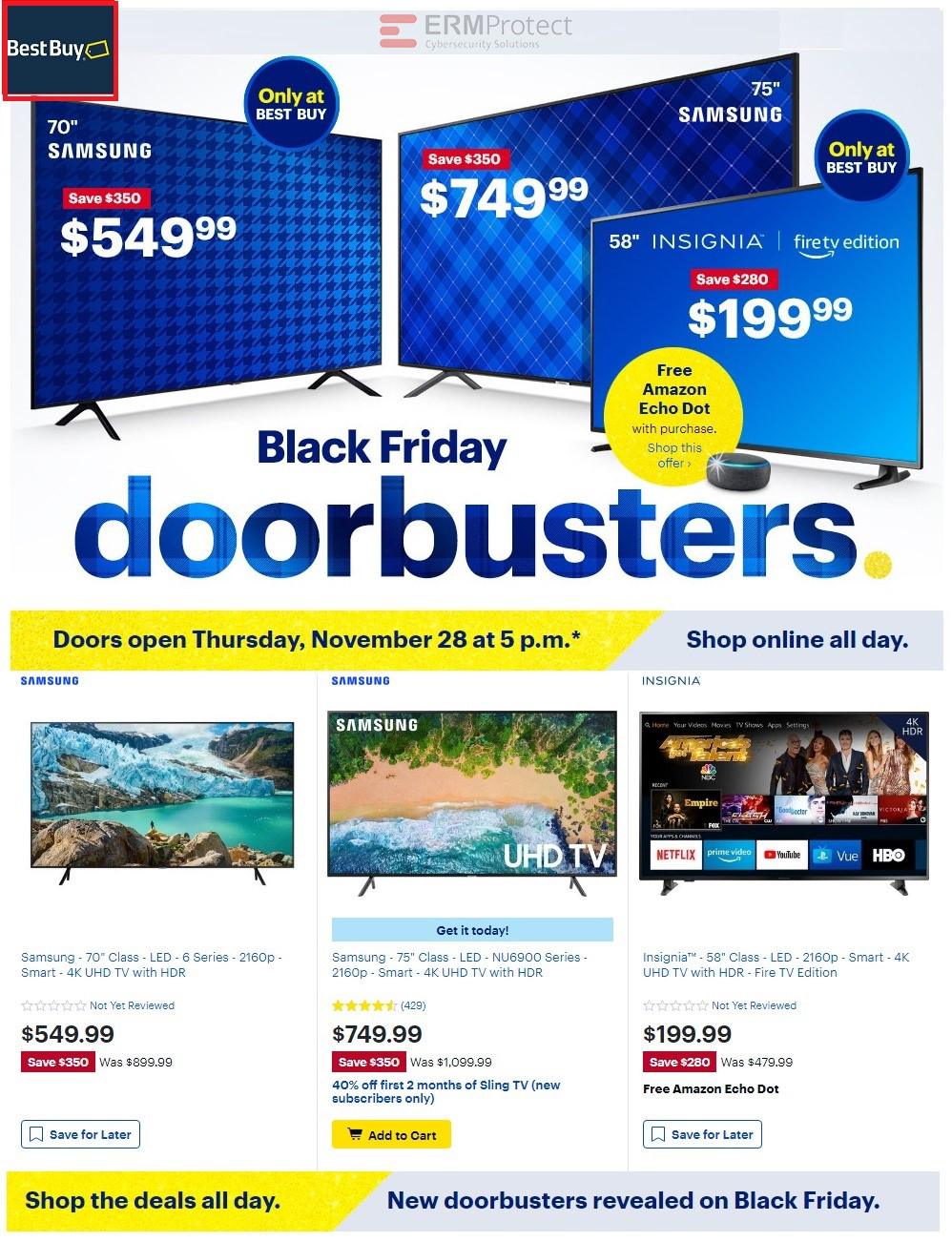
Image 4 details: This one is tricky! Almost everything looks in order. The only red flag here is the really outdated logo … and that’s easy to miss! Many times, hackers will try to keep things clean in the email, message, or notification they send to you. They’ll want you to first click and then try to hijack your process flow along the way. Hasty mistakes like an outdated logo can save you possible pain from a cyber attack down the road. This one is a phish!

Get a curated briefing of the week's biggest cyber news every Friday.

Turn your employees into a human firewall with our innovative Security Awareness Training.
Our e-learning modules take the boring out of security training.
Intelligence and Insights

Aligning Your Incident Response Plan with NIST SP 800-61 Rev. 3

CEO Checklist: How To Know If Your Organization Is Cyber Secure