Test Your Security Awareness
The images displayed below are a combination of phishing and real emails. Spot which ones are real and which ones are phony:
Spoiler Alert: Answers are below.
Answer: Image 2 is the only phishing email. The rest are all real. Let’s take a look.
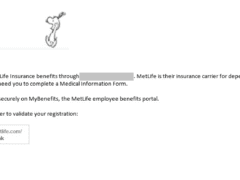
Image 1 details: This looks like an email sent to an employee who has pre-registered a dependent spouse. The URL in the email points to the real MetLife domain. Nothing really stands out as phishy. Looks legit.
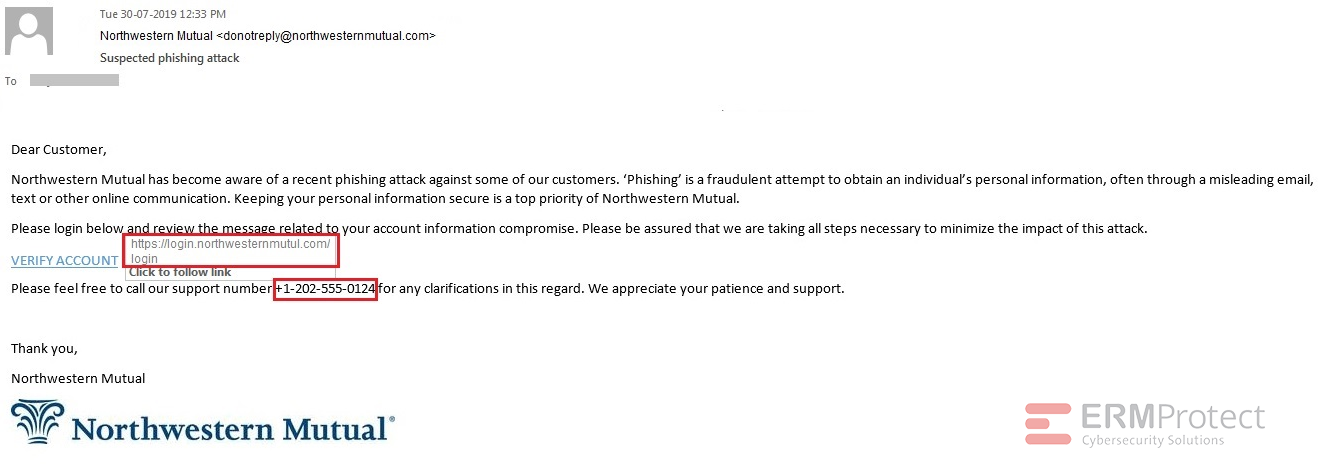
Image 2 details: The “from” address actually shows the real domain. But then it is possible to “spoof” a real domain when sending an email. Take a closer look at the URL though. It points to “northwesternmutul.com”. Notice the missing “a” in “mutual”? That was tricky and could be easily missed. There’s one other red flag as well. That support number mentioned in the email is a fake. It isn’t an official or published number of Northwestern Mutual. Remember, if you’re planning to call a company based on an email you received that you suspect is a phishing email, go to the company’s website and call their official number that’s published on their website.
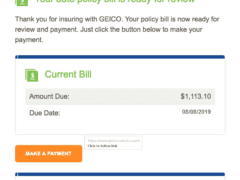
Image 3 details: This looks like an invoice from GEICO. The link points to the legitimate geico.com domain. Nothing seems amiss. It’s a good idea, though, to keep your guard up even after you click through and land at the GEICO site. Whenever there’s a payment involved and there are links, always stay cautious.
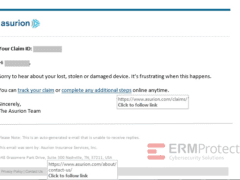
Image 4 details: This looks like an email from Asurion to a customer. The link-checks pass our requirements. Nothing otherwise phishy about the email that stands out either. This one looks OK.
Improve Your Cybersecurity with ERMProtect
No matter how much an organization improves its technical defenses, employees can fall victim to phishing attacks and other hacker lures. ERMProtect™ arms employees with the tools and security awareness they need to protect themselves and their organizations from cyber attacks. To speak with an expert on our cybersecurity team please call (800) 259-9660 or click here to schedule a free demo.

Turn your employees into a human firewall with our innovative Security Awareness Training.
Our e-learning modules take the boring out of security training.

Get a curated briefing of the week's biggest cyber news every Friday.
Intelligence and Insights

Cybersecurity Blind Spot: Why Physical Security Is Now the Easiest Way In

Red, Blue, & Purple Teaming: Unified Strategy Organizations Can’t Ignore