Test Your Security Awareness
The images displayed below are a combination of phishing and real websites. Spot which ones are real and which ones are phony:
Spoiler Alert: Answers are below.
Answer: Images 1 and 4 are real. The rest are phishes. Let’s take a look.
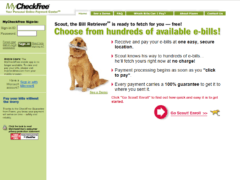
Image 1 details: This is the actual website of MyCheckfree.com. Nothing stands out as phishy.
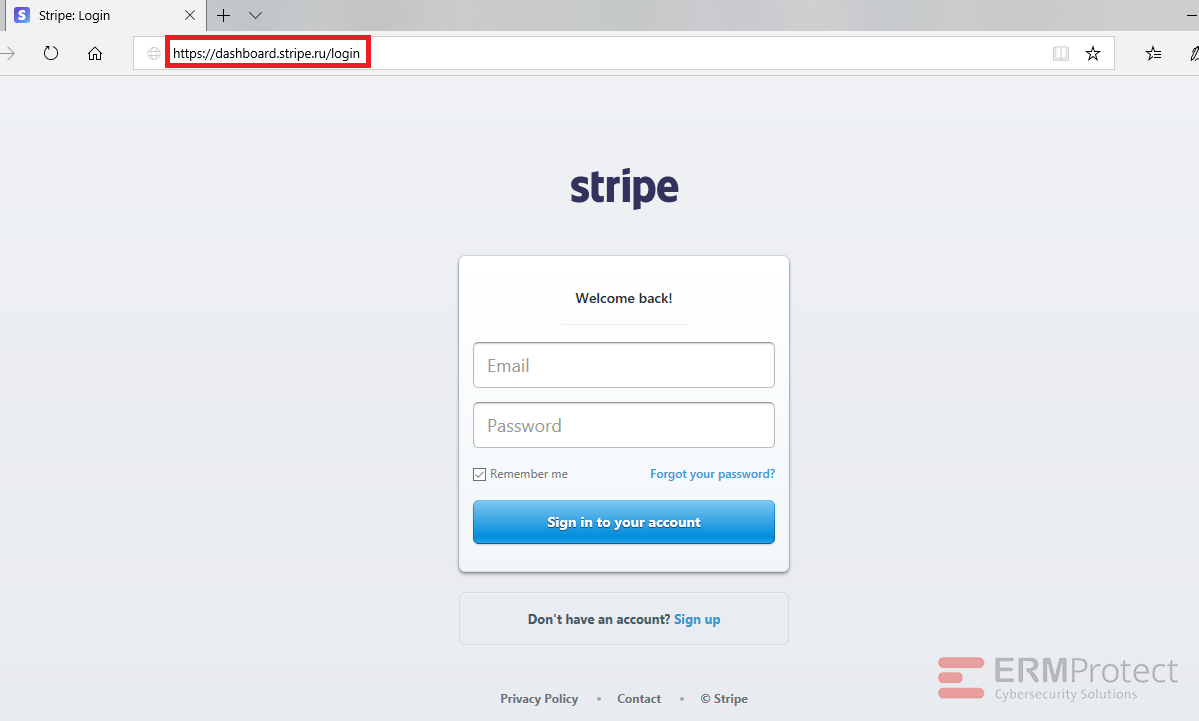
Image 2 details: The biggest and the only giveaway is the phony domain in the link. The real domain is “dashboard.stripe.com” but this one says “dashboard.stripe.ru.” It’s important to stay alert for signs like these.
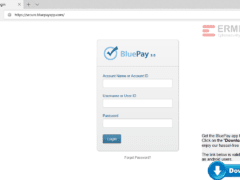
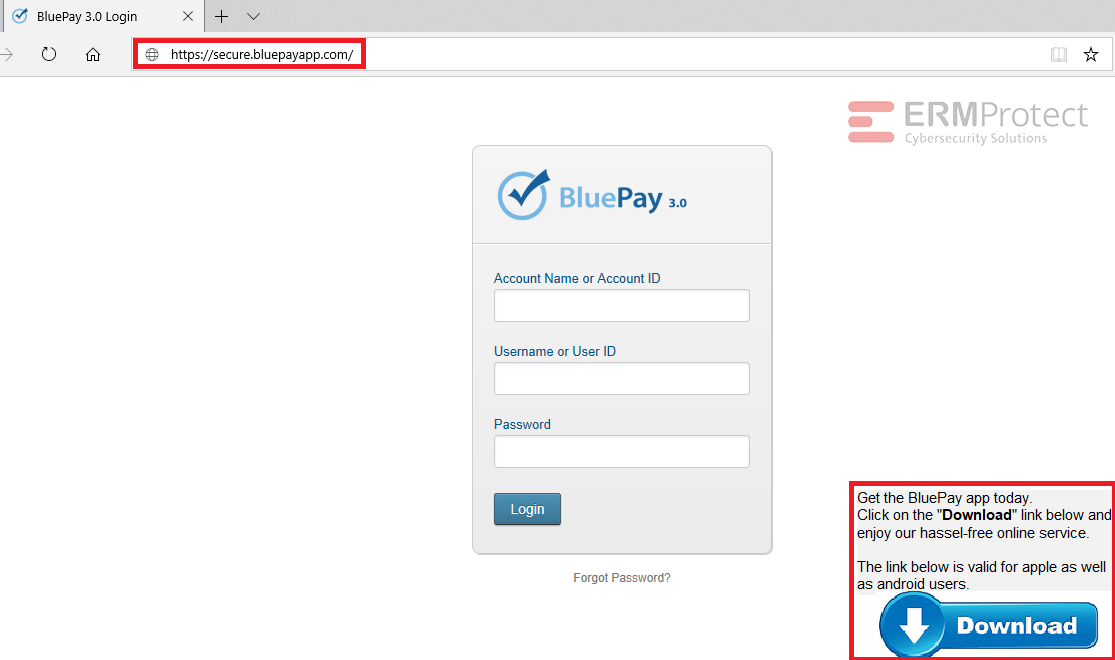
Image 3 details: The actual domain of BluePay is “bluepay.com.” The attacker has tried to pull a fast one here with “bluepayapp.com.” Also, that banner at the side might have looked a bit odd and out-of-place to you, and you’re right if you thought so. The actual BluePay site doesn’t have that banner.
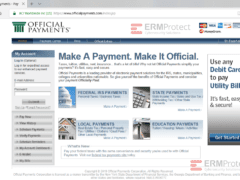
Image 4 details: This one is legit. It’s the actual Official Payments site.
Intelligence and Insights

Aligning Your Incident Response Plan with NIST SP 800-61 Rev. 3

CEO Checklist: How To Know If Your Organization Is Cyber Secure