PCI DSS 4.0.1 and New Principle of Least Privilege Requirements: PCI Compliance Services To Strengthen Cybersecurity
By Rey LeClerc Sveinsson, PhD
The latest iteration of the Payment Card Industry Data Security Standard (PCI DSS), version 4.0.1, introduces enhanced security requirements to protect sensitive payment card data. Among its critical updates, the standard emphasizes the Principle of Least Privilege (PoLP) in risk assessments, ensuring that only authorized personnel have access to critical systems and information.
These changes significantly impact businesses, particularly those seeking PCI compliance certification or leveraging penetration testing services to safeguard their digital infrastructure.
This article explores how PCI DSS 4.0.1 enhances IT risk assessment, cybersecurity risk assessment, and penetration testing solutions, while also providing guidance on implementing the Principle of Least Privilege to utilize PCI compliance services to strengthen cybersecurity.
What is the Principle of Least Privilege (PoLP)?
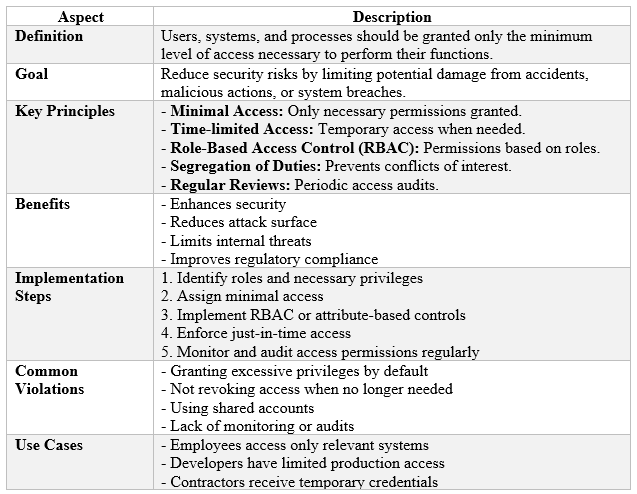
The Principle of Least Privilege dictates that individuals, processes, and systems should be granted the minimum level of access required to perform their designated functions. By enforcing IT security risk assessment controls, businesses can significantly reduce their attack surface, preventing unauthorized access and mitigating potential security breaches.
Key Changes in PCI DSS 4.0.1: Expanding Least Privilege with PCI Compliance Services
The latest PCI DSS update expands PoLP beyond payment environments, ensuring organizations implement stricter access controls across all system components. This shift enhances compliance with NIST, HIPAA, GLBA, and FFIEC risk assessment frameworks, aligning cybersecurity practices with global standards.
New PoLP Requirements in PCI DSS 4.0.1
1. Requirement 7: Strengthening Access Controls
Under PCI DSS 4.0.1, businesses must establish stringent access control systems to protect sensitive financial data and system components. This requirement ensures that only authorized individuals, whose job roles necessitate such access, can interact with payment systems and cardholder data. Organizations must conduct regular risk assessments to validate user permissions, preventing unauthorized access and insider threats.
For example, an accounts payable clerk should not have administrative privileges over transaction databases. Similarly, customer service representatives should only be able to access the data necessary to perform their tasks. Implementing Privileged Access Management (PAM) solutions allows organizations to automate permission controls, ensuring that employees do not have excessive access to sensitive data.
Additionally, businesses should establish a zero-trust security model, where users must verify their identity before being granted access, even if they are inside the corporate network.
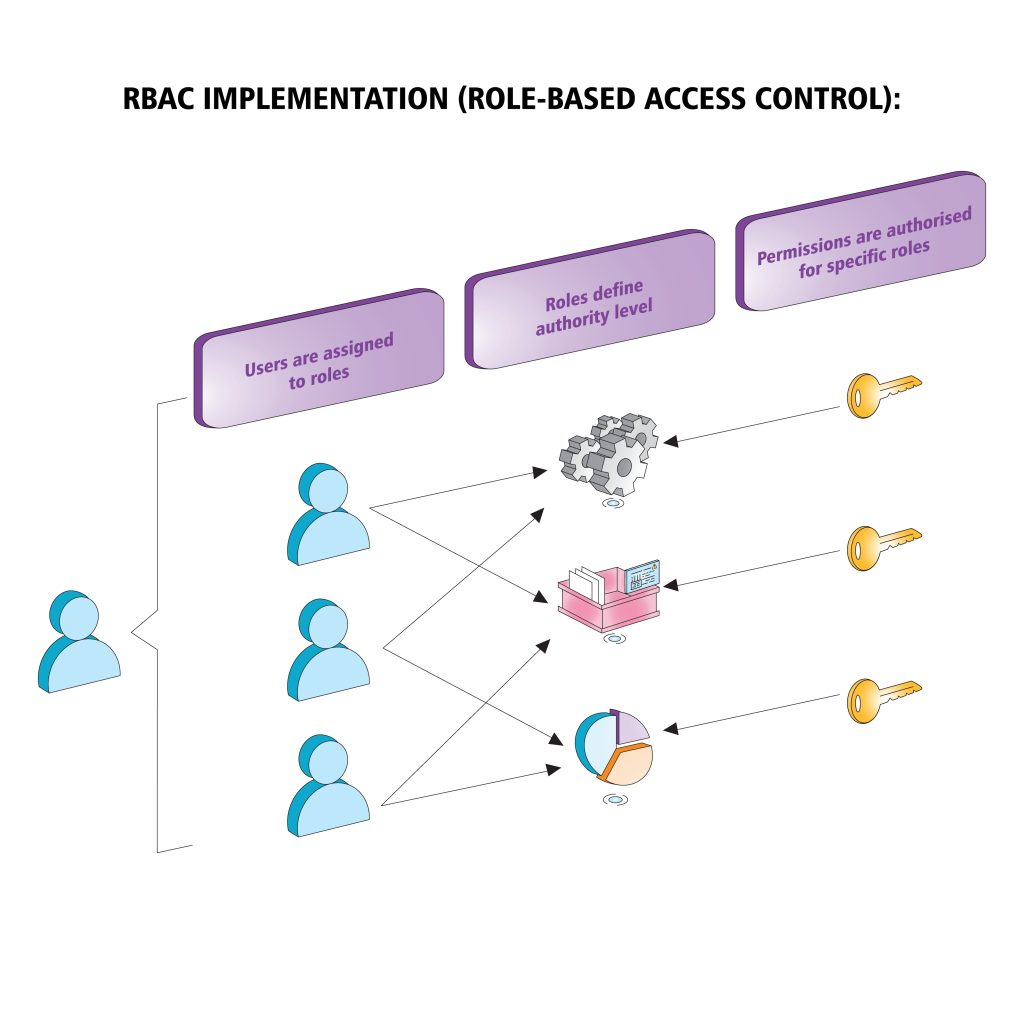
2. Requirement 7.2: Implementing Role-Based Access Control (RBAC)
The PCI Security Standards Council mandates Role-Based Access Control (RBAC) as a best practice for managing user permissions. This requirement ensures that access rights are assigned based on job functions and that permissions align with business needs. Organizations must enforce a default deny policy unless explicit approval is granted, ensuring that employees and third-party vendors do not retain unnecessary privileges.
A real-world example of RBAC implementation is within financial institutions, where tellers may have access to account information but are restricted from altering security settings. Similarly, IT administrators may have full system access but cannot process financial transactions. Frequent IT risk assessment reviews are necessary to detect privilege creep, where users accumulate unnecessary permissions over time.
Organizations can utilize Identity and Access Management (IAM) systems to streamline user role assignments, ensuring that former employees or transferred personnel do not retain inappropriate access.
3. Requirement 7.2.5: Least Privilege for Application and System Accounts
PCI DSS 4.0.1 extends PoLP to non-human accounts, including application and system accounts that often have elevated privileges. If not properly managed, these accounts can become a security liability, as attackers may exploit them to gain unauthorized access to sensitive systems.
Organizations must implement RBAC for system accounts, ensuring that applications and services only receive the minimum permission required to function.
A practical example includes restricting an automated transaction processing system to only execute payment transactions without having administrative control over database configurations. Businesses should establish baseline configurations to prevent excessive permissions and utilize Configuration Management Tools such as Ansible, Puppet, or Microsoft Group Policy to enforce these settings consistently.
Additionally, integrating automated IAM tools enables real-time monitoring and management of system accounts.
For instance, an IAM solution can detect an application attempting to access customer payment data when it should only process refunds, triggering an alert for immediate investigation. Organizations should also implement Just-In-Time (JIT) Access Controls, granting temporary permissions when needed and revoking them immediately after the task is completed to minimize security risks.
Ensuring Compliance Through Risk Assessments and Testing
To comply with PCI DSS 4.0.1, organizations must integrate Risk Assessment services and penetration testing solutions into their security framework. Here’s how:
- Cybersecurity Risk Assessment: Proactive Compliance Measures
Regular cyber security risk assessments help businesses identify vulnerabilities before attackers exploit them. A structured NIST risk assessment or FACTA risk assessment can uncover security gaps in access control mechanisms.
- Penetration Testing: Evaluating System Resilience
Engaging penetration testing companies helps verify compliance and security effectiveness. Key services include:
-
- Red team penetration testing: Simulating real-world attacks to test PoLP enforcement.
- PCI DSS penetration testing: Ensuring networks and applications comply with PCI DSS.
- Penetration testing reports: Documenting security findings for auditors and regulators.
- Digital Forensics and Incident Response: Managing Breaches
Even with stringent controls, credit card breaches can still occur. Partnering with digital forensics companies ensures a swift response by:
- Conducting incident response services to mitigate threats.
- Performing digital forensics investigations to trace and remediate breaches.
- Offering data breach response solutions to comply with PCI DSS and regulatory obligations.
Best Practices for Implementing the Principle of Least Privilege
To streamline PoLP adoption and maintain PCI DSS certification, organizations should follow these best practices:
- Automate Access Reviews
Organizations should deploy Identity and Access Management (IAM) and Privileged Access Management (PAM) solutions to continuously monitor and enforce access controls. These tools can automatically detect excessive permissions, streamline IT security risk assessment workflows, and reduce human error.
A recommended approach is to integrate IAM with HR systems to ensure access rights align with employee roles. Automated tools like SailPoint, Okta, and Microsoft Entra ID (formerly Azure AD) provide real-time monitoring, access requests, and de-provisioning capabilities. Organizations should schedule periodic access reviews, leveraging AI-driven analytics to flag anomalous permissions or dormant accounts.
- Conduct Regular Penetration Testing
Engaging penetration testing services ensures PoLP is enforced effectively. Penetration testing companies can simulate privilege escalation attacks to identify misconfigurations or access loopholes. Organizations should conduct both external and internal penetration tests to evaluate their access control resilience.
A structured approach includes quarterly red team penetration testing, where ethical hackers attempt to exploit excessive privileges. Regular PCI DSS penetration testing ensures compliance, and penetration testing reports provide actionable insights for security improvements.
- Utilize Just-In-Time (JIT) Access Controls
JIT access provides time-bound permissions, reducing standing privileges that could be misused. Instead of persistent administrative access, users obtain temporary, need-based privileges. Tools like BeyondTrust, CyberArk, and HashiCorp Vault facilitate JIT access, requiring multi-factor authentication (MFA) for elevated permissions.
- Implement Continuous Monitoring
Real-time monitoring is essential to detect unauthorized access attempts. SIEM (Security Information and Event Management) solutions like Splunk, IBM QRadar, and Microsoft Sentinel aggregate logs from network devices, applications, and IAM systems to identify suspicious activities.
User Behavior Analytics (UBA) tools can analyze access patterns and detect anomalies, such as an employee suddenly accessing sensitive financial data outside business hours. Automated alerts enable immediate incident response, reducing the risk of credential compromise.
- Train Employees on Access Control Policies
Technical controls alone are insufficient—human awareness plays a crucial role. Security teams should conduct ongoing training on access control policies, phishing risks, and cybersecurity incident response.
Organizations should implement phishing simulations, hands-on workshops, and role-specific training. Employees handling payment data should be trained on PCI compliance solutions, while IT staff must stay updated on PoLP best practices and emerging threats.
By adopting these best practices, organizations can enforce PoLP effectively, achieve PCI DSS compliance, and mitigate risks associated with excessive access privileges.
The Business Benefits of Enforcing Least Privilege
- Reduce Insider Threats
Minimizing unnecessary access significantly reduces the risk of credit card data breaches and insider threats. Employees and contractors should only have access to the data and systems required for their specific tasks, limiting the opportunities for malicious activity or accidental exposure of sensitive information. By enforcing Role-Based Access Control (RBAC) and Just-In-Time (JIT) Access Controls, organizations can prevent unauthorized privilege escalation. Insider threats remain one of the biggest risks to organizations, as even well-intentioned employees can make mistakes. By applying strict access restrictions and leveraging Privileged Access Management (PAM) solutions, companies can contain risks before they escalate.
- Strengthening PCI Compliance
Organizations striving for PCI DSS certification must adhere to stringent access control measures. Limiting access ensures compliance with PCI QSA companies and PCI compliance services while also reducing the likelihood of regulatory violations. Companies that proactively implement PoLP as part of their broader compliance strategy demonstrate their commitment to data security, making audits and assessments smoother.
Regular penetration testing services can verify whether PoLP is being enforced effectively by attempting privilege escalation attacks. Successful PCI DSS penetration testing ensures an organization remains compliant while mitigating security risks associated with excessive privileges.
- Enhance Operational Efficiency
A streamlined access control process improves both security and productivity. Employees no longer need to navigate overly complex permission structures, and IT teams spend less time managing ad-hoc access requests. Automated IAM tools can provision and de-provision user access dynamically, ensuring that permissions are adjusted as roles evolve. Companies that integrate IAM solutions with their HR systems can seamlessly grant appropriate permissions when employees join, change roles, or leave. This reduces administrative overhead while ensuring that IT security risk assessments continuously align with evolving business needs.
- Increase in Customer Trust
Trust is a critical component of cybersecurity, particularly for businesses handling payment data. Customers expect companies to take every precaution to protect their sensitive financial information. Organizations that implement PoLP effectively can communicate their commitment to security through third-party audits, compliance badges, and transparency about their security measures.
Demonstrating robust security practices—such as employing digital forensics services, cyber security incident response, and penetration testing reports—assures customers that their data is being handled responsibly. When a credit card breach occurs, organizations with strict access controls in place can respond faster, limit damage, and maintain consumer confidence.
By prioritizing Least Privilege, businesses not only enhance their security posture but also streamline operations, comply with industry standards, and build lasting trust with their customers and partners.
PCI Compliance Services Aimed to Achieve Robust Access Controls
The expansion of PoLP in PCI DSS 4.0.1 underscores the importance of stringent access controls in securing payment card data. By conducting IT risk assessments, engaging penetration testing companies, and leveraging digital forensics services, businesses can strengthen their cybersecurity posture while maintaining compliance.
For expert guidance on PCI compliance services, penetration testing services, and digital forensics investigations, contact ERMProtect today.
PCI Compliance Services with ERMProtect
ERMProtect provides tailored cybersecurity consulting services to help organizations achieve and maintain compliance with PCI DSS 4.0.1. Our team of experts offers comprehensive solutions designed to mitigate risks and strengthen security postures. We specialize in IT security risk assessments and PCI compliance services, ensuring that organizations proactively identify and address vulnerabilities in their security infrastructure.
In addition to risk assessments, we offer advanced penetration testing solutions, including penetration testing and red team penetration testing, to simulate real-world attacks and uncover potential weaknesses in access controls and system security. Our incident response services provide organizations with the expertise needed to effectively manage credit card breaches and execute data breach response strategies, ensuring minimal disruption and regulatory compliance.
For businesses aiming to streamline their PCI DSS certification, our PCI compliance services provide the necessary guidance and technical support to meet industry standards.
By working with ERMProtect, organizations can enhance their cybersecurity resilience, safeguard sensitive financial data, and stay ahead of emerging threats. Contact us today to learn how we can help protect your organization from evolving cybersecurity risks.
About the Author
Dr. Rey Leclerc Sveinsson is an expert in Privacy and Data Protection, Information Security, and Technology Governance, Risk & Compliance (IT GRC). He has developed information assurance programs for major organizations globally during his career as well as serving as a Consultant for ERMProtect. He has a PhD in Information Systems and multiple master’s degrees in the areas of privacy, information technology, and cybersecurity laws.
Intelligence and Insights

Cybersecurity Blind Spot: Why Physical Security Is Now the Easiest Way In

Red, Blue, & Purple Teaming: Unified Strategy Organizations Can’t Ignore