Count the Phish: Macy's Black Friday
The webpage below contains one or more red flags that makes it a phishing site. How many do you count?
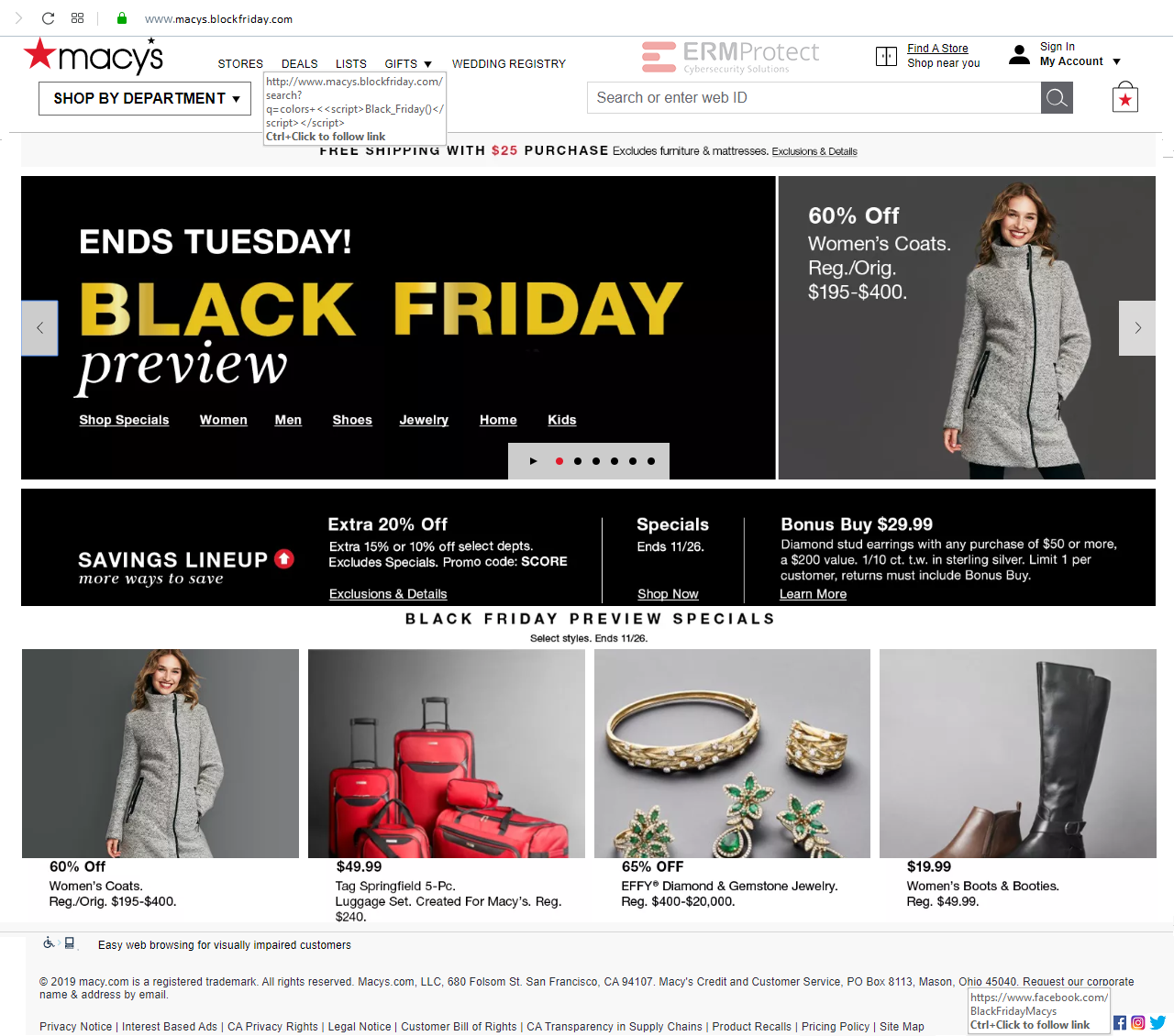
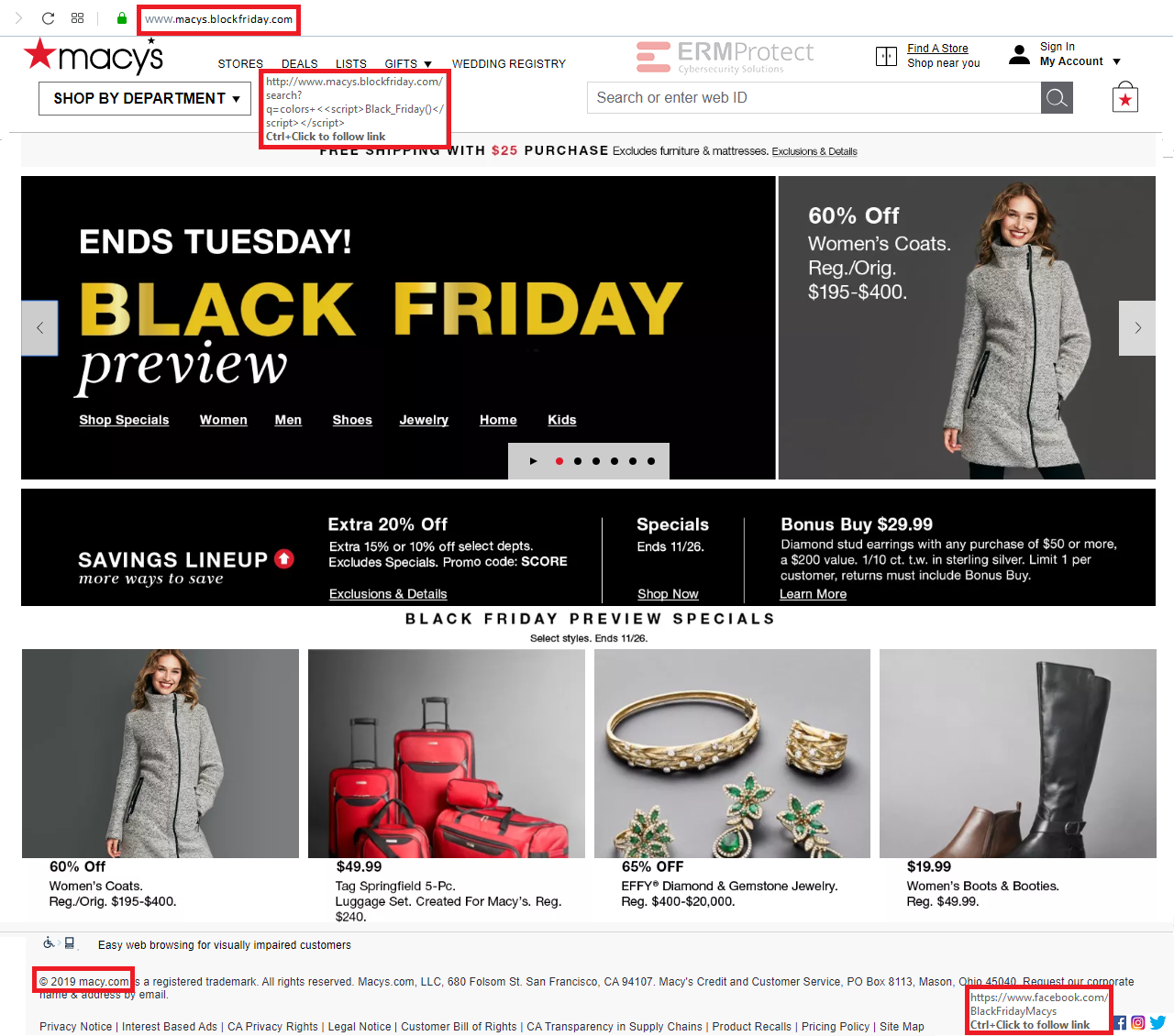
Answer: There are 4 red flags. Let’s take a look.
Phishing details:
- The first red flag is the phony URL. The actual “macys.com” domain is not the one being used here. Instead it’s “macys.blockfriday.com.” You could fall for it because you’re assuming that they may have set up a separate site specifically for Black Friday. But then why would a reputable organization like Macy’s go with a domain like “blockfriday.com”? This is clearly a domain setup by malicious phishers.
- The hyperlink for “DEALS” actually carries what is known as, a cross-site scripting attack. When the button is clicked, a new page will be loaded and this page will cause the browser to execute the script that you see in the URL called “Black_Friday().” This is most likely a malicious script. Plus, you can see again that the domain is still the phishy one from #1 above.
- The next red flag is the result of a sloppy hacker at work. If you see the copyright notice at the bottom of the page, it says “© 2019 macy.com” instead of “© 2019 macys.com.
- The last red flag is the Facebook hyperlink in the social media buttons at the bottom of the page. That’s not Macy’s Facebook page. Often times, hackers will try to lead you to other sites, including well-known social media sites, where they’ve planted malicious scripts or other such malicious ploys.

Get a curated briefing of the week's biggest cyber news every Friday.

Turn your employees into a human firewall with our innovative Security Awareness Training.
Our e-learning modules take the boring out of security training.
Intelligence and Insights

From Compliance to Advantage: Using PCI 4.0 Certification to Boost Business Value
In this comprehensive guide, we explain in simple terms every aspect of complying with the NIST Cybersecurity Framework 2.0 …

5 Major Cybersecurity Risks Banks and Financial Organizations Face
In this article, we outline some of the most common cybersecurity attacks that banks and financial institutions can be vulnerable to …

Follow These 4 Steps to Achieve PCI DSS Certification
For all organizations that process payment cards, the Payment Card Industry Data Security Standard (PCI-DSS) certification is high up the data security and compliance priority list …