Spot the Phishing Attempt - Cybersecurity Awareness
The images displayed below are a combination of phishing and real emails from Apple. Spot the phish! Click on the images to zoom in.
Spoiler Alert: Answers are below.
Answer: Email 1 and 4 are real emails. The others are phishes! Let’s take a look below…
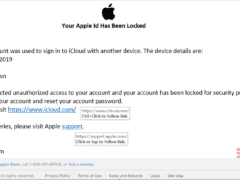
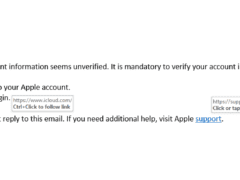
Image 1 details: The email passes our link checks, format checks, and grammar checks. Nothing seems amiss. Still, with cybersecurity awareness, it’s always a good idea to not click links at all and instead login to your Apple account via your browser.
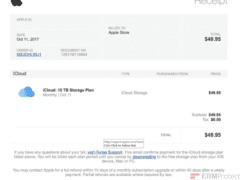
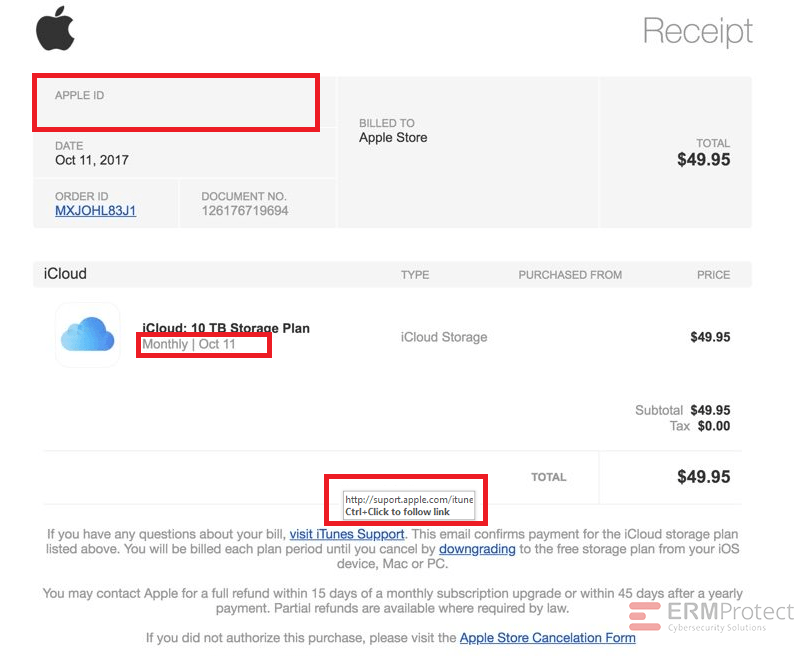
Image 2 details: The biggest giveaway is the missing Apple ID. A receipt from Apple always mentions your Apple ID. The date format is also abrupt as “October” has been shortened. That’s not typical of a professional organization. The link has typos – “suport” and “itune.” Even though the domain is correct, in phishing attacks, there are ways that hackers can redirect you. So, you always need to look for multiple red flags before arriving at a conclusion.
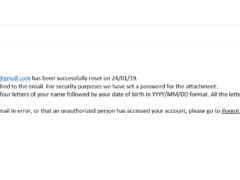
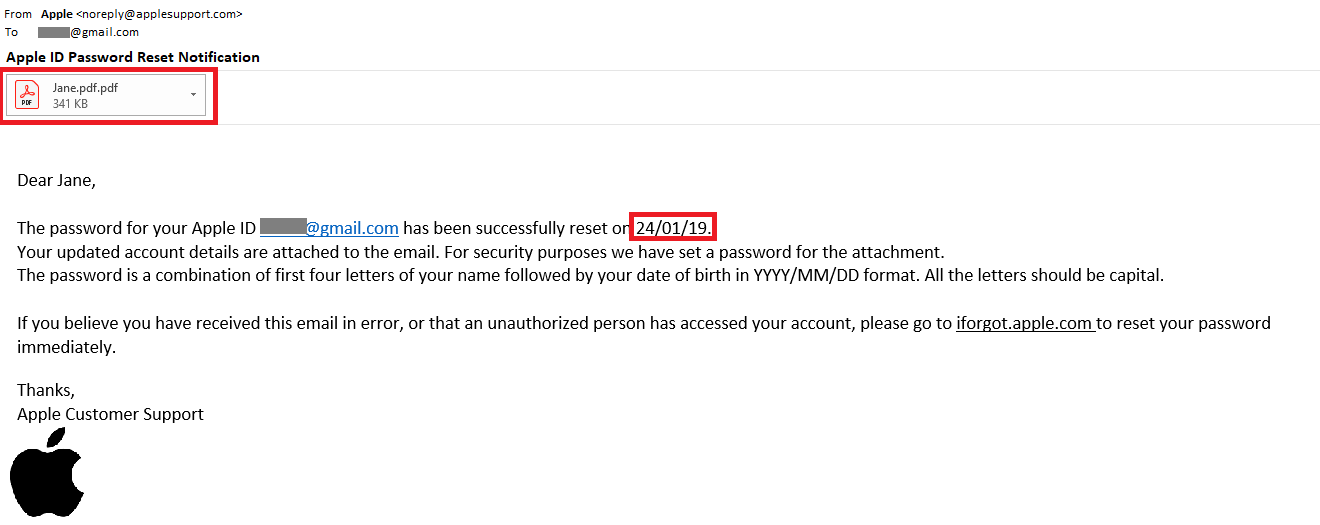
Image 3 details: First, the date format is a non-U.S. one. The sender’s email domain is not an apple.com domain. And then the attachment has a weird extension. What professional organization would send out an attachment that looks like that? You don’t really need to perform a link check on this one. Totally phishy!
Image 4 details: Nothing in the email looks phishy. The email passes link checks, format checks, and grammar checks, looks good from a cybersecurity aspect.

Get a curated briefing of the week's biggest cyber news every Friday.

Turn your employees into a human firewall with our innovative Security Awareness Training.
Our e-learning modules take the boring out of security training.
Intelligence and Insights

From Compliance to Advantage: Using PCI 4.0 Certification to Boost Business Value

5 Major Cybersecurity Risks Banks and Financial Organizations Face